Alarm
Last updated:2025-09-17 21:28:59
Alarm List
1. Log in to the CSC console, click Cloud API Exception Monitoring in the left navigation.
2. In the alarm list, view alarm content (leakage, abnormal calls) based on the alarm rule perspective, associate AK with abnormal call records, and provide permission policy configuration recommendations.
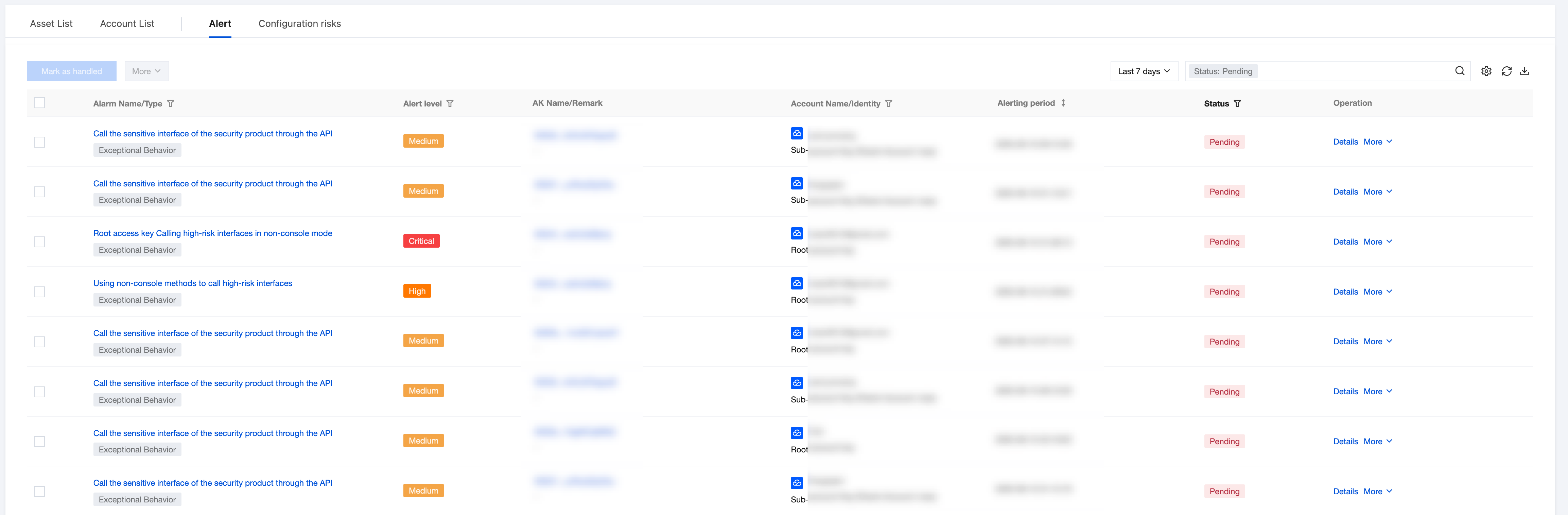
Field Name | Example | Description |
Alarm Name/Type | abnormal behavior leakage monitoring | Click to pull up the Alarm Details drawer. |
Alarm level | High High-risk Medium Risk Low-risk Note. Invalid | The alarm level is determined based on Tencent Cloud security practice. |
AK name/remark | AKID75XXX Department 1 AK | AK name and custom remarks. AK retains the first 6 and last 11 digits, with the middle omitted, supporting one-click copy; click to pull up the AK detail drawer. Remarks can be custom edited with no more than 20 characters. If empty, display "-". |
Account Name Identity | Account A Root Account/Sub-account (belonging to main account: Root Account B) | AK cloud service provider and account, if it is a sub-account show info belonging to main account. Hover over to view account ID and APPID; support filtering root account/sub-account. |
Alarm Time | 2025-01-12 18:00:00 | Alarm generation time. Format: YYYY-MM-DD HH:MM:SS. Support sorting. |
Processing Status | Unprocessed processed ignored | Show alarm handling status, manually done tag, processing status supports filtering. |
