Configuration Risks
Last updated:2025-09-17 21:28:59
By risk item
Risk List
1. Log in to the CSC console, click Cloud API Exception Monitoring in the left navigation.
2. In Configuration risks > By risk item, automated scanning of AK permission configuration is performed based on the risk item perspective to identify AKs with existing risks and directly display all affected specific account lists.
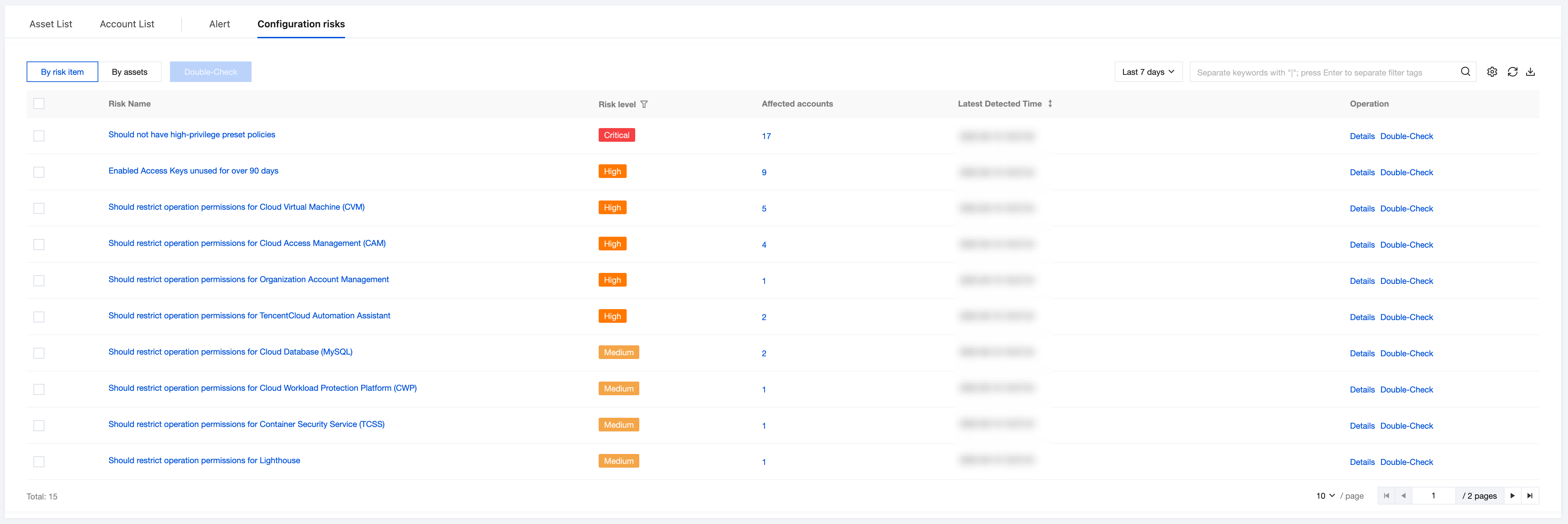
Field Name | Example | Description |
Risk name | Should not have high-privilege preset policies | Click to pull up the risk item details drawer. |
Risk Level | High High-risk Medium Risk Low-risk Note. | Risk level is assessed based on Tencent Cloud security practice. |
Affected account | 1 | Click the digit to open the risk item details drawer. |
latest detected time | 2025-01-12 18:00:00 | Risk detection time. Format: YYYY-MM-DD HH:MM:SS. support sorting |
3. In the risk item perspective list, select the desired risk and click Description/Recheck.
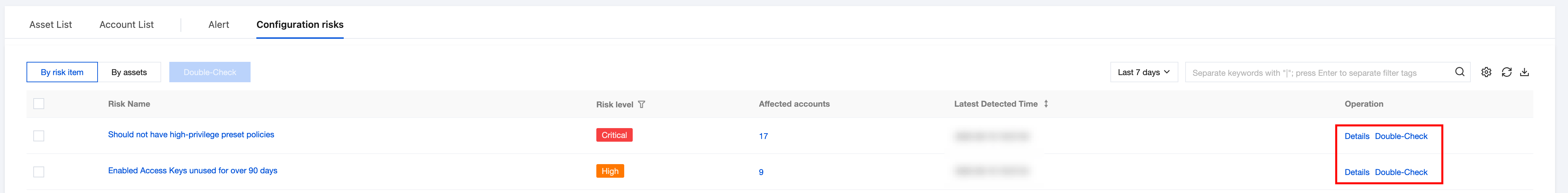
Operation Type | Description |
Details | Click to pull up the risk item details drawer, view the risk description and associated account info, and perform corresponding operations based on the account's current processing status. |
recheck | Click to recheck the rule. |
Risk Item Details
1. Log in to the CSC console, click Cloud API Exception Monitoring in the left navigation.
2. In Configuration risks > By risk item, select the required asset and click Details.
3. In the Risk Item Details page, view basic info, affected accounts, and configuration suggestions.
View risk item basic info.
