漏洞管理
最后更新时间:2025-09-30 16:27:33
本文将为您介绍漏洞管理的功能和操作,帮助您管理服务器中的漏洞风险。
概述
腾讯云主机安全支持对目前主流主机(Windows,Linux 等)上的漏洞进行周期性和及时性的检测功能。主机安全支持对指定主机和漏洞类别的检测,同时支持忽略漏洞等功能,可为您提供漏洞的风险、特征、严重等级及修复建议等信息,可视化界面有助于您更好的管理服务器中的漏洞风险。
限制说明
至少存在1台已绑定防护授权的主机(专业版/旗舰版),才可解锁漏洞管理功能。
漏洞管理范围说明如下:
漏洞管理功能 | 漏洞类型 | Linux 系统 | Windows 系统 |
漏洞扫描 专业版、旗舰版主机适用 | Linux 软件漏洞 | ✓ | × |
| Windows 系统漏洞 | × | ✓ |
| Web-CMS 漏洞 | ✓ | ✓ |
| 应用漏洞 | ✓ | ✓ |
漏洞防御 旗舰版主机适用 | Linux 软件漏洞 | × | × |
| Windows 系统漏洞 | × | × |
| Web-CMS 漏洞 | ✓仅支持部分漏洞 | × |
| 应用漏洞 | ✓仅支持部分漏洞 | × |
漏洞自动修复 旗舰版主机适用 | Linux 软件漏洞 | ✓ 仅支持部分漏洞 | × |
| Windows 系统漏洞 | × | × |
| Web-CMS 漏洞 | ✓ 仅支持部分漏洞 | ✓ 仅支持部分漏洞 |
| 应用漏洞 | × | × |
因漏洞修复可能对用户业务造成影响,漏洞自动修复并非检出漏洞后立即进行自动化修复,须用户了解漏洞后单击修复并进行数据备份,才可进行自动化修复。
操作指南
1. 登录 主机安全控制台。
2. 单击左侧导航中的漏洞管理,各功能说明如下。
漏洞扫描
在漏洞扫描区域中,您可进行一键扫描,获取漏洞扫描的结果,也可设置定时扫描,及时暴露漏洞风险并进行处理。
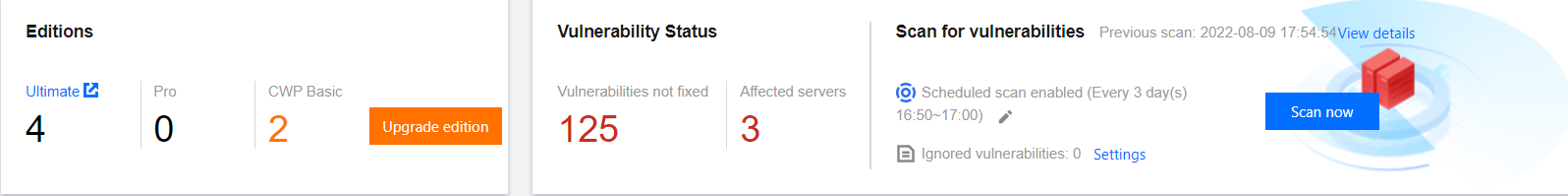
单击一键扫描将打开一键扫描设置弹窗,您可对本次扫描的漏洞类别、漏洞等级、扫描超时时长、扫描服务器范围进行设置,设置后可立即扫描。