3. In the alarm list, select the desired alarm and click Details/more.
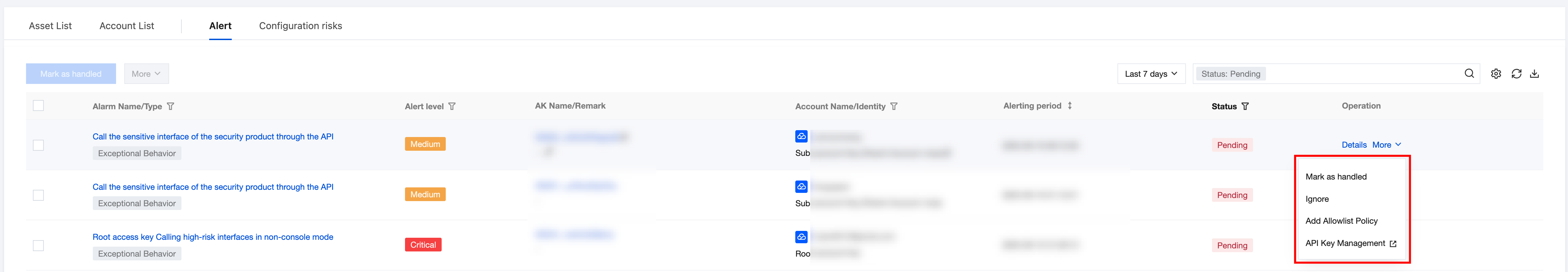
Operation Type | Description | |
Details | | Click to pull up the Alarm Details drawer. |
Others | tag disposal | Click post-processing and the status changes to "Processed". |
| marked as ignored | Click post-processing and the status changes to "Ignored". |
| Allowlist policy | Click to pull up the allowlist policy drawer and fill in the corresponding AK. |
| API Key Management | Click to navigate to Cloud Access Management > Access Keys > API Key Management. |
Rule Description
Monitor AK leakage and abnormal calls in real time. The monitoring includes three types: hacker tool/Cloud Manager/cos-browser identification, GitHub leakage (GitHub collaboration + IP check), and abnormal IP calls to sensitive APIs. Specific rules are listed in the table below.
Rule Name | Rule Description |
Root key calls a high-risk API | Root account access key calls a high-risk API. High-risk APIs cover 30+ interfaces across 20+ services such as cam, sts, tat, scf, tke, cdb, cvm, cbs. Example: cam.ListAccessKeys,cam.DeleteUser... |
Non-console calls to high-risk APIs | Call high-risk APIs via non-console methods (primarily obtaining via TencentCloud API through SDK). |
Unauthorized service invocation | Unauthorized service invocation via API call requires permission convergence for that account/role. |
Create a key | A new key is created. |
Permission escalation act | The user permission gets promoted by calling some APIs of sts and cam. |
Sensitive behavior during not normal time period | Perform sensitive operations such as resource deletion via console or API between 10 PM and 6 AM. |
New user calls a high-risk API | A created user called a high-risk API within 1 day. Need to pay attention. |