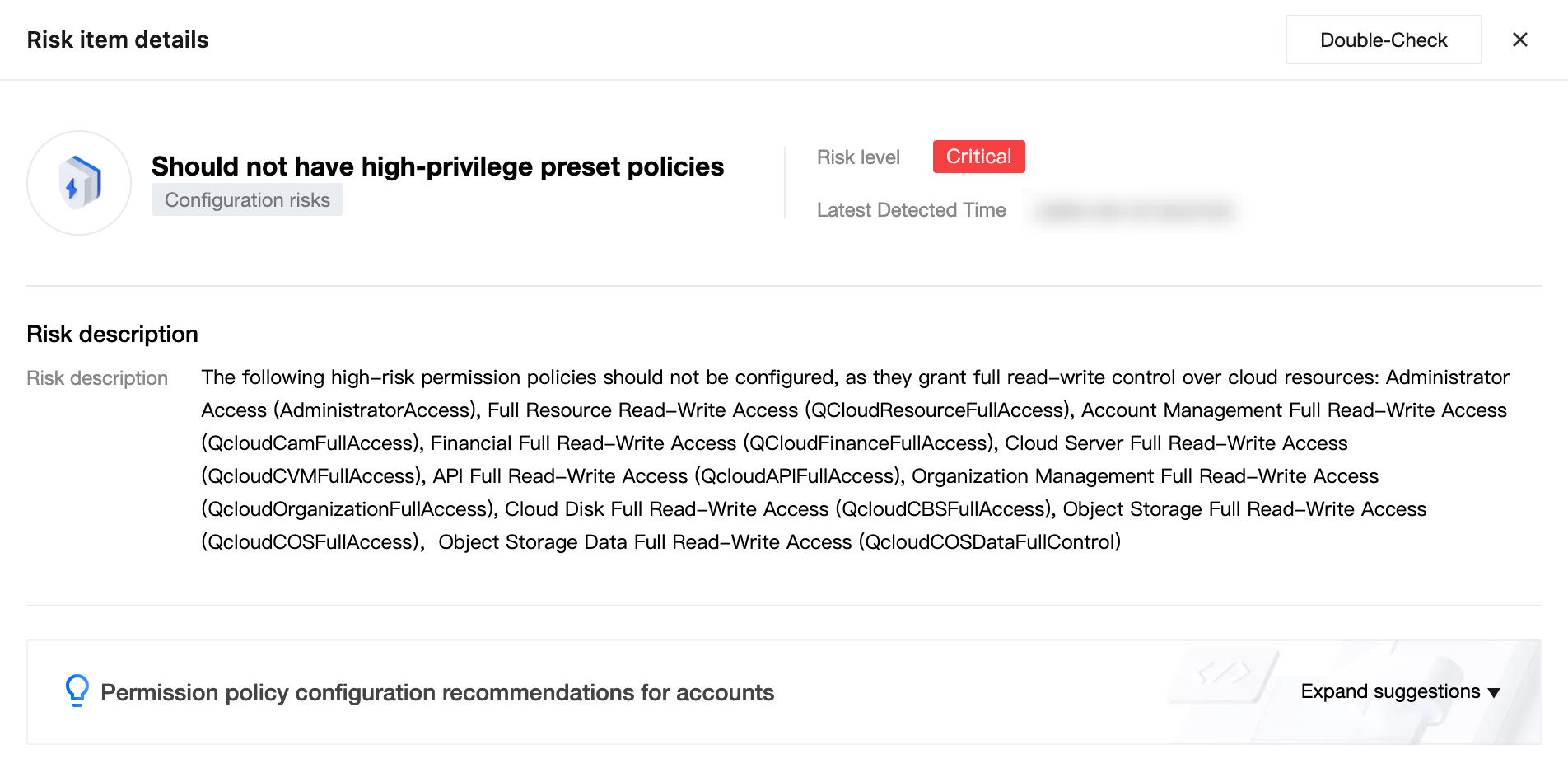
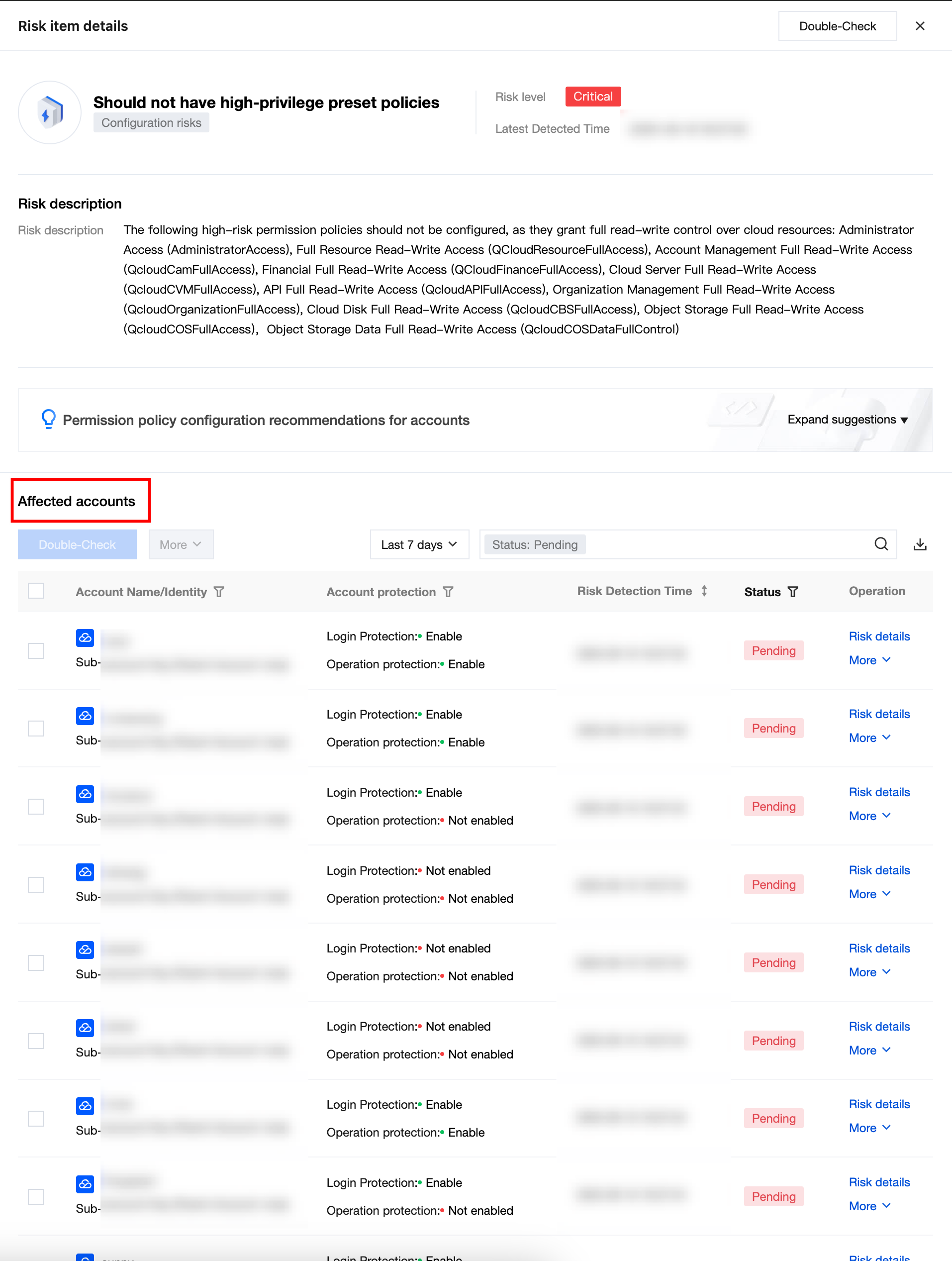
View the affected account list, by default showing accounts with unhandled risks.