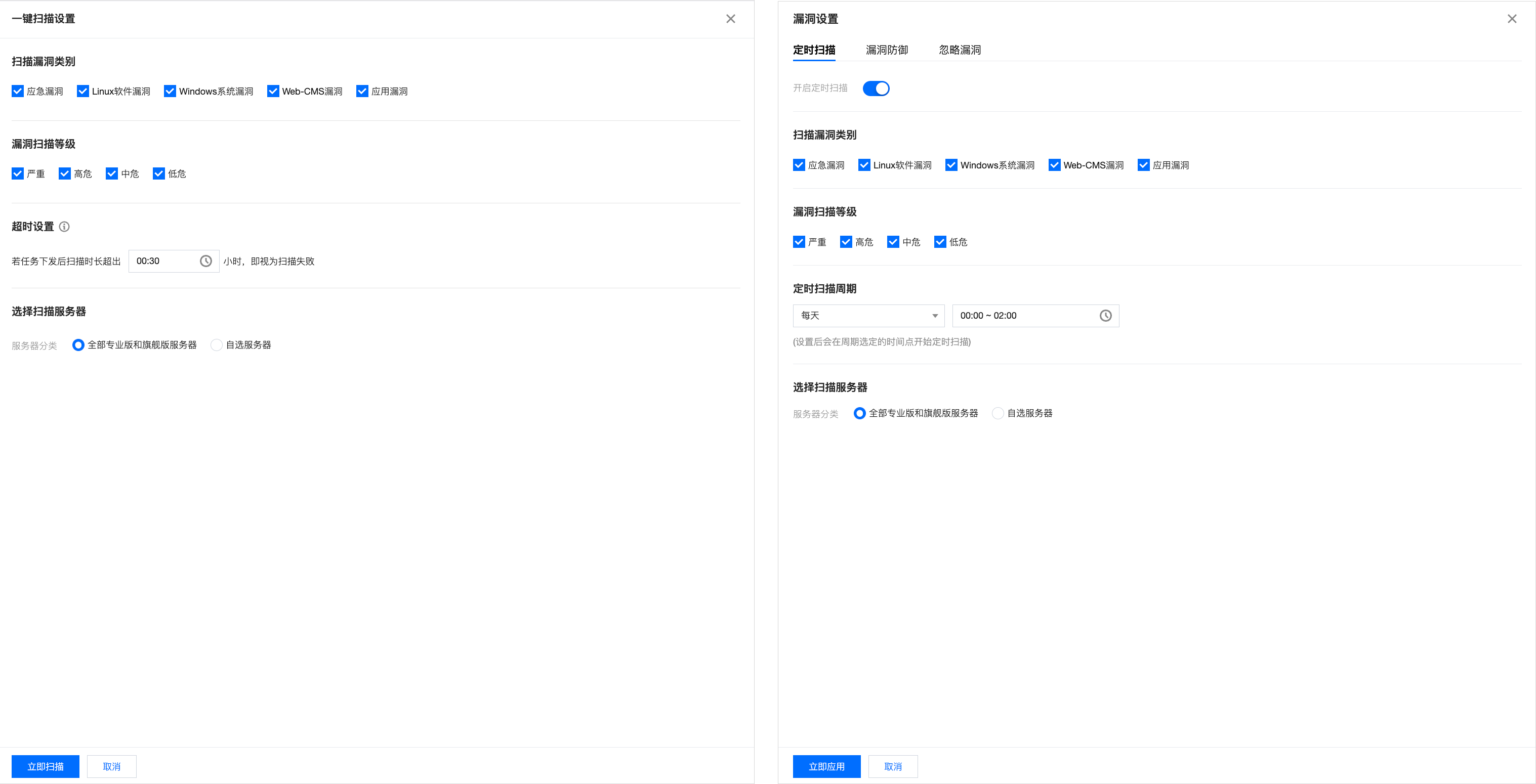
单击扫描设置或定时扫描的编辑图标,可打开漏洞设置弹窗并锚点至定时扫描,您可对定时扫描开关、定时扫描周期、漏洞等级及漏洞类别进行设置,设置后可立即应用。
单击详情可查看上一次扫描的详情,并支持下载 PDF 扫描报告、Excel 扫描结果。
漏洞防御
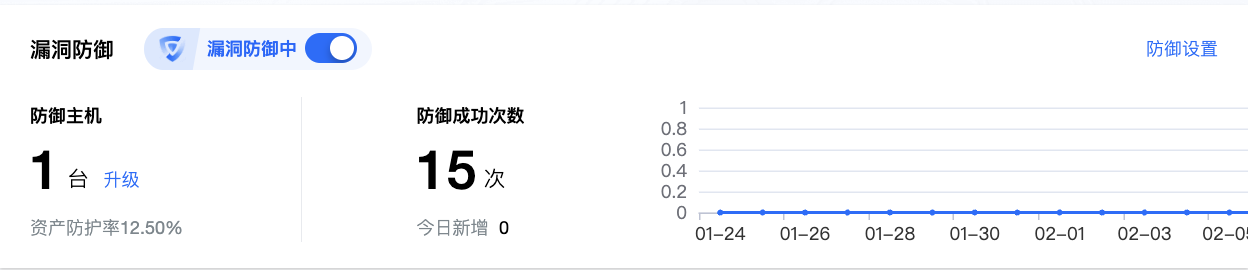
在漏洞防御模块中,支持漏洞防御开关启停、查看防御主机台数、防御成功次数及防御趋势情况。
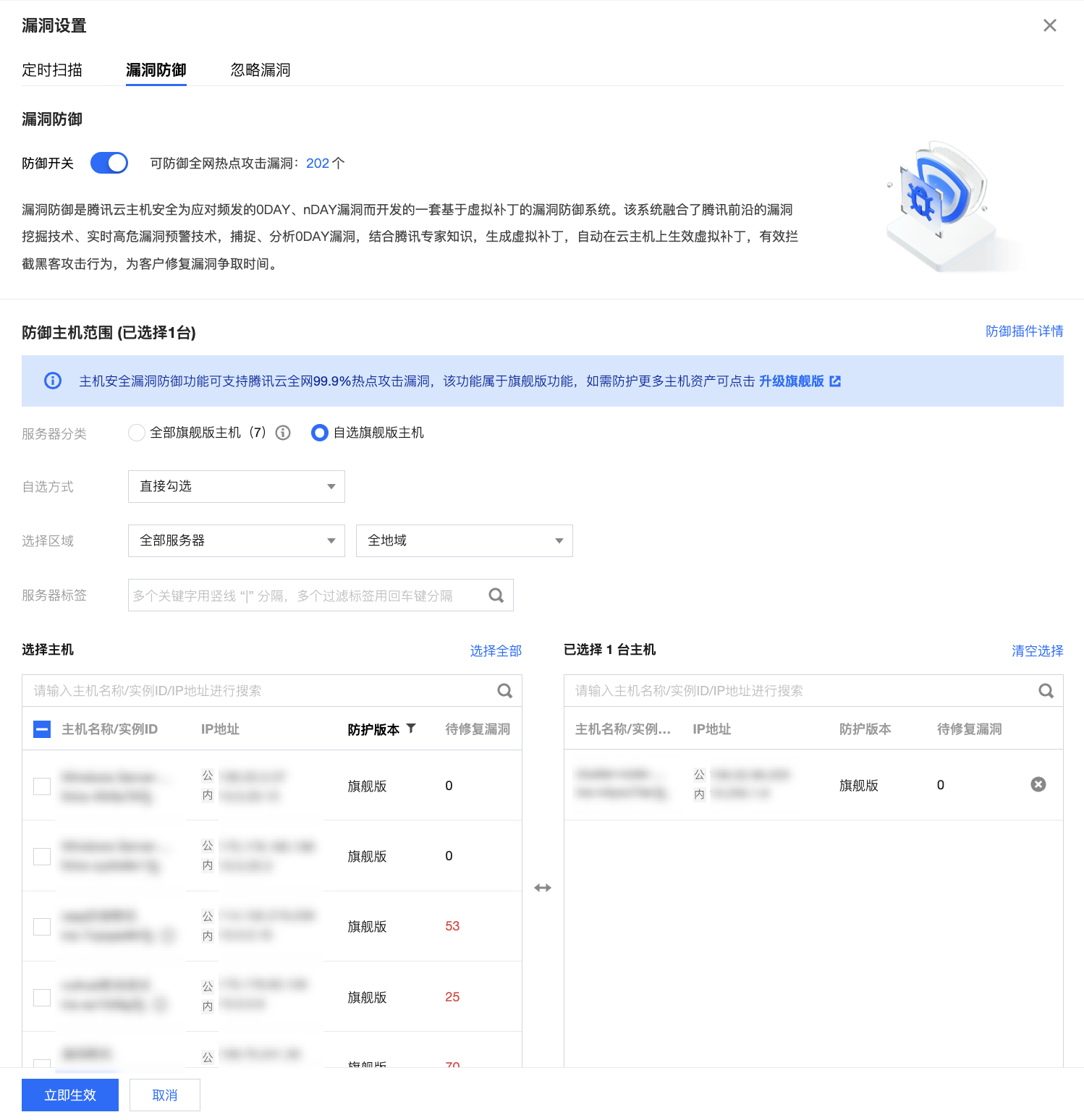
单击防御设置将打开漏洞设置弹窗并锚点至漏洞防御,您可设置漏洞防御开关、查看可防御漏洞、选择防御主机范围、查看防御插件详情。
注意:
开启漏洞防御时,将会有短暂的资源占用升高(平均1~2分钟),建议您避开业务高峰时期,分批开启。
单击防御成功次数,您可查看当前已成功防御的攻击,且可查看攻击详情。
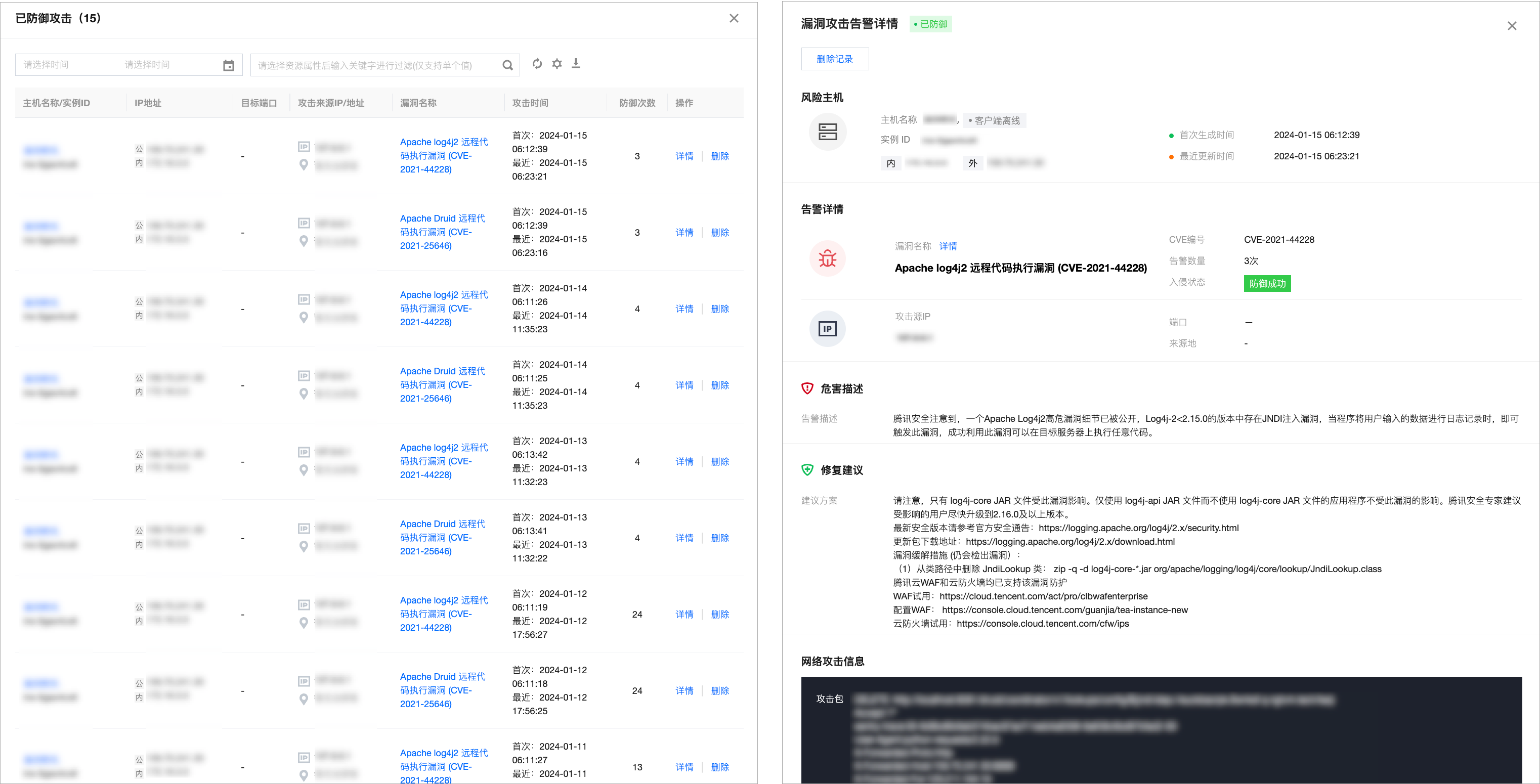
漏洞处置