GitHub key confirmation request | Check whether the request originates from the egress IP of a GitHub callback. If hit, it means the ak exists in a GitHub public/private repository. |
Hacker tool detection | Check if the behavior of the same ak is similar to a hacker tool. |
Long-term inactive access keys with API calls | Inactive access keys never used in the past month have API calls. Pay attention. |
Invoke cloud API via cos browser | Call TencentCloud API via cos-browser. Attackers may use cos-browser to perform file downloads. Need to determine whether it is proper usage. |
Create Tencent Cloud resources through API | Create Tencent Cloud resources through TencentCloud API, such as Cloud Virtual Machine (CVM) and cloud database (CDB). |
Cloud Manager behavior | This part of calls comes from the Cloud Manager invocation source. Attention required. Cloud Manager is a multi-cloud management platform that visually manages cloud CVM, network, mirror and more. It may also be used by attackers. O&M personnel must check whether to use Cloud Manager. |
High-risk operations in Cloud Automation Tools | By calling some APIs of tat, directly execute commands on the machine. |
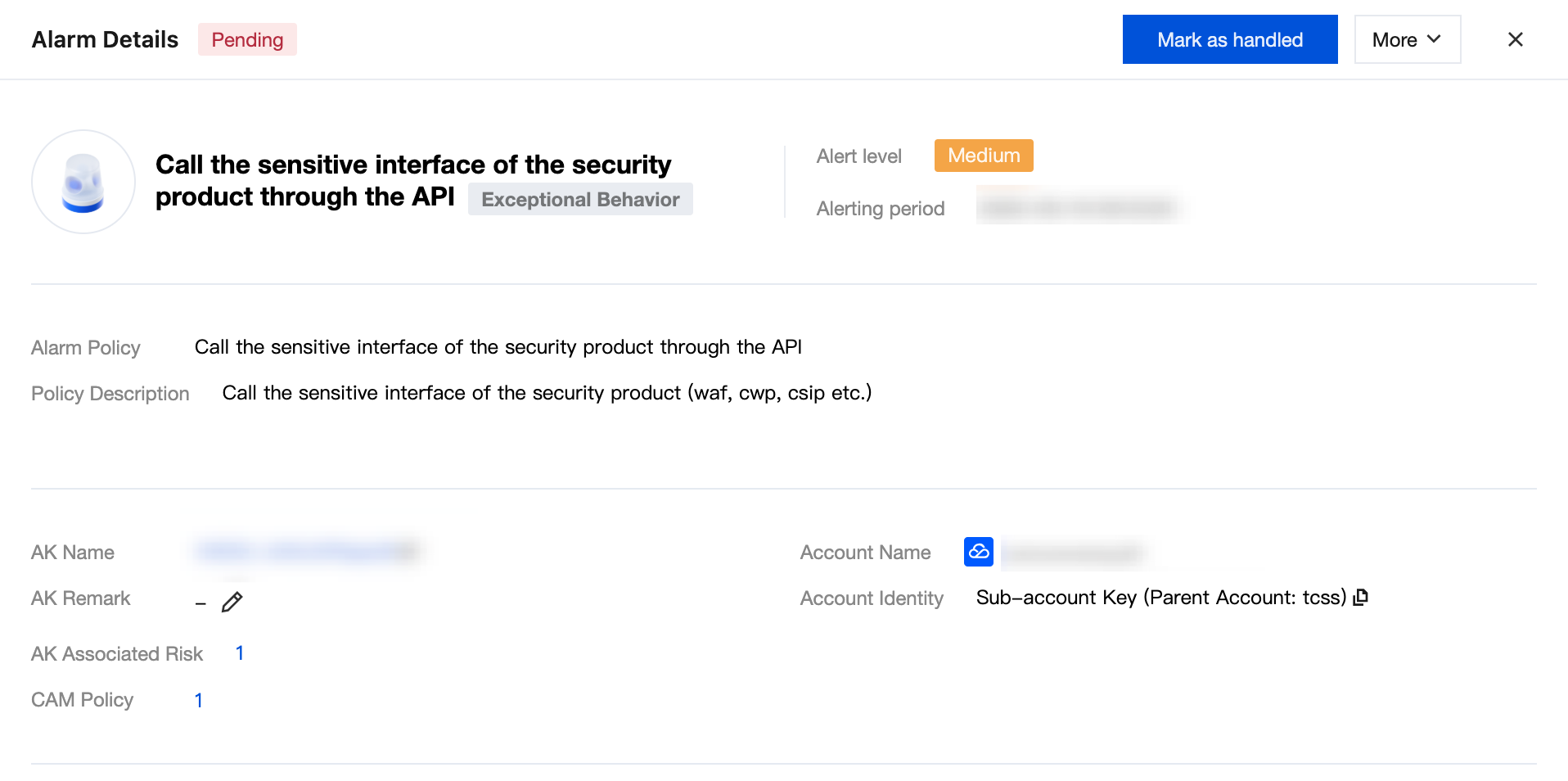
Alarm Details
1. In the alarm list, select the desired alarm and click Details.
2. On the alarm detail page, view alarm information and exception invocation records.
View alarm information, including alarm policy, policy description, AK name, AK remark, AK association risk, CAM policy, account name, and account identity.
View exception call records, including the IP address, IP type, calling method, service name, success or failure count, first/most recent call time, and related CAM policy.
