Downloading Backup Files
Last updated:2025-11-24 17:13:41
Feature Introduction
To ensure data security and business continuity, TencentDB for MongoDB provides a secure and convenient feature for downloading backup files. In routine Ops, you can obtain backup files quickly by using this feature in scenarios, such as emergency data recovery, development and testing environment building, or cross-environment data migration.
Core Feature | Feature Description |
Backup file management view | The backup file list centrally displays the generation records and download progress of all files, and you can directly download or delete files. |
Public network download | You can enable public network download with one click and set passwords for backup files to ensure secure access. |
Download permission control | You can configure the download and access permissions for backup files through IP addresses and VPCs, effectively preventing unauthorized access and ensuring data security. |
Operation Steps
1. Log in to the TencentDB for MongoDB console.
2. In the left sidebar, choose MongoDB > Replica Set Instance or Shard Instance. The operations for replica set instances and sharded cluster instances are similar.
3. At the top of the instance list page on the right, select a region.
4. In the instance list, locate the target instance.
5. Click the target instance ID to go to the Instance Details page.
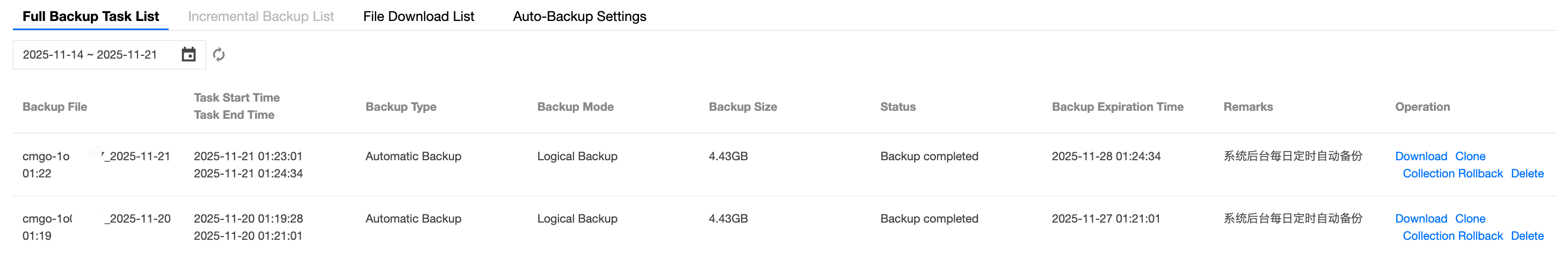
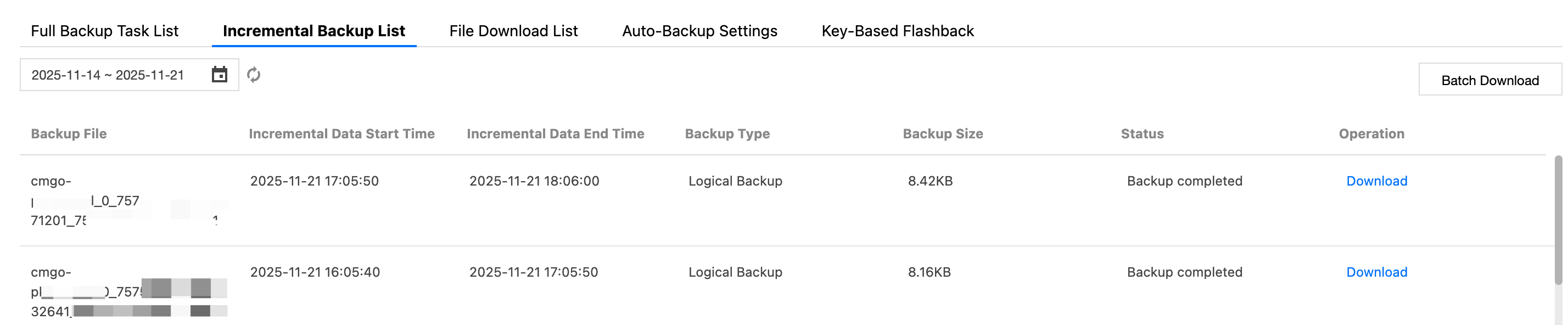
6. Switch to the Backup and Rollback page, and select the Full Backup Task List tab or the Incremental Backup List tab, as shown in the following figure.
Full Backup Task List
Incremental Backup List
7. In the backup file list, click Download in the Operation column. In the Generate Backup File dialog box, configure the conditions for generating backup files.
