Granting Tag-Level Permissions to Sub-accounts
Last updated:2026-01-30 14:55:28
Scenarios
You can confirm it by the policy feature in the CAM console to grant sub-accounts read/write permissions for MQTT resources owned by the root account and already bound with tags via tag authorization. Sub-accounts with permissions can obtain control capability over resources with corresponding tags.
Prerequisites
The Tencent Cloud root account has been used to create a sub-account for the employee. For detailed instructions, see create a new sub-account.
Have at least one MQTT cluster resource instance.
Have at least one Tag. If you have no, can go to the Tag Console > Tag List to create.
Operation Steps
Step 1: Bind Tag to the Resource
1. Use the root account to log in to the TDMQ for MQTT console and enter the Cluster page.
2. Select the target cluster, click Edit Resource Tag in the upper left corner, and bind the resource tag to the cluster.

Step 2: Authorize by Tag
1. Log in to the CAM console.
2. Select Policies in the left sidebar, click Create a custom policy, and choose Authorize by Tag as the policy creation method.
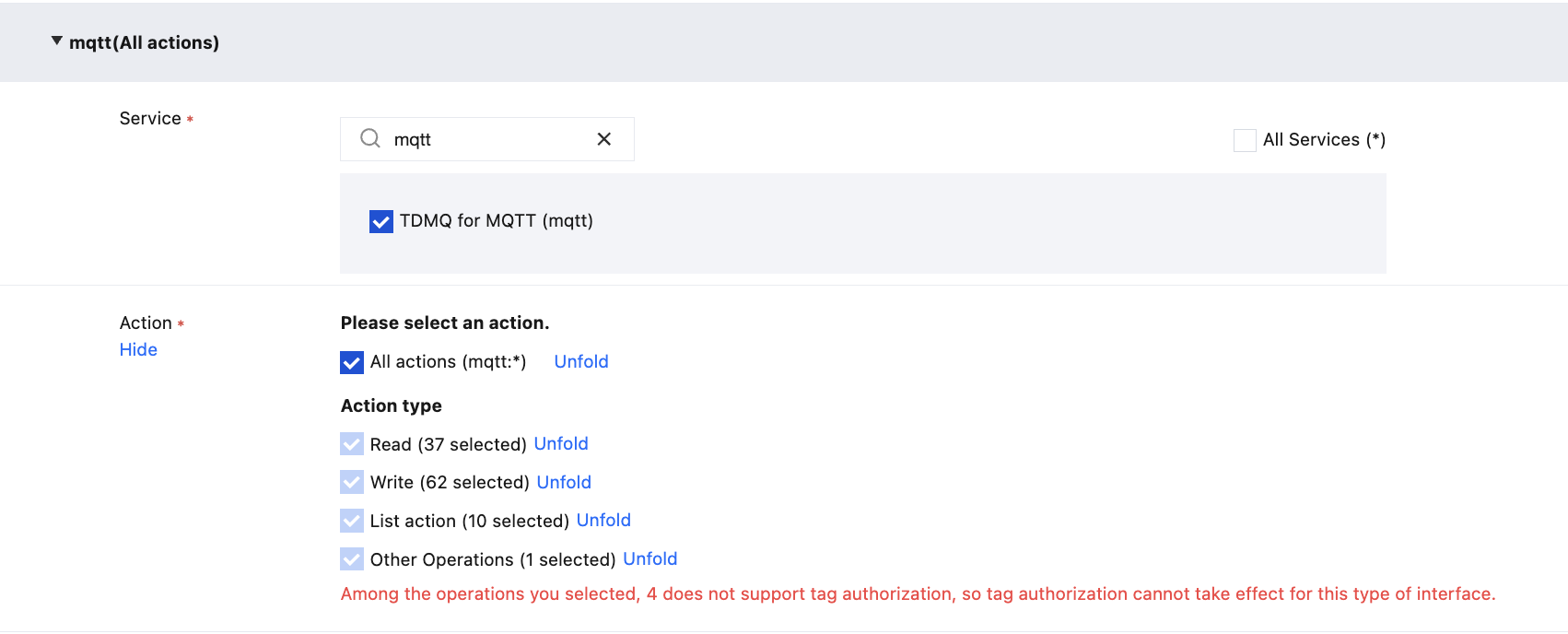
3. In the Visual Strategy Generator, enter mqtt in Service to filter, select TDMQ for MQTT (mqtt) from the results, choose All actions (*) under Actions, or select corresponding operations as needed.
Note:
All APIs of the services are included in the operations allowed. You can use Whether tag-based authorization is supported to to filter APIs and check whether they support authorization by tag.
Yes: APIs support tag-based authorization and have the operation permissions for resources associated with the tags.
No: APIs that do not support tag-based authorization. In subsequent steps, you can choose whether to grant operation permissions for all resources to these APIs that do not support tag-based authorization.
To support authorization for multiple services, you can click Add in the upper-left corner to add multiple authorization statements and configure authorization policies for other services.
