Granting Resource-Level Permission to Sub-account
Last updated:2026-01-05 10:03:28
Scenarios
You can use the policy feature of the Cloud Access Management (CAM) console to grant the permissions for RabbitMQ resources owned by the root account to sub-accounts. Sub-accounts that obtain the permissions will gain access to those resources. This document takes granting permissions for the resources of a cluster to sub-accounts as an example. The operation steps for other types of resources are similar.
Prerequisites
You have created sub-accounts for employees using the Tencent Cloud root account. For detailed operations, see Creating a Sub-account.
At least one RabbitMQ cluster is available.
Operation Steps
Step 1: Obtaining the ID of the RabbitMQ Cluster
1. Use the root account to log in to the TDMQ for RabbitMQ console.
2. In the left sidebar, select Cluster. Select the target region and copy the ID of the target cluster.
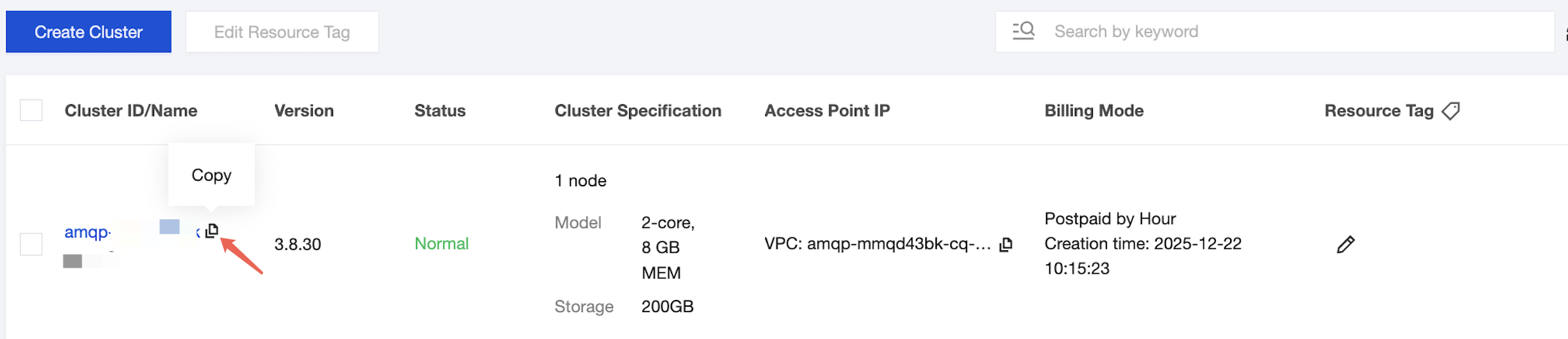
Step 2: Creating an Authorization Policy
1. Log in to the CAM console.
2. In the left sidebar, select Policies, click Create a Custom Policy, and set the policy creation method to Create by Policy Builder.
3. In the visualized policy generator, keep the Effect as Allow and select the Service. The following describes how to select a service:
Managed Edition: Enter TDMQ to filter, and select Tencent Distributed Message Queue (tdmq) from the results.
Serverless Edition: Enter trabbit to filter, and select RabbitMQ Serverless (trabbit) from the results.
4. In Action, select All Actions. You can also select an appropriate operation type based on your actual business needs.
Note:
Certain APIs currently do not support resource authentication. For the APIs that support resource authorization, those displayed on the console page shall prevail.
5. In the Resource section, select Specific resources, and locate the cluster resource type. You can check Any resource of this type (authorize all cluster resources) on the right, or click Add a six-segment resource description (authorize specific cluster resources). In the pop-up sidebar dialog box, enter the cluster ID in the Resource Prefix field.