Field Name | Example | Description |
Account Name/Identity | Account A Root account/Sub-account (Belonging to main account: Main account B) | AK belongs to the cloud service provider and account. If it is a sub-account, show root account information. Hover over to view account name, account ID and APPID. |
account protection | Login protection: Enable Operation protection: Enable | Show the account's login protection and operation protection security status activation. Support filtering enable all/partially enabled/not enabled. |
Risk detection time | 2025-01-12 18:00:00 | Risk detection time. Format: YYYY-MM-DD HH:MM:SS. support sorting |
Processing Status | unprocessed Converged ignored | Show risk processing status, manually done tag, processing status supports filtering. |
4. On the Risk Item Details > Affected account page, select the desired account and click Risk Details/More.
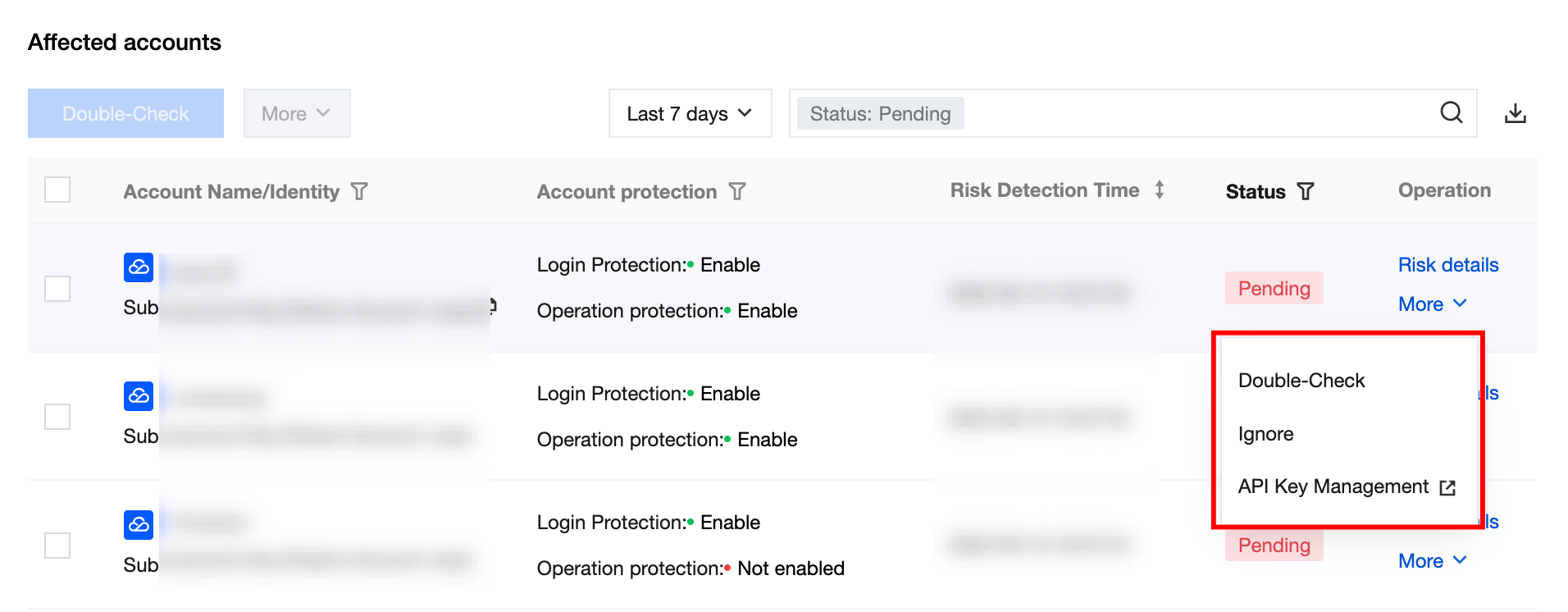
Operation Type | Description | |
risk details | | Click to pull up the risk details drawer to view the risk description and judgment evidence. |
Others | Detection | Click to recheck the rule. |
| marked as ignored | Click to change the processing status to "ignored". |
| API Key Management | Click to navigate to Cloud Access Management > Access Keys > API Key Management. |
Risk Details
1. On the Risk Item Details > Affected Account page, select the desired account and click Risk Details.
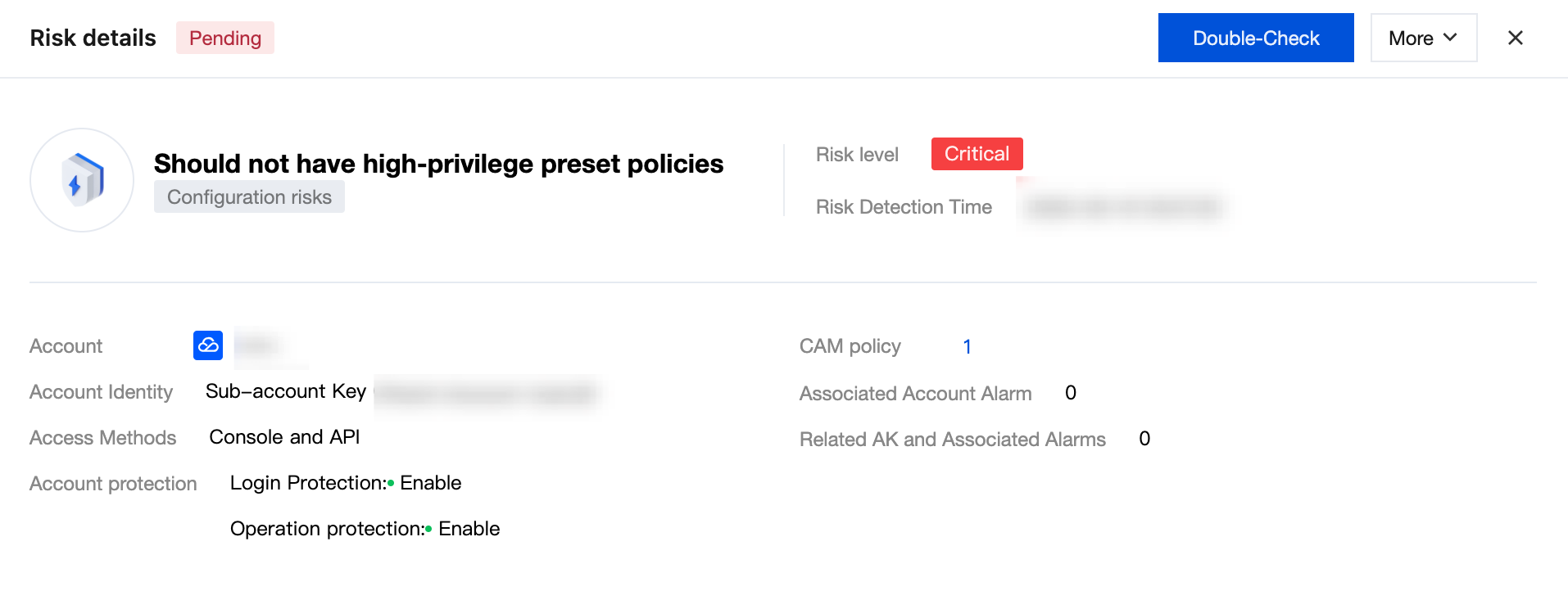
2. In the Risk Details page, view basic info, risk evidence and description, API call status, and configuration suggestions.
