Step 2: Configuring Server Certificate
Last updated:2026-01-30 14:55:28
The server certificate is used for client authentication of the server. The server will use the certificate you select to establish connections with clients. To ensure cluster security, Message Queue for MQTT Edition provides a default server certificate for one-way authentication. If you want to use your own certificate for authentication, you can refer to this guide to bind a custom certificate. After purchasing or self-issuing the server certificate, you need to host it on Tencent Cloud SSL Certificates and then complete the configuration in the MQTT console.
Prerequisites
The CA certificate has been obtained.
OpenSSL v1.1.1i or above has been installed.
Step 1: Prepare Certificates
Certificate Requirements
To ensure compatibility and security, the server certificate (End Entity Certificate) must meet the following requirements:
1. The certificate must include the X.509 v3 Extended Key Usage extension, which must contain serverAuth (TLS Web Server Authentication) as specified in the RFC 5280 standard.
The certificate must include the necessary Subject Alternative Name (SAN) extension and Common Name (CN). Certificates issued by a publicly trusted Certificate Authority (CA) typically include these required extensions by default.
Note:
If a certificate contains both a CN and SAN, when the TLS Server Name Indication (SNI) selects a certificate, it will prioritize matching domain names in the SAN extension. If no SAN exists, it will fall back to using the CN field for matching.
Major browsers have deprecated CN matching, such as Chrome 58+. Therefore, when using Web Secure Socket as the MQTT transport layer, you must ensure the SAN extension and Server Auth value are properly configured.
2. The certificate chain can contain up to 5 certificates.
3. The certificate chain file does not exceed 16 KiB.
Generate Server Certificate Using CA Certificate
You can purchase server certificates from trusted certificate authorities or use a CA certificate to issue server certificates. For methods to obtain a CA certificate, see CA Certificate. The following uses the RSA algorithm as an example to briefly describe how to generate a server certificate using a CA certificate.
If you use a self-signed CA certificate to generate server certificates, you can follow the instructions below. After generating the server certificate, you can upload it to SSL Certificates.
1. Create a file named
client.csr.cfg and modify its content as needed.[req]default_bits = 2048prompt = nodefault_md = sha256distinguished_name = dn[dn]C=CNST=SHXXXL=SHO=TXOU=MQTTemailAddress=xxx@xxxCN=client-test
2. Create a file named
client.crt.cfg with the following content:authorityKeyIdentifier=keyid,issuerbasicConstraints=CA:FALSEkeyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment, keyCertSign