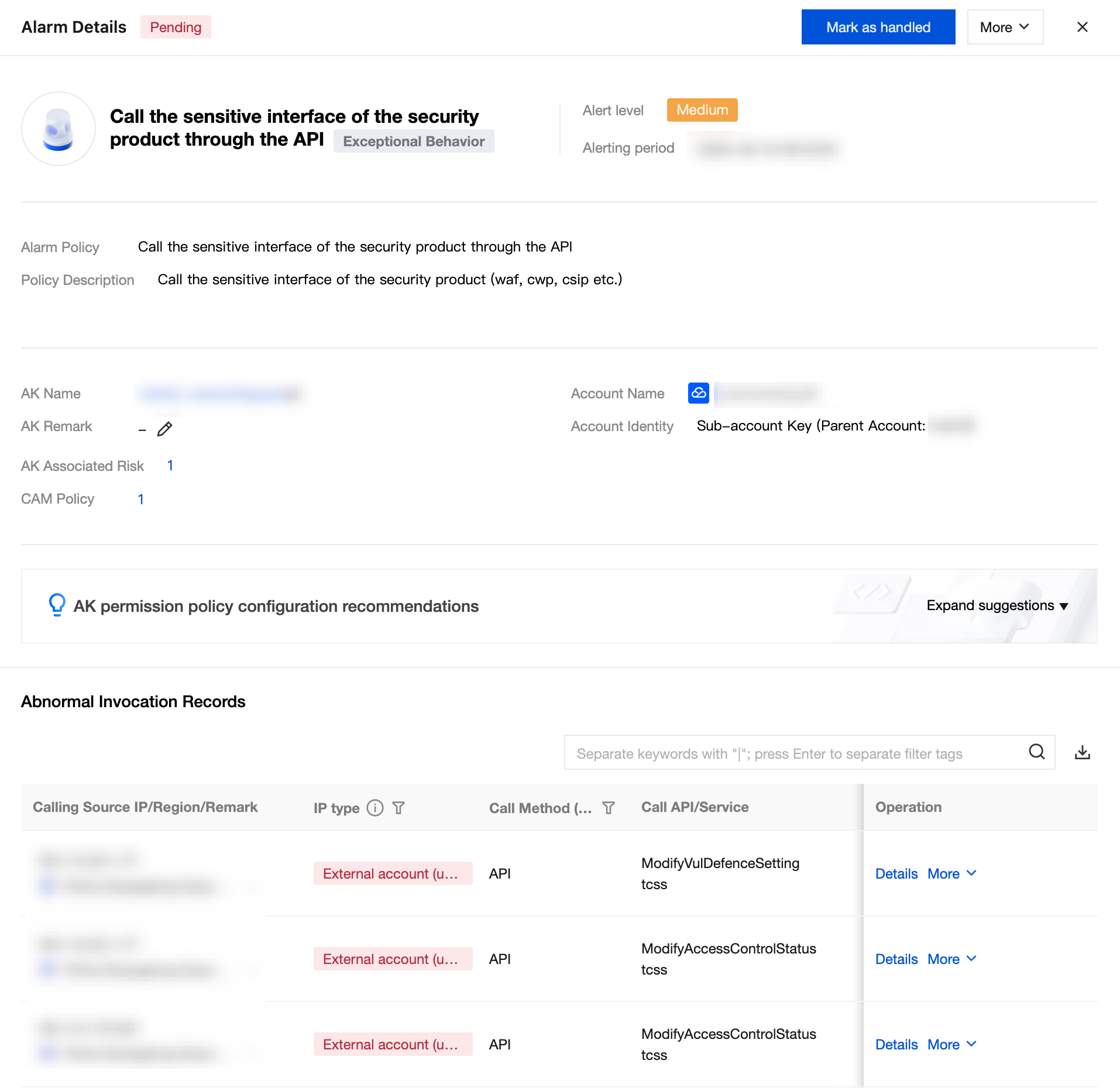
Field Name | Example | Description |
Source IP/Region/Remark | 1.1.1.1 China-Beijing | Department 1 AK | Source IP, region, and custom remarks. IP content supports one-click copy. Remarks can be custom edited with no more than 20 characters. If empty, display "-". |
IP type | within the account (with remark) within the account (no remark) outside the account (with remark) outside the account (no remark) LAN (with remark) LAN (no remark) | within the account (with remark): the source IP of calls identified in the CSC asset list, with remark. within the account (without remark): the source IP of calls detected in the CSC asset list, no remark. outside the account (with remark): IPs not within the