1. 漏洞管理页下方,您可查看当前检出漏洞的统计情况及详细漏洞列表。
2. 在漏洞概览模块中,展示了漏洞检出情况、网络攻击事件次数及今日新增情况,并展示了主机安全漏洞库总数。
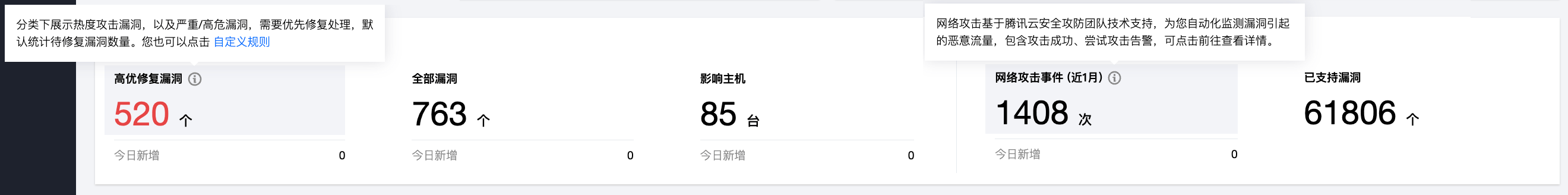
字段说明:
高优修复漏洞:该分类下展示热度攻击漏洞,以及严重/高危漏洞,需要优先修复处理,默认统计待修复漏洞数量。单击自定义规则可对高优修复漏洞进行自定义规则判定。
全部漏洞:检出 Linux 软件漏洞、Windows 系统漏洞、Web-CMS 漏洞、应用漏洞的数量总和。
影响主机:检出漏洞的主机数量。
网络攻击事件:统计近1个月内网络攻击事件的数量。
已支持漏洞:可查看主机安全支持检测的漏洞库,每日最多可检索25次,单次搜索最多可展示100条结果。
3. 在漏洞列表模块中,展示当前检出的具体漏洞,已分为应急漏洞、全部漏洞两类,二者功能无太大差异,下面以全部漏洞举例,为您介绍漏洞处置。
说明:
应急漏洞:专为新发现、影响广、危害高的紧急漏洞而设,相当于一份重点漏洞走查清单,用户可对其发起手动扫描或设置定期扫描,以确保及时响应高危风险。