View basic risk info, including Account, account identity, access method, account protection, related CAM policy, associated account alarms, and related AK as well as associated alarms.
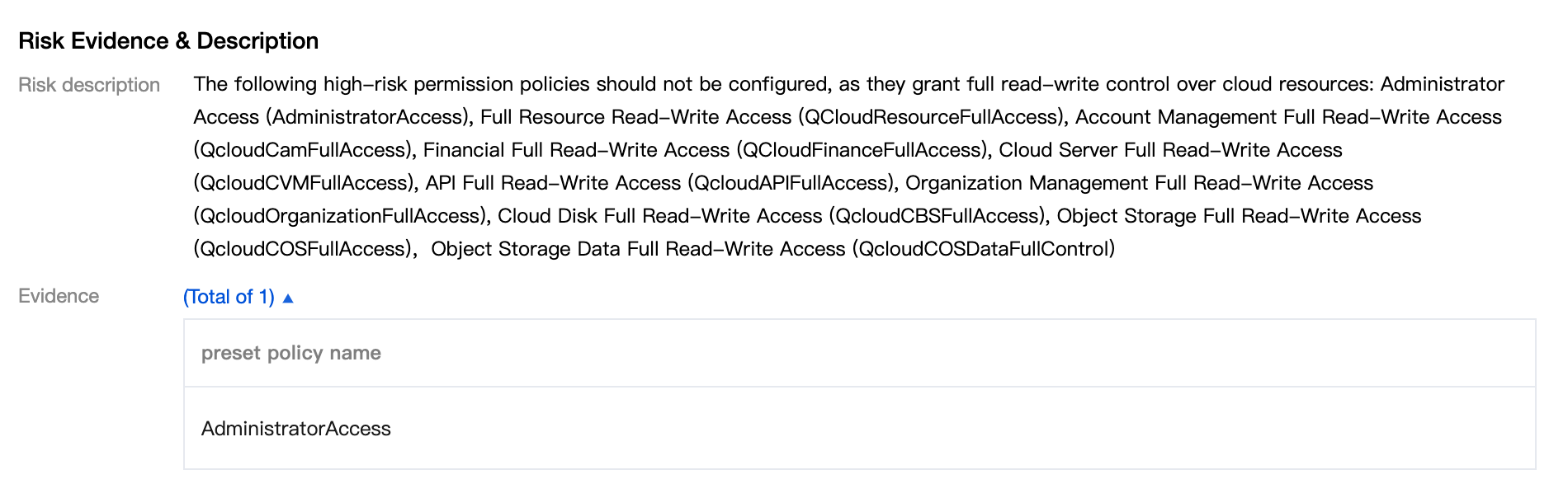
View risk description and evidence. The risk details include Policy Name, operation, resource, and request conditions. In addition, there are two types of risk evidence: AK name, creation time, last used time, and preset policy name.
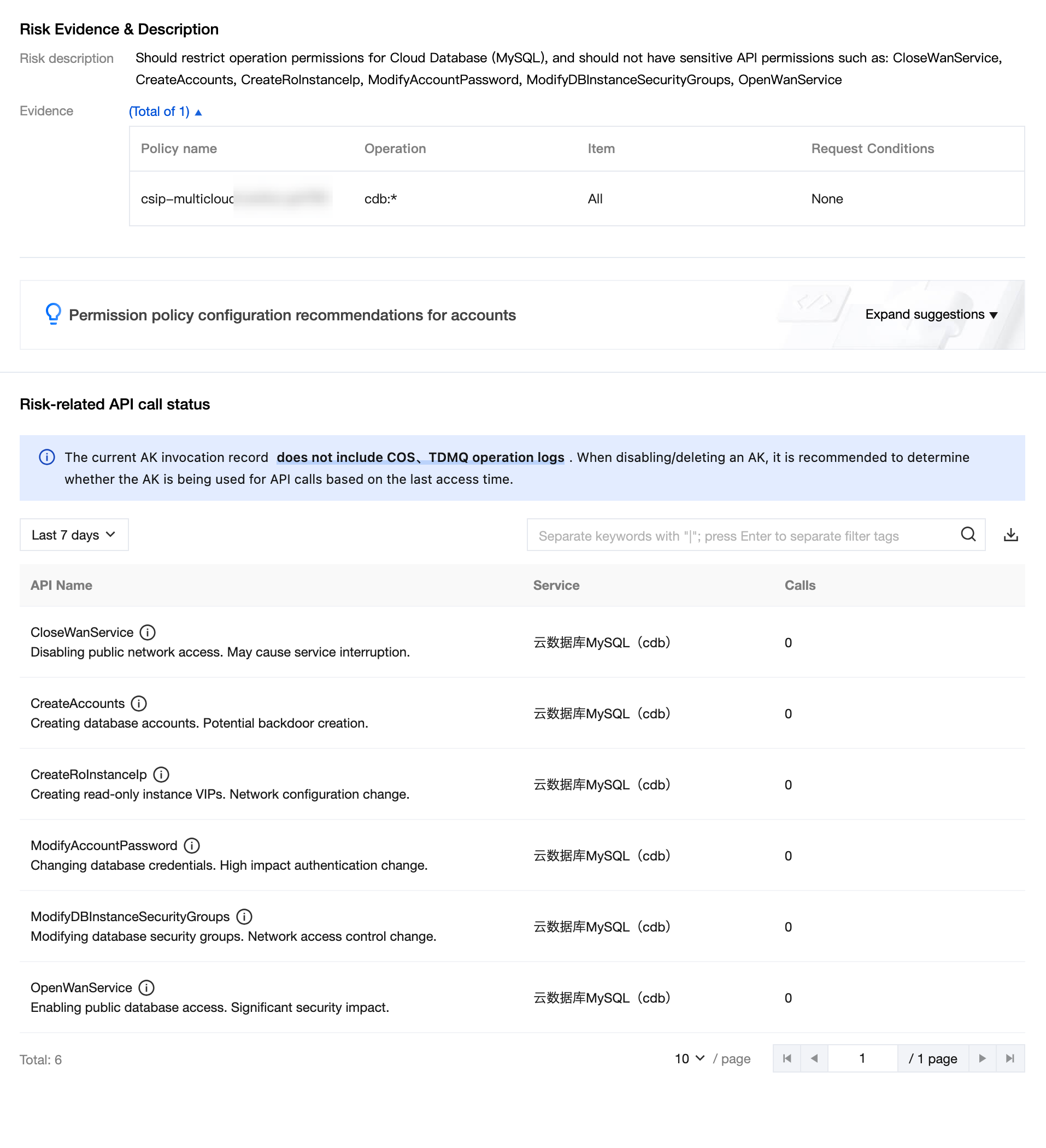
View API call status and configuration suggestions.
