Collaborator or Sub-user Authorization
Last updated:2026-01-13 16:29:11
Authorization Scheme
In practical cases, the product usage accounts are typically collaborators or sub-users. Depending on authorization requirements, you can grant different granularity operation permissions to sub-users or collaborators through the following methods.
Authorization Scheme | Applicable Scenario | Operation Instructions |
Authorization based on preset permissions | Applicable to sub-users to configure management permissions for all resources. | Set sub-user permissions: Quickly grant relevant access permissions to sub-users through preset policies. For details, see Preset Policy Overview. |
Authorization based on custom permission policies | Applicable to granular management of sub-user permissions, including: Operation-based authorization: Grant sub-users partial operation configuration permissions. Basic tag-based authorization: Grant sub-users management permissions for resources with different attribute tags. Mandatory tag-based authorization: Grant sub-users management permissions for resources with different attribute tags, requiring sub-users to bind only the resources with authorized tags when creating resources. | Set resource tags: Add attribute tags to resources when creating resources. Set sub-user permissions: Create a CAM custom policy and grant it to a sub-user. For more examples of custom policy application scenarios, see Custom Policy Operation Guide. |
Prerequisites
Preset Policy Operation Examples
Preset Policy Overview
Policy Name | Description | Required or Optional | Description |
QcloudEMRFullAccess | Full read-write access for EMR (EMR) | No | Full feature operation permissions for EMR products. |
QcloudEMRReadOnlyAccess | Read-only access for EMR (EMR) | No | View permissions for all features of EMR products |
QcloudEMRPurchaseAccess | Financial permissions for EMR products | No | If purchase or change of configuration is not needed, this permission can be disabled. |
QcloudCamRoleFullAccess | Full read-write access for CAM Users and Roles | No | This permission can be added to create users, custom policies, and custom roles, as well as to perform other operations. |
Note:
The pre-defined QcloudEMRPurchaseAccess policy allows you to manage the financial permissions for purchasing EMR products for all users. When this policy is granted to a user, it includes the financial permissions for CVM, CDB, and EMR. If you need to restrict a user's ability to purchase CVM and CDB, do not grant the corresponding product ordering permissions.
Purchase and manage EMR clusters
For scenarios involving resource purchasing (including creating clusters, modifying configurations, or scaling out), granting collaborators or sub-users the EMR access policy, EMR financial policy, and the custom TencentDB purchase policy is required. If there are no resource purchasing scenarios (including service configuration management or restarts), only the EMR access policy is required.
Note:
For the annual/monthly subscription purchase method, if financial permissions are not granted, a pending order will be generated and linked to an account with financial permissions for approval. The pay-as-you-go purchase method does not support order approval; financial permissions must be granted.
Policy Category | Policy Name | Policy Description |
EMR Preset Policy | QcloudEMRFullAccess | Full read-write access for EMR (select one) |
EMR Preset Policy | QcloudEMRReadOnlyAccess | Read-only access for EMR (choose one of the two) |
EMR Preset Policy | QcloudEMRPurchaseAccess | Financial permissions for EMR products |
The root account grants the above permissions to the Sub-user or Collaborator. The steps are as follows:
1. Log in to CAM Console, find the corresponding Sub-user or collaborator in Users > User List, then click Authorize.
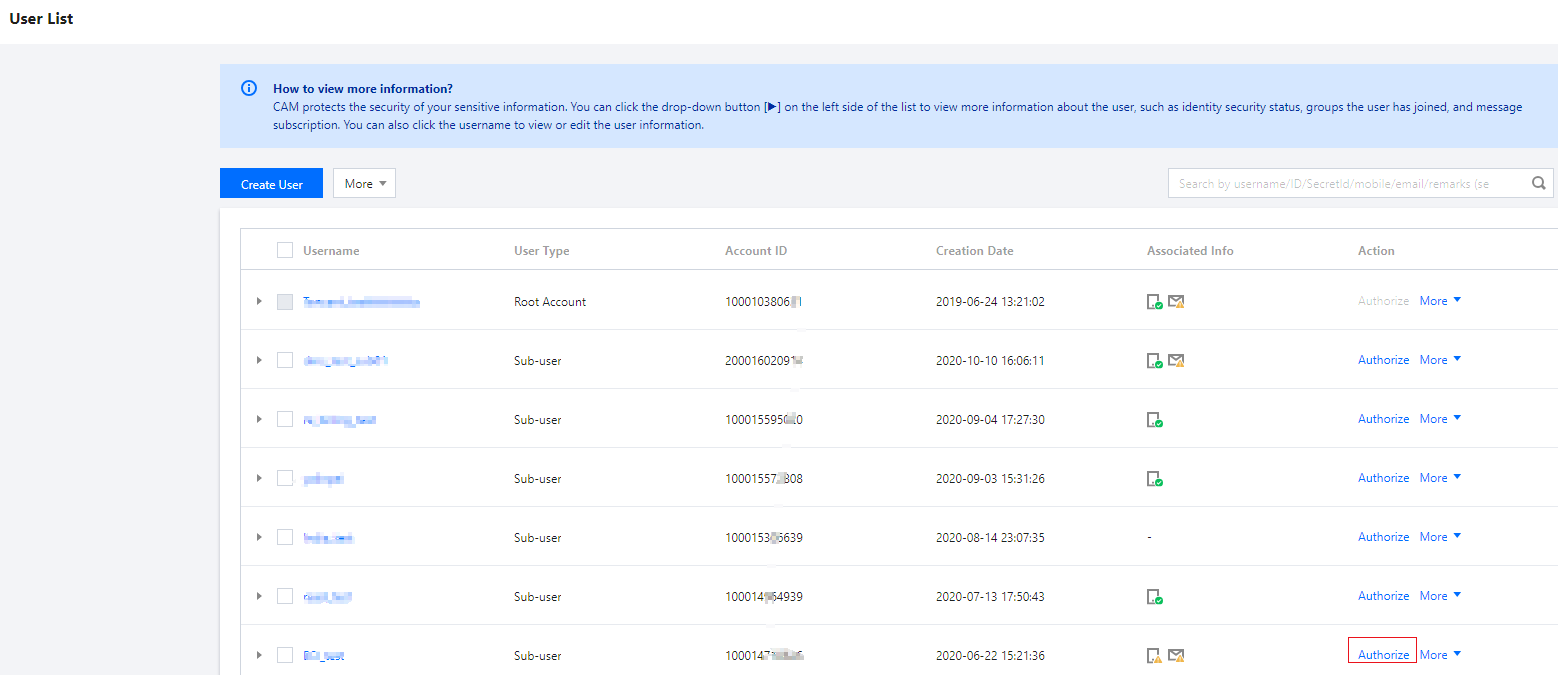
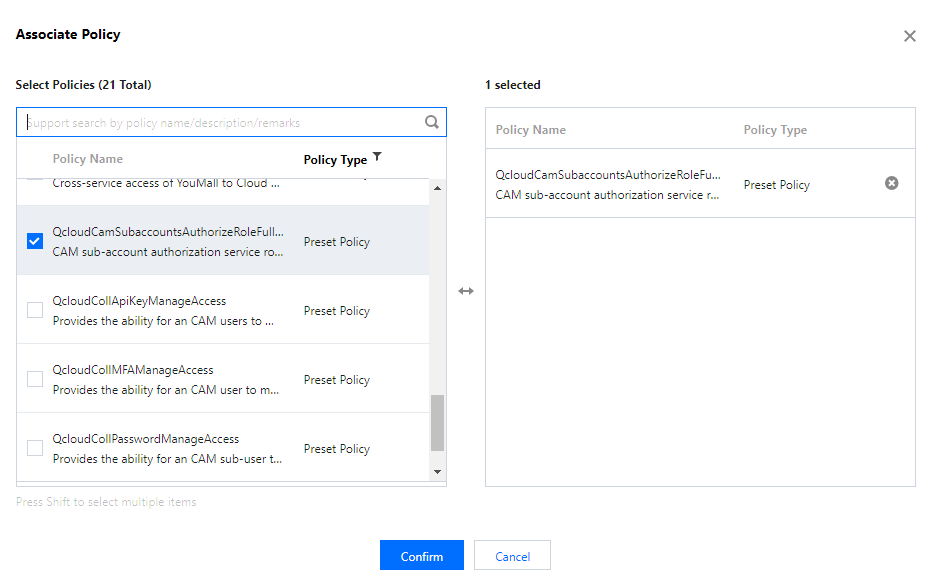
2. Search for the policy listed in the table above (the following image takes QcloudEMRFullAccess policy as an example) within Associated Policies. Once the policy is selected, click OK to confirm.
3. Grant the EMR financial policy QcloudEMRPurchaseAccess, similar to step 2.
Setting Custom Service Role
For scenarios involving setting custom service roles, including setting the cluster COS service role, which is used for precise control of COS bucket permissions (For details, see Custom Cluster COS Service Role), and granting collaborators or sub-users the CAM access policy is required. The specific steps are as follows:
1. Log in to the CAM console, find the corresponding sub-user or collaborator in User > User List, then click Authorize.
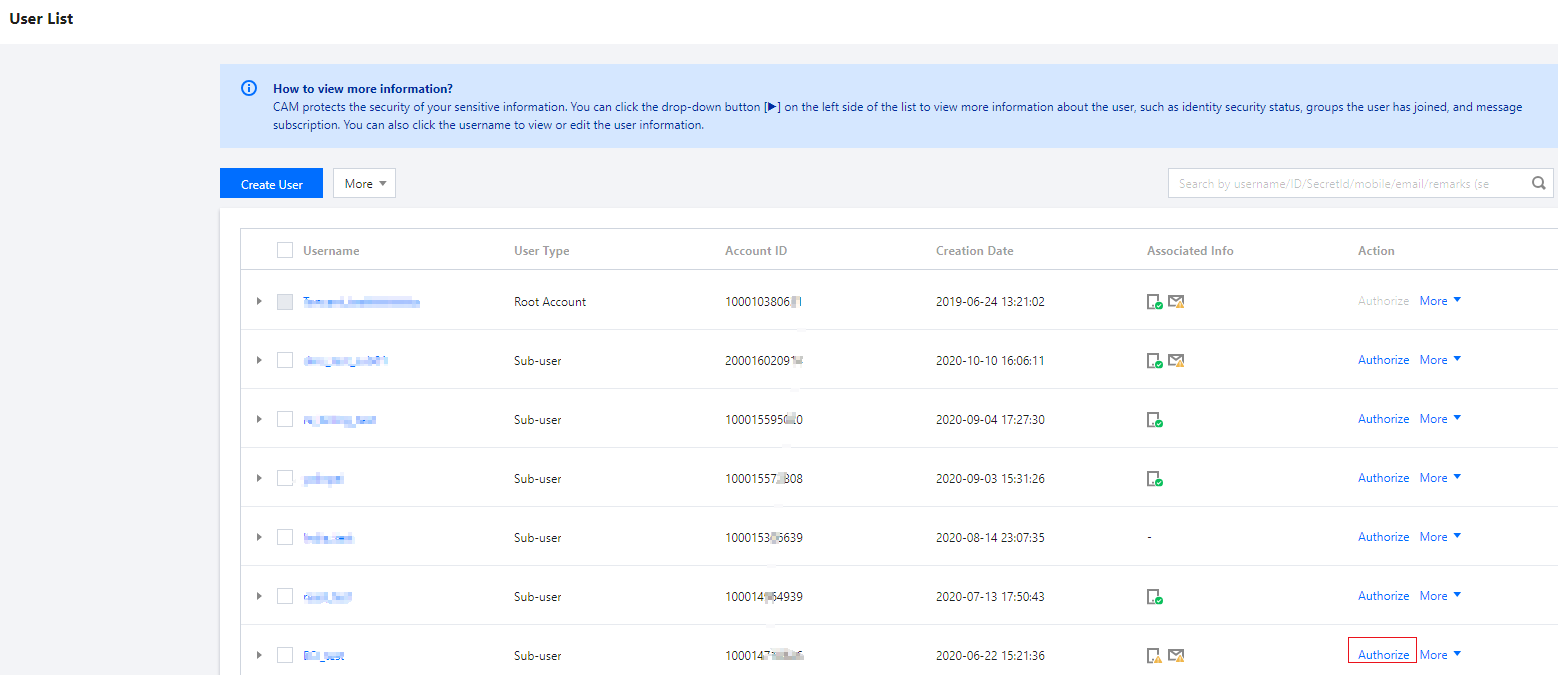
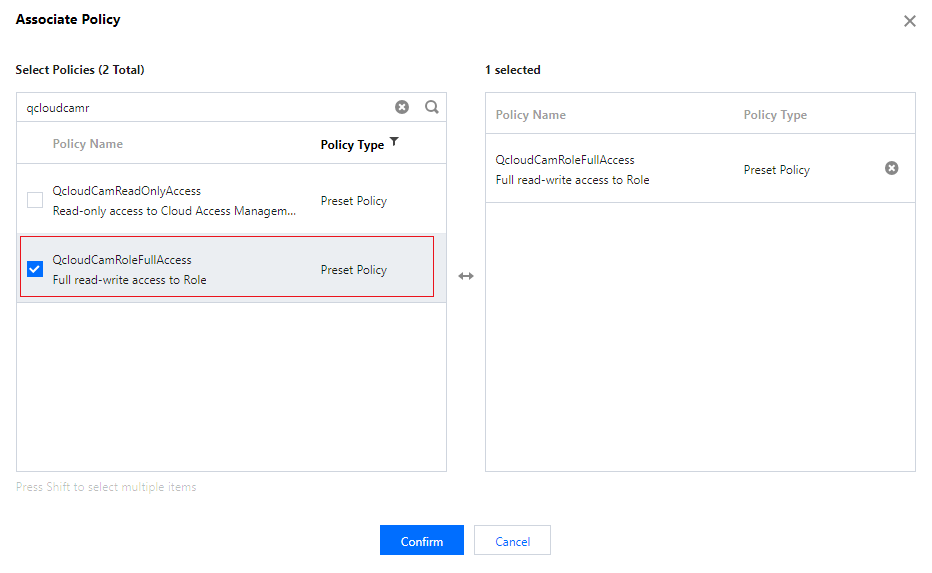
2. Search for QcloudCamRoleFullAccess policy within Associated Policies. Once the policy is selected, click OK to confirm.
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No
Feedback