3. Run the following command to generate the server certificate private key and the certificate signing request (csr) file for certificate verification.
openssl req -new -sha256 -nodes -out client.csr -newkey rsa:2048 -keyout client.key -config <(cat client.csr.cfg)
openssl req -new -sha256 -nodes -out client.csr -newkey rsa:2048 -keyout client.key -config client.csr.cfg
4. Run the following command to generate the server certificate.
openssl x509 -req -in client.csr -CA CA.crt -CAkey CA.key -CAcreateserial -out client.crt -days 500 -sha256 -extfile client.crt.cfg
Step 2: Hosting the Server Certificate
Upload the prepared certificate to Tencent Cloud SSL Certificates. For details, see Upload SSL Certificate Instructions.
Step 3: Bind Custom Certificate
1. Log in to the MQTT Console.
2. Click Resource > Cluster in the left sidebar. After selecting a region, click the "ID" of the target cluster to enter the cluster basic information page.
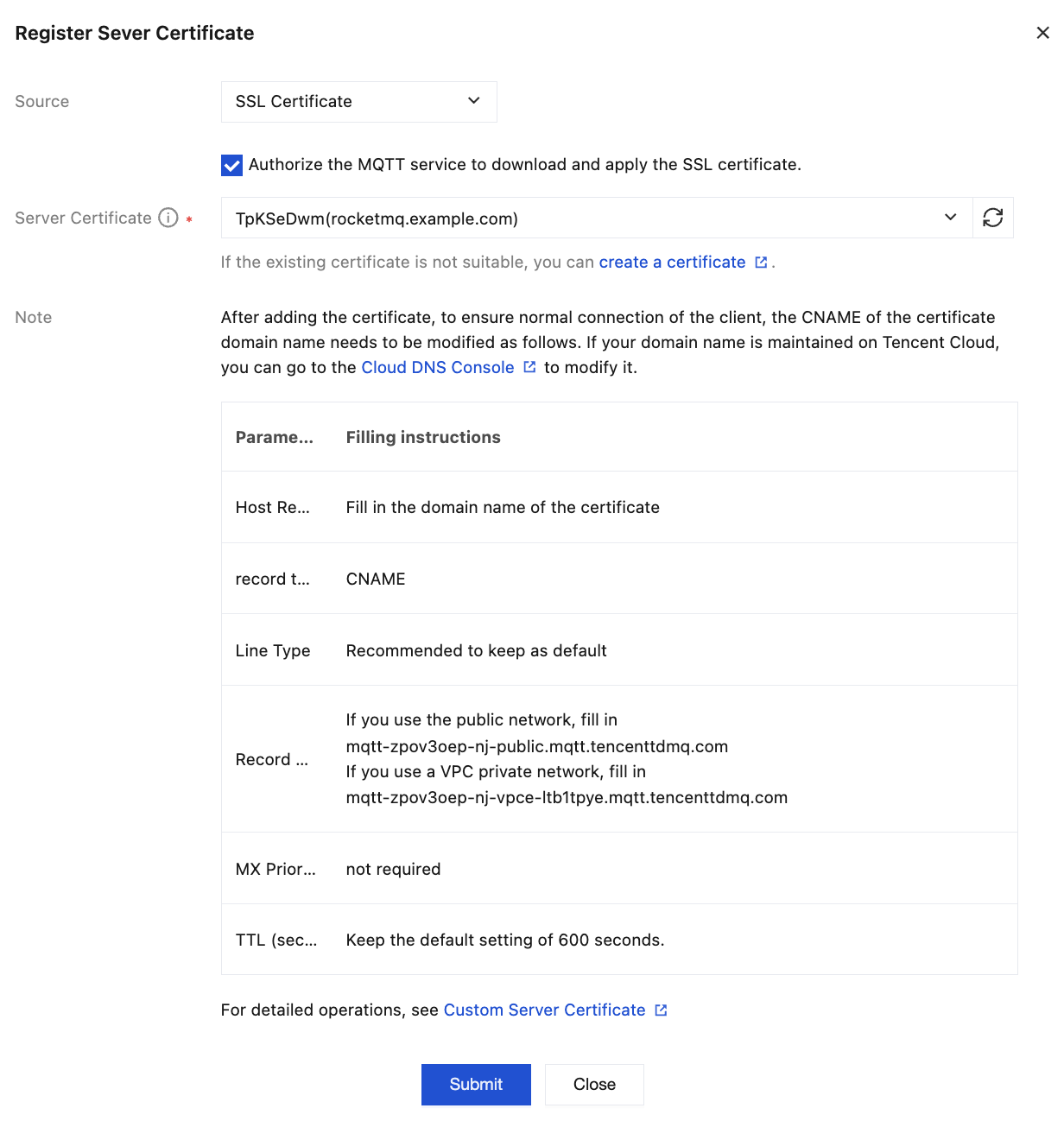
3. On the cluster details page, select the Server Certificate tab, and click Register Server Certificate in the top-left corner.
Source: Select SSL Certificates.
Server certificate: In the drop-down box, select the SSL Certificates hosted in Tencent Cloud.
4. Click Submit to complete the binding.
Step 4: Configure Custom Domain Name
After the certificate is added, to ensure normal client connections, the CNAME configuration for the certificate domain must be modified accordingly. If your domain is managed on Tencent Cloud, you can go to the DNS Resolution console to modify the DNS records.
Parameter | Instructions |
Host Record | Fill in the domain name for the certificate in use. |
Record Type | CNAME |
Record Value | If using public network, enter -. If using VPC private network, enter mqtt-xxxx-nj-vpce-xxx.mqtt.tencenttdmq.com. |
MX Priority | Not required |
TTL (seconds) | It is recommended to retain the default value of 600s. |
Assume the selected server certificate Subject Alternative Name contains the following domain names:
mqtt-abc.company.com.Refer to Cloud DNS - CNAME Record to create a CNAME record that resolves
mqtt-abc.company.com to the domain name provided by the cluster's access point: mqtt-xxx-sh-public.mqtt.tencenttdmq.com. Subsequently, the cluster can be accessed via mqtt-abc.company.com.Step 5: (Optional) Disable the Default Server Certificate
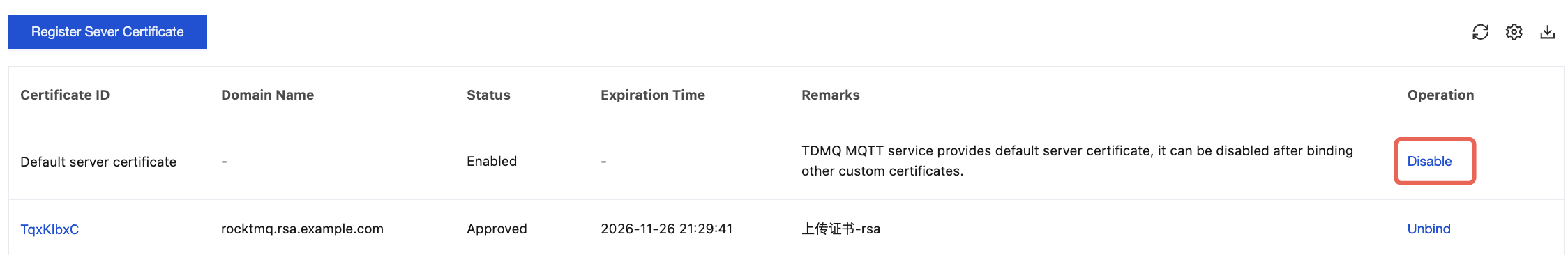
After a custom certificate is bound, you can disable the default server certificate provided by TDMQ MQTT. The specific steps are as follows:
On the server certificate management page, click Disable in the operation column of the default server certificate. After confirmation in the pop-up window, the default certificate can be disabled.
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No
Feedback