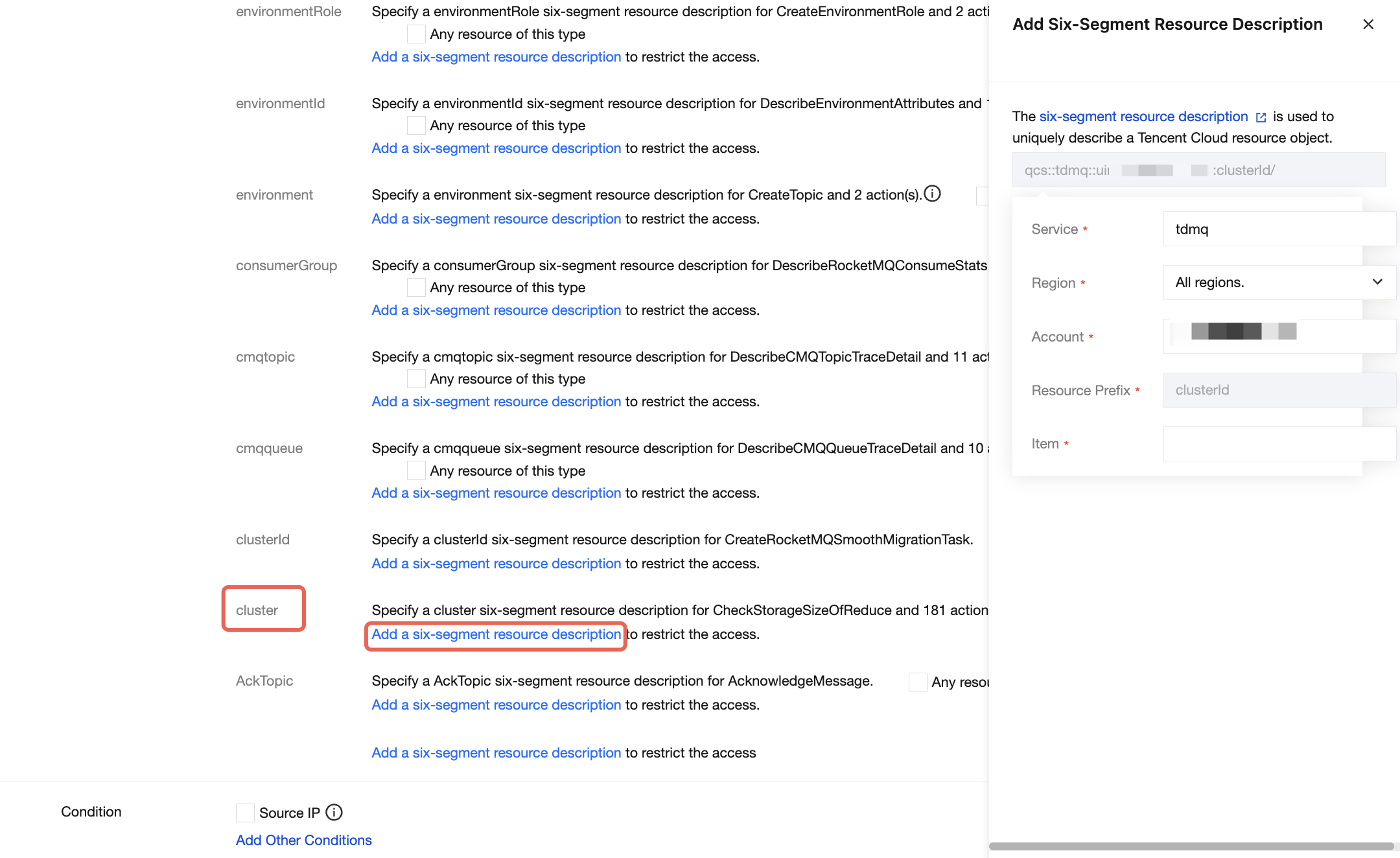
6. In the Condition section, select whether to specify the source IP address based on actual business requirements. After a source IP address is specified, access to the specified operation is allowed only when the request comes from the specified IP address range.
Click Next to set the policy name. The policy name is automatically generated by the console, with the default name of "policygen", with the suffix number generated based on the creation date. You can customize it.