Field Name | Example | Description |
API Name | AddUser | The API name. Hover over the icon to display the API description in detail. |
Associated Service | Cloud Access Management (cam) | This API belongs to the product or service module. |
Call count | 1 | Call count measurement unit for this API. |
By assets
Risk List
1. Log in to the CSC console, click Cloud API Exception Monitoring in the left navigation.
2. In Configuration risks > By assets, automated scanning of AK permission configuration is performed based on the asset perspective to identify AKs with existing risks and clearly list each affected account corresponding to risky AKs.
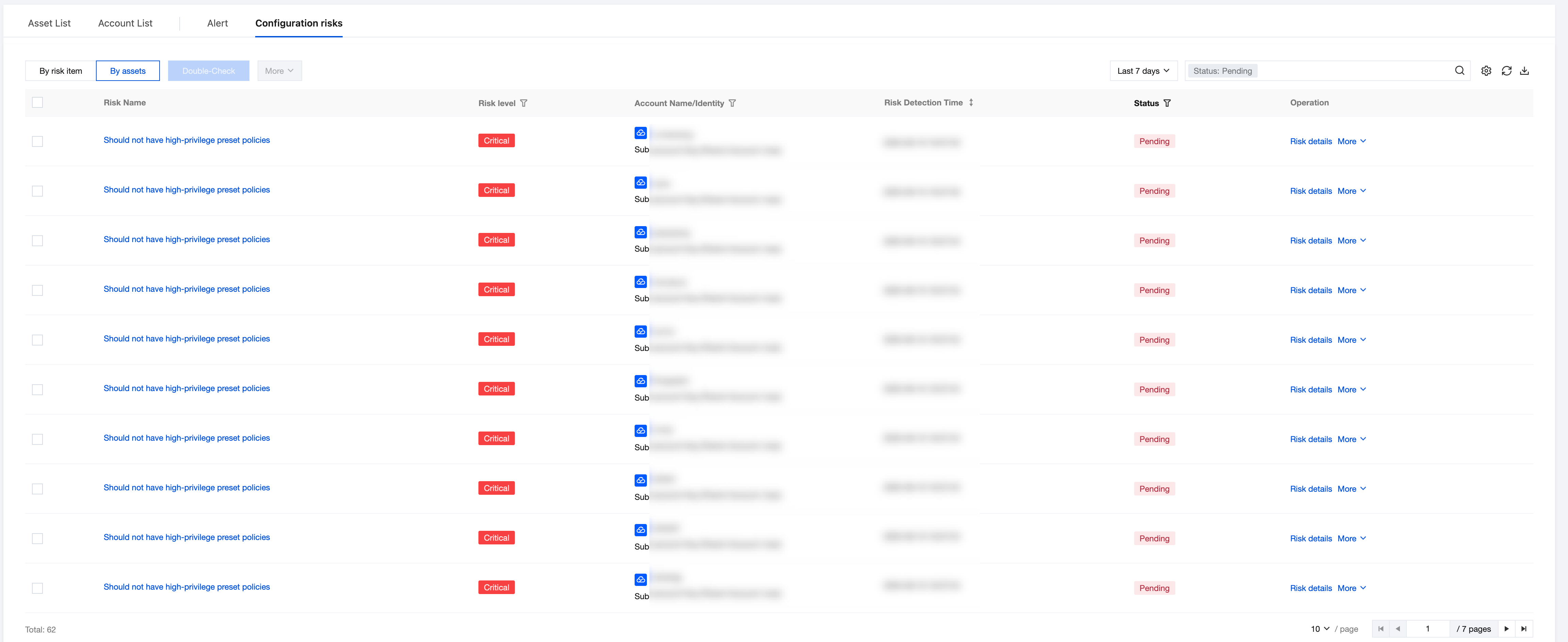
Field Name | Example | Description |
Risk name | Should not have high-privilege preset policies | Click to pull up the risk details drawer. |
Risk Level | High High-risk Medium Risk Low-risk Note. | Risk level is assessed based on Tencent Cloud security practice. |
Account Name/Identity | Account A Root account/Sub-account (Belonging to main account: Main account B) | AK belongs to the cloud service provider and account. If it is a sub-account, show root account information. Hover over to view account ID and APPID; supports filtering root account/sub-account. |
Risk detection time | 2025-01-12 18:00:00 | Risk detection time. Format: YYYY-MM-DD HH:MM:SS. support sorting |
Processing Status | unprocessed Converged ignored | Show risk processing status, manually done tag, processing status supports filtering. |