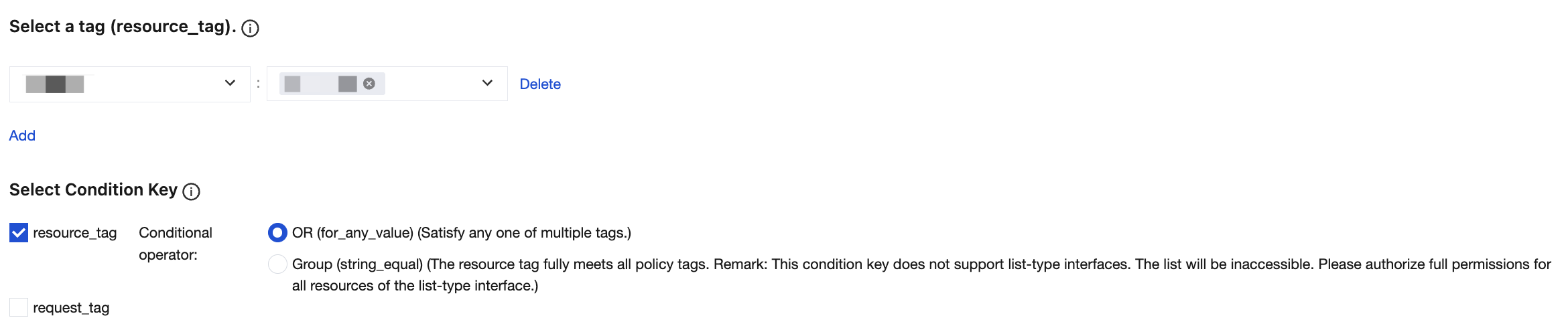
4. In the Select a Tag position, select the tag key and tag value bound to the cluster resource. Multiple tags are in an OR relationship, and you only need to meet one of them.
5. In the Select Condition Key position, select the condition key. The condition keys resource_tag and request_tag allow multiple selections or can be selected separately.
6. Select whether to Whether to grant permission "resource": "*" to APIs that do not support Tag. If checked, the API will include operation permissions for all resources.
7. Click Next, set policy name. The Policy Name is automatically generated by the console, defaulting to "policygen" with a numerical suffix generated based on the creation date. You can customize it.
8. Click Select User or Select User Group to select the user or user group to grant resource permissions.
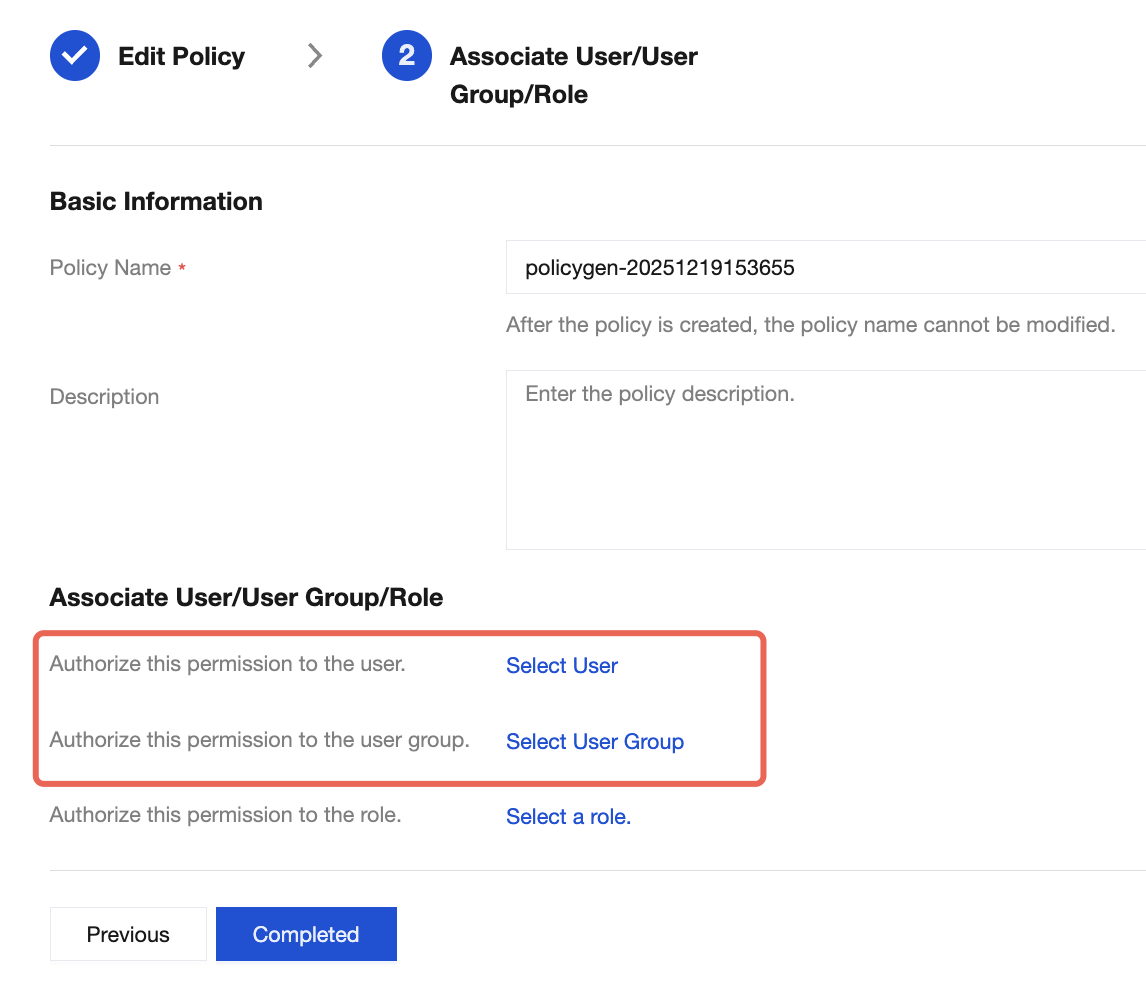
9. Click Completed to enable the sub-account to control resources under the specified tag based on policies.
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No
Feedback