account but with remark. outside the account (without remark): IPs not within the account and without remark. LAN (with remark): Local Area Network IP Address, with remark. LAN (without remark): Local Area Network IP Address, without remark. |
AK name/remark | AKID75XXX Department 1 AK | AK name and custom remarks. AK retains the first 6 and last 11 digits, with the middle omitted, supporting one-click copy; click to pull up the AK detail drawer. Remarks can be custom edited with no more than 20 characters. If empty, display "-". |
Calling Method | API Console | Access the service via API call or console operations. |
Call API/Service | DescribeAccountPrivileges cdb | API and its associated service. |
CAM Policy User (Role)/Policy | 1 username: xxx Policy: 1 | The number of CAM policies associated with this AK. Click the number to open the CAM policy details popup. Temporary key is displayed in an aggregated manner, so display users (role). |
Call status Number of invocations | Successful. (x times) Failed. (x times) | Call the AK successfully/failed state and count. |
First call time Most recent call time | 2025-01-01 18:00:00 2025-01-12 18:00:00 | First call time and most recent call time. Format: YYYY-MM-DD HH:MM:SS. Support sorting. |
IP asset (ID/name) | ins-xxx Machine 1 | Show AK asset. |
3. On the alarm detail page, select the required source IP for the call, and click Details/More.
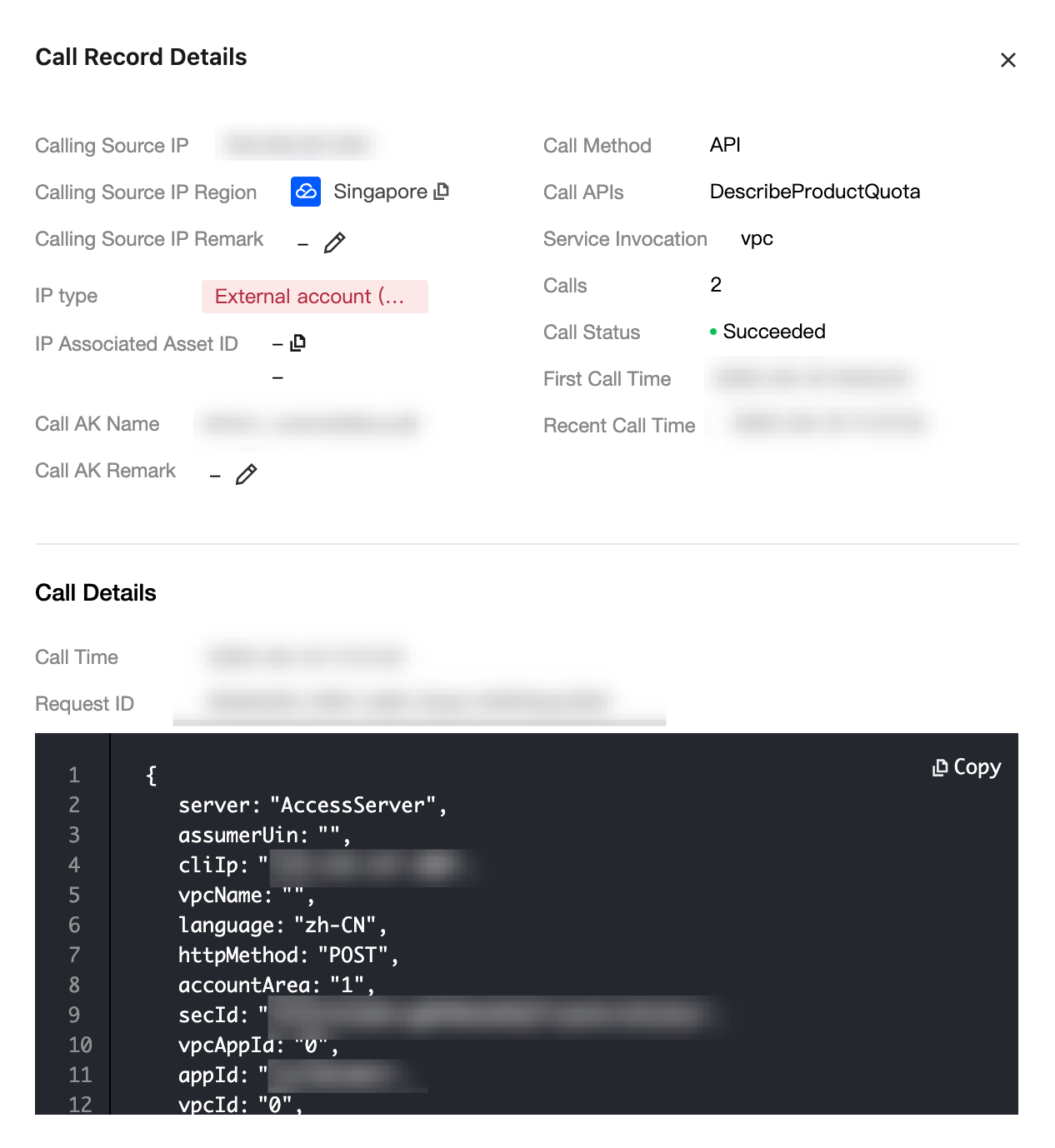
Details