3. In the asset perspective list, select the required risk and click Risk Details/More.
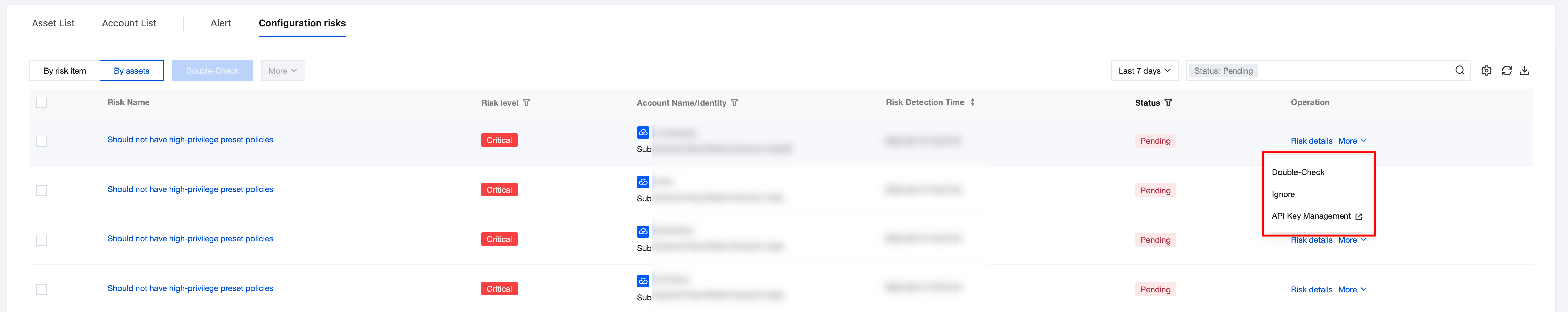
Operation Type | Description | |
risk details | | Click to pull up the risk details drawer to view the risk description and judgment evidence. |
Others | Detection | Click to recheck the rule. |
| marked as ignored | Click to change the processing status to "ignored". |
| API Key Management | Click to navigate to CAM > Access Keys > API Key Management. |
Risk Details
1. In the Configuration risks > By assets page, select the required risk name and click Risk Details.
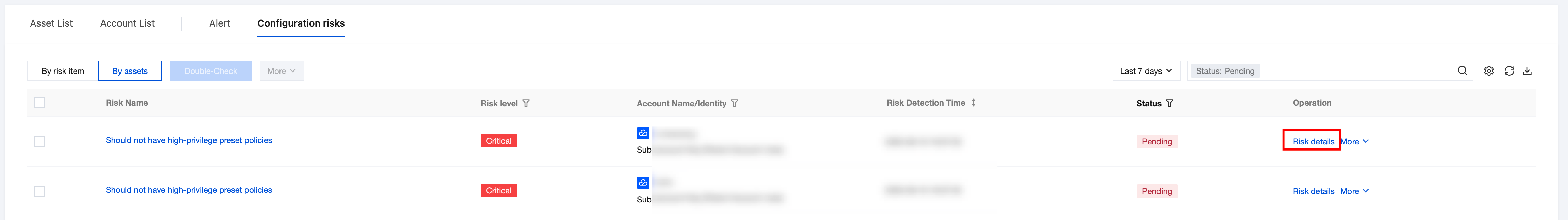
2. In the Risk Details page, view basic info, risk evidence and description, API call status, and configuration suggestions.
View basic risk info, including Account, account identity, access method, account protection, related CAM policy, associated account alarms, and related AK as well as associated alarms.
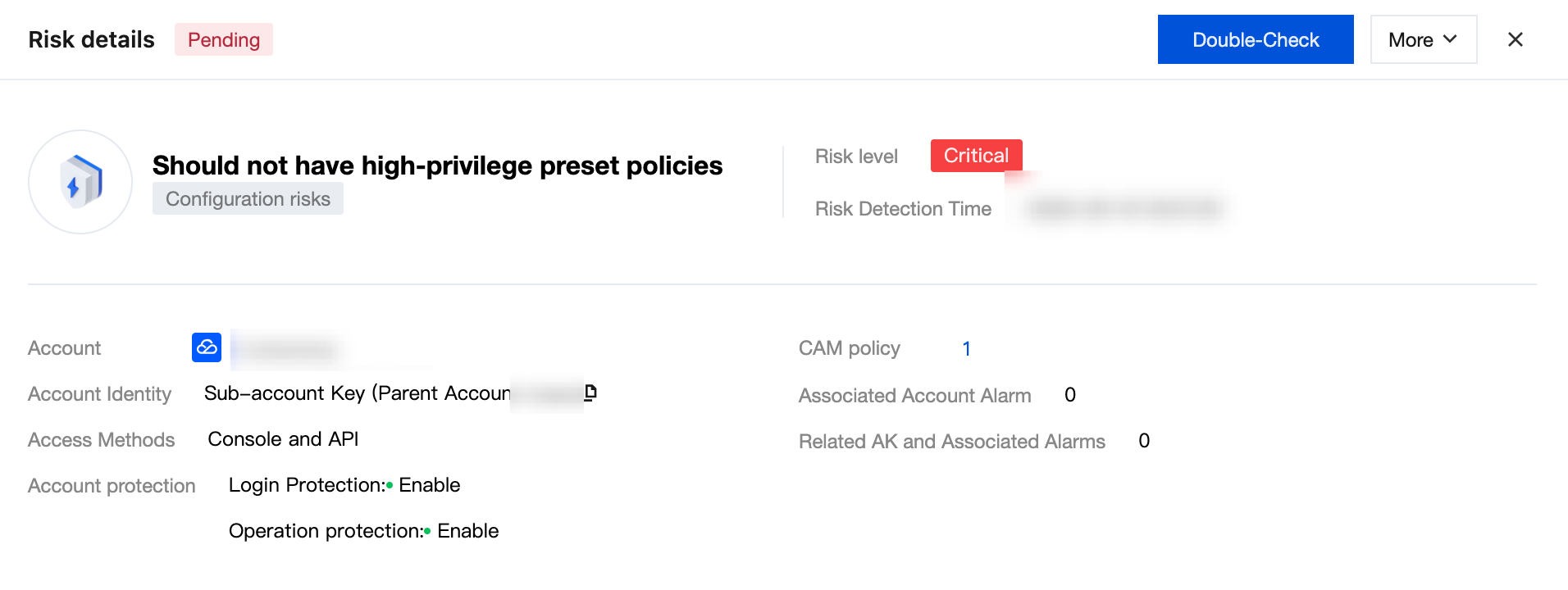
View risk description and evidence. The risk details include Policy Name, operation, resource, and request conditions. In addition, there are two types of risk evidence: AK name, creation time, last used time, and preset policy name.