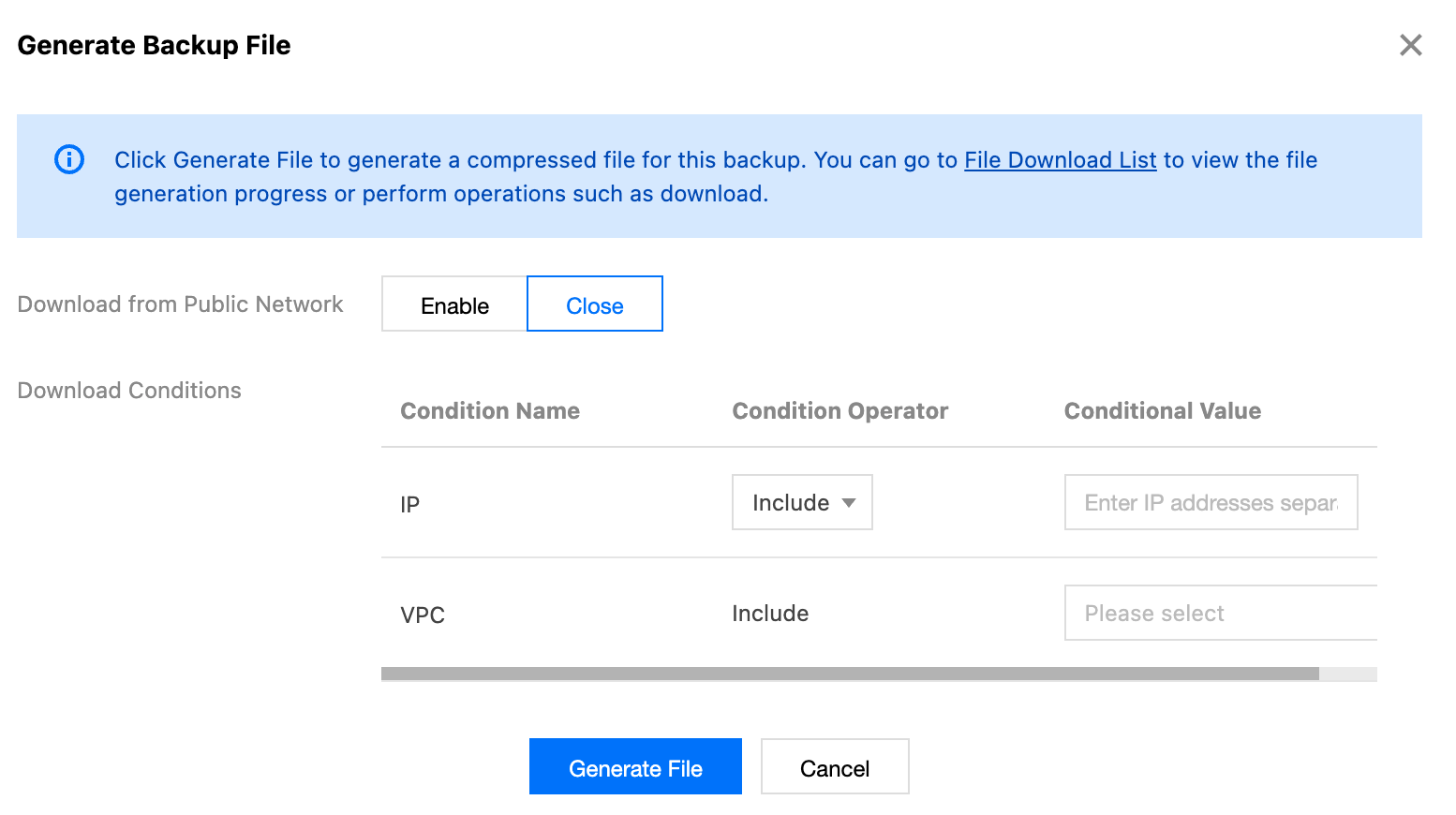
Parameter | Description | |
Public network download | Public network download | Sets whether to enable public network download. |
| Public Network File Encryption | To enable public network download, click  |
| Set Password | In the input box, set the password for file encryption. Click Generate Random Password to randomly generate a password in the input box. Note: In the encryption process, the PBKDF2 algorithm is used to derive a high-strength key based on the set password, and then the AES-256 algorithm is used to encrypt the file, strengthening file security. For details about decryption instructions, see Decrypting Encrypted Files. |
Download Conditions | IP | Restricts the client access source IP addresses that are allowed to download backup files in the condition operator and condition value. Only when the client IP address matches the preset IP range, can backup files be downloaded. |
| VPC | Restricts the client access source VPCs that are allowed to download backup files in the condition operator and condition value. The download permission is available only when a request is from the specified VPC. |
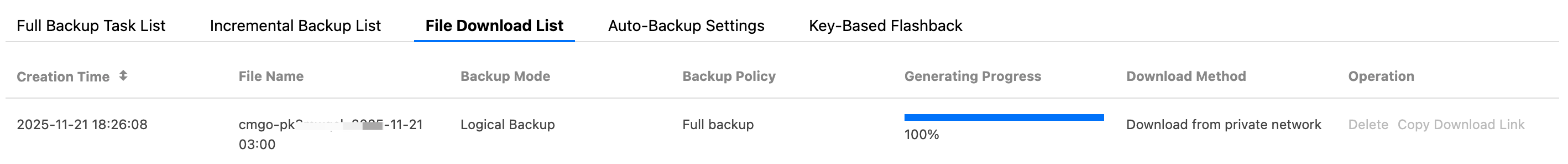
8. Switch to the File Download List tab to view the list of generated backup files. In the Operation column, click Copy Download Link and use the copied link in the browser to directly download backup files.
Decrypting Encrypted Files
Use the OpenSSL command line for decryption. The decryption command format is as follows.
Note:
If you develop a decryption tool, ensure that it supports the following parameters:
Algorithm: AES-256-CBC
Key derivation: PBKDF2, 10,000 iterations, SHA-256 hash
Salt value extraction: Read from the first 16 bytes of the file (Salted__ + 8-byte salt value)
Data decryption: CBC mode, PKCS7 padding
openssl enc -aes-256-cbc -d -pbkdf2 -iter 10000 \\-in [encrypted file name] \\-out [decrypted file name] \\-k "[your password]"
Example: If the encrypted file name is encrypted.tar, the password is 12345, and the decrypted file is decrypted.tar, the command is as follows:
Note:
Ensure that the password is correct (case-sensitive and special characters).
The -pbkdf2 and -iter 10000 parameters should be specified.
The decrypted file will be restored to its original status.
openssl enc -aes-256-cbc -d -pbkdf2 -iter 10000 \\-in encrypted.tar \\-out decrypted.tar \\-k "12345"
Related APIs
API | Description |
DescribeDBBackups | |
DescribeBackupDownloadTask | |
CreateBackupDownloadTask |
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No
Feedback