Display call information, call details (including time, request ID, request body; supports pagination), and CAM policy details.
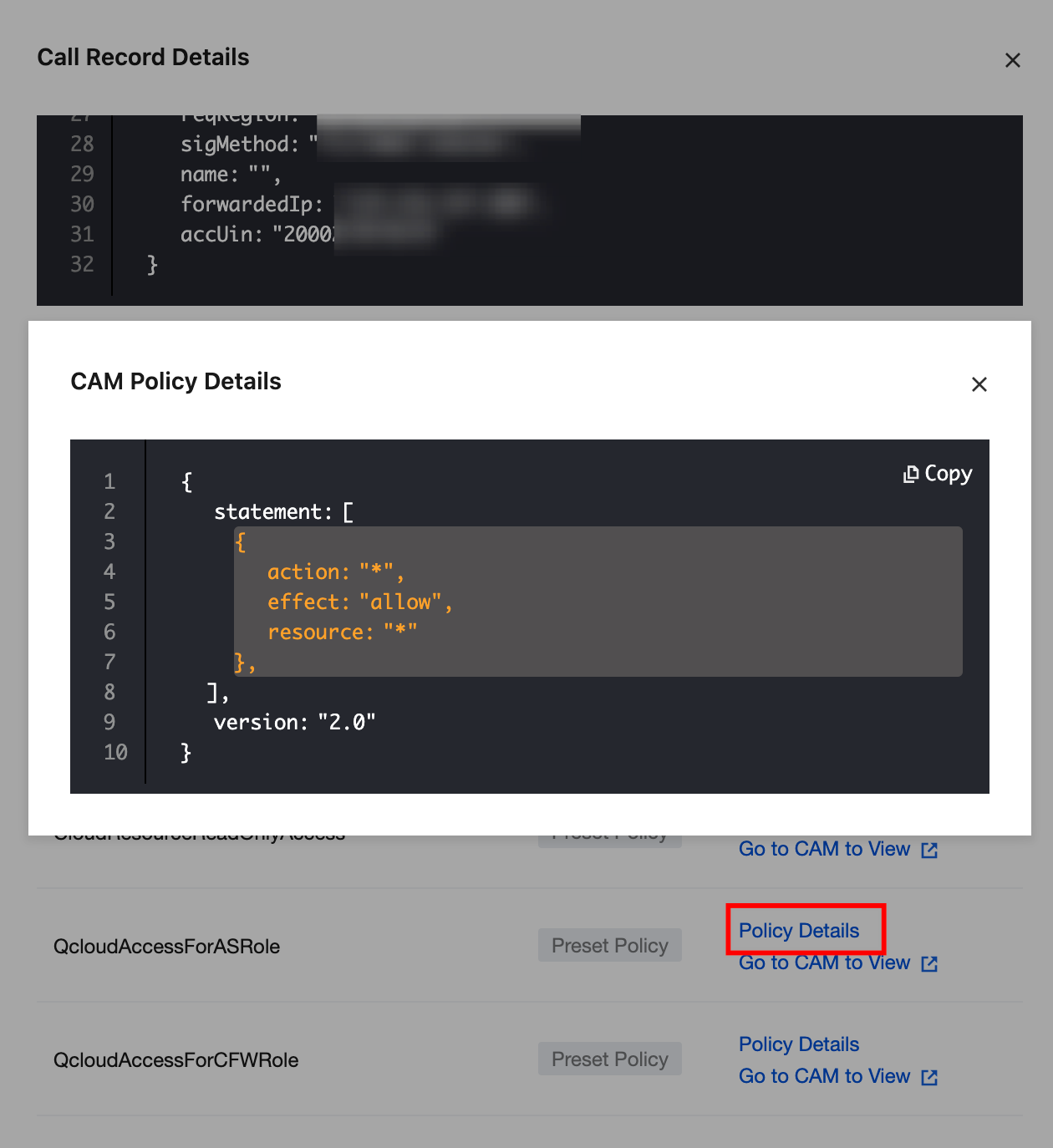
Click Policy Details to show the policy code (copying is supported). Click Go to CAM to navigate to Access Management > Policy > Specific Policy Details.
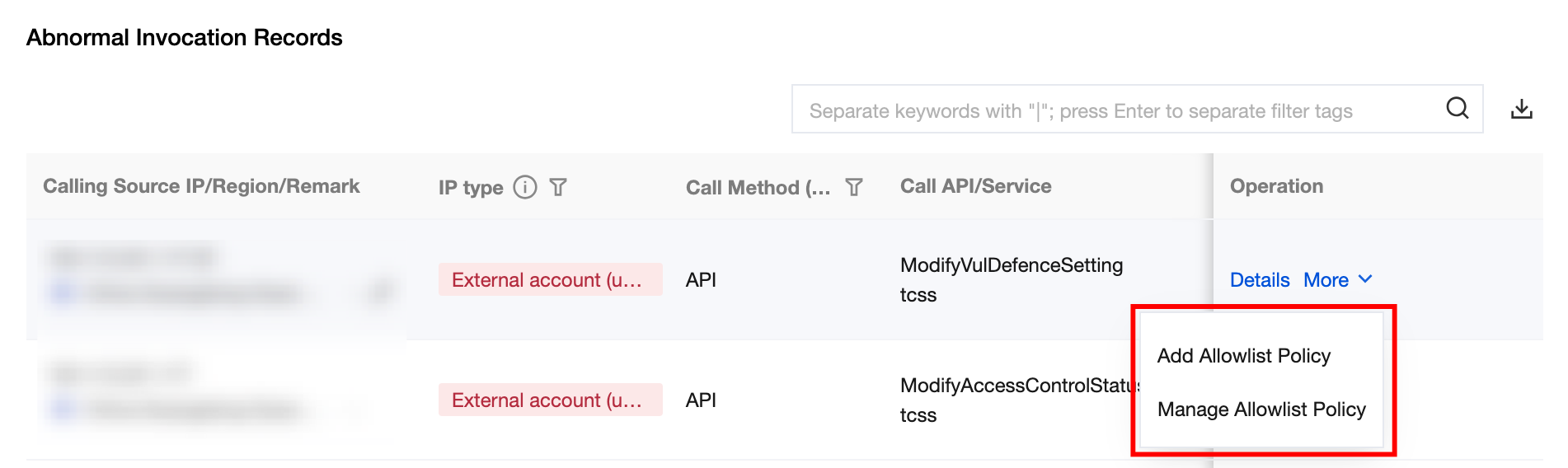
Others
Allowlist policy: Click to pull up the allowlist policy drawer, fill in the effective policy, corresponding IP, API call method, AK, API, response code. For filling instructions, please refer to policy management.
Manage allowlist policy: Click to pull up the policy management drawer and navigate to Policy Management > Allowlist Policy.
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No
Feedback