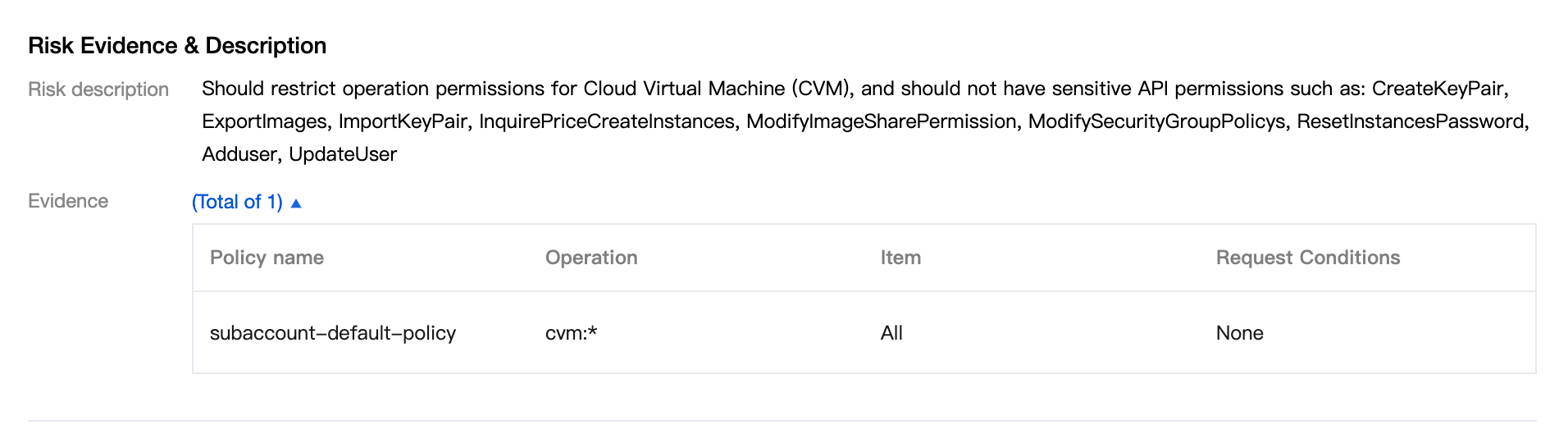
View API call status and configuration suggestions.
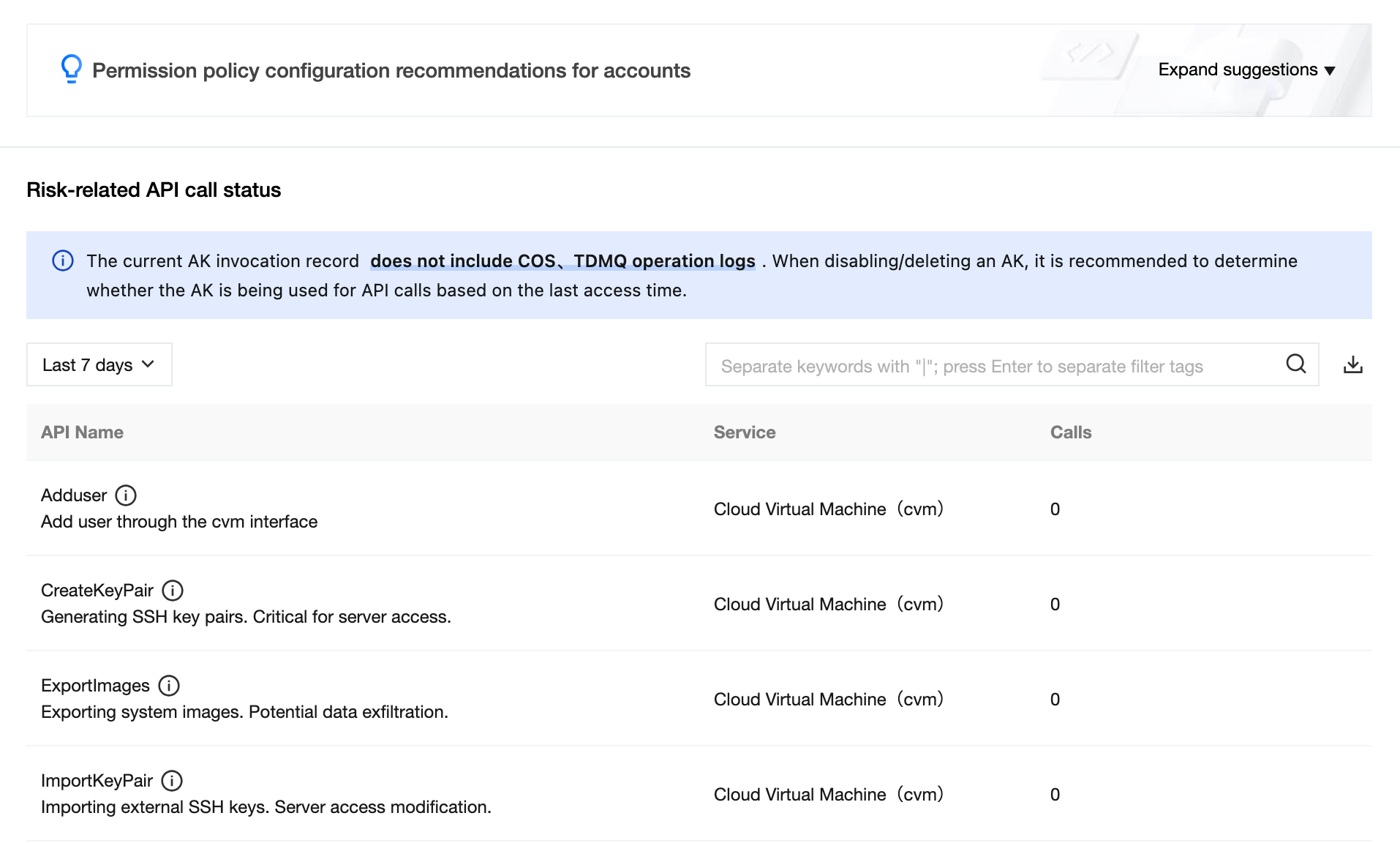
Field Name | Example | Description |
API Name | AddUser | The API name. Hover over the icon to display the API description in detail. |
Associated Service | Cloud Access Management (cam) | This API belongs to the product or service module. |
Call count | 1 | Call count measurement unit for this API. |
Rule Description
Monitor AK leakage and abnormal calls in real time. Monitoring includes three types: hacker tool detection, GitHub leakage (GitHub collaboration and IP check), and abnormal IP calls to sensitive APIs. Specific rules are in the table below:
Rule Name | Rule Description |
Operation permissions for the Virtual Private Cloud (VPC) should converge. | Operation permissions for the VPC should converge. The following sensitive API permissions should not be granted: CreateCcnRouteTables, CreateNatGatewayDestinationIpPortTranslationNatRule, CreateNatGatewaySourceIpTranslationNatRule, CreateSecurityGroup, CreateSecurityGroupWithPolicies, CreateVpcEndPoint, CreateVpcPeeringConnection. |
Operation permissions for Tencent Cloud VectorDB should converge. | Operation permissions for Tencent Cloud VectorDB should converge. The following sensitive API permissions should not be granted: ModifyAccessKey. |
Operation permissions for Tencent Kubernetes Engine (TKE) should converge. | Operation permissions for Tencent Kubernetes Engine (TKE) should converge. The following sensitive API permissions should not be granted: CreateClusterEndpoint, DeleteEKSCluster, DeleteEKSContainerInstances, DescribeClusterKubeconfig, DescribeClusterSecurity, DescribeEKSClusterCredential. |
Operation permissions for TencentCloud High Performance Computing (THPC) should converge. | Operation permissions for TencentCloud High Performance Computing (THPC) should converge. The following sensitive API permissions should not be granted: ModifyInitNodeScripts. |
Operation permissions for cloud development services should converge. | Operation permissions for cloud development services should converge. The following sensitive API permissions should not be granted: CreateCloudUser, DescribeEnvs. |
Operation permissions for Tencent Cloud Automation Tools (TAT) should converge. | Operation permissions for Tencent Cloud Automation Tools (TAT) should converge. The following sensitive API permissions should not be granted: CreateCommand, CreateInvoker, EnableInvoker, InvokeCommand, RunCommand. |
Operation permissions for Security Credential Service should converge. | Operation permissions for Security Credential Service should converge. The following sensitive API permissions should not be granted: AssumeRole, GetFederationToken. |
Operation permissions for Serverless Cloud Function (SCF) should converge. | Operation permissions for SCF should converge. The following sensitive API permissions should not be granted: CreateFunction, Invoke. |
Operation permissions for TencentDB for Redis should converge. | Operation permissions for TencentDB for Redis should converge. The following sensitive API permissions should not be granted: ClearInstance, KillMasterGroup, ModifyInstanceAccount, ResetPassword. |
Operation permissions for TencentDB for PostgreSQL should converge. | Operation permissions for TencentDB for PostgreSQL should converge. The following sensitive API permissions should not be granted: ResetAccountPassword. |