7. Click Select User or Select User Group to grant resource permissions.
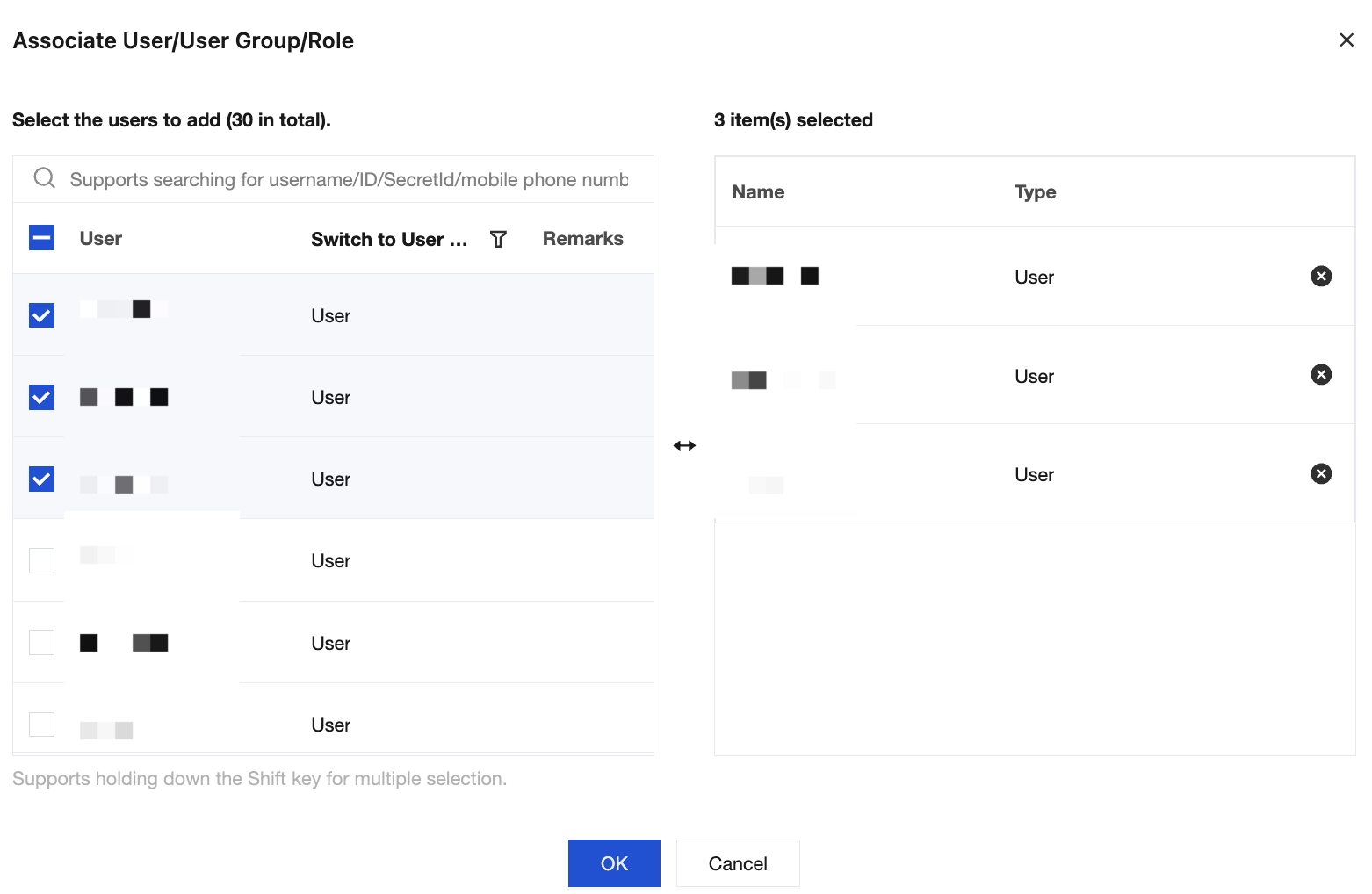
8. Click completed, and the sub-accounts granted resource permissions now have the ability to access the relevant resources.
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No
Feedback