Operation permissions for Tencent Cloud Organization should converge. | Operation permissions for Tencent Cloud Organization (TCO) should converge. The following sensitive interface permissions should not be granted: AddUserToGroup, CreateUserSyncProvisioning. |
Operation permissions for Tencent Cloud Lighthouse (Lighthouse) should converge. | Operation permissions for Tencent Cloud Lighthouse (Lighthouse) should converge. The following sensitive API permissions should not be granted: CreateKeyPair, ImportKeyPair, ResetInstancesPassword. |
Operation permissions for Tencent Cloud Domains should converge. | Operation permissions for Tencent Cloud Domains should converge. The following sensitive API permissions should not be granted: CreateDomainBatch, RegisterDomain, RenewAgentPay. |
Operation permissions for cloud resolution (DNS) should converge. | Operation permissions for cloud resolution (DNS) should converge. The following sensitive API permissions should not be granted: CreateDomainBatch, CreateShareDomains. |
Operation permissions for Tencent Container Security Service (TCSS) should converge. | Operation permissions for Tencent Container Security Service (TCSS) should converge. The following sensitive API permissions should not be granted: DeleteMachine. |
Operation permissions for Cloud Workload Protection Platform (CWP) should converge. | Operation permissions for Cloud Workload Protection (CWP) should converge. The following sensitive API permissions should not be granted: DeleteMachine. |
Operation permissions for CloudAudit should converge. | Operation permissions for CloudAudit should converge. The following sensitive API permissions should not be granted: DeleteAudit, DeleteAuditTrack. |
Operation permissions for TencentDB for MySQL should converge. | Operation permissions for TencentDB for MySQL should converge. The following sensitive API permissions should not be granted: CloseWanService, CreateAccounts, CreateRoInstanceIp, DescribeAccounts, DescribeBackups, DescribeBinlogs, ModifyAccountPassword, ModifyDBInstanceSecurityGroups, OpenWanService. |
Operation permissions for Cloud Access Management (CAM) should converge. | Operation permissions for Cloud Access Management (CAM) should converge. The following sensitive API permissions should not be granted: AddUser, AddUserToGroup, AttachRolePolicy, AttachUserPolicy, CreateAccessKey, CreateApiKey, CreateCollApiKey, CreateOIDCConfig, CreateRole, CreateSAMLProvider, CreateServiceLinkedRole, CreateUserOIDCConfig, CreateUserSAMLConfig, EnableApiKey, GetProjectKey, ListAccessKeys, ListUsers, UpdateAccessKey, UpdateCollPassword, UpdateUser. |
Operation permissions for Blackstone physical servers (BM) should converge. | Operation permissions for Blackstone physical servers (BM) should converge. The following sensitive API permissions should not be granted: BuyDevices, CreateSpotDevice, ReloadDeviceOs, ResetDevicePassword, ShutdownDevices. |
Operation permissions for Cloud Virtual Machine (CVM) should converge. | Operation permissions for CVM should converge. The following sensitive API permissions should not be granted: CreateKeyPair, ExportImages, ImportKeyPair, InquirePriceCreateInstances, InquiryPriceRunInstances, ModifyImageSharePermission, ModifySecurityGroupPolicies, ResetInstancesPassword, RunInstances, AddUser, UpdateUser. |
Delete long-term unused AK keys | Delete long-term unused AK keys, even if the AK is banned. |
Should not have high-privilege preset policies | AKs should not have high-privilege preset policies like AdministratorAccess, QCloudResourceFullAccess, QCloudCAMFullAccess, or QCloudFinanceFullAccess. |
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No
Feedback