全部漏洞:汇总展示所有检测到的服务器漏洞,涵盖从低危到严重的全部威胁等级,包含已检测到的应急漏洞。
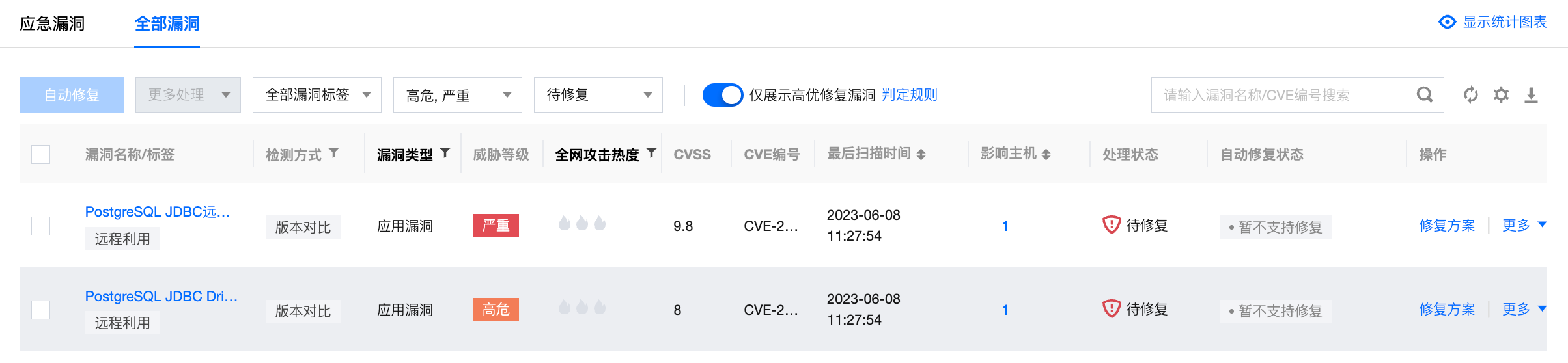
字段说明:
漏洞名称/标签:漏洞名称指当前检出的漏洞,标签指该漏洞的标签(如:远程利用、服务重启、存在 EXP 等)。
检测方式:版本对比、POC 验证。
漏洞类型:Linux 软件漏洞、Windows 系统漏洞、Web-CMS 漏洞、应用漏洞。
威胁等级:严重、高危、中危、低危。
CVSS:指通用漏洞评分系统的评分,分数范围从0到10,0代表最不严重,10代表最严重。
CVE编号:公共漏洞暴露库中,识别该漏洞的唯一编号。
最后扫描时间:最近一次扫描到该漏洞的时间。
影响主机:存在该漏洞的主机数量。
处理状态:待修复、修复中、扫描中、已修复、已忽略、修复失败。
自动修复状态:暂不支持修复、可自动修复(无需重启)、可自动修复(需重启)。
操作
修复方案:暂不支持自动修复的漏洞,可单击修复方案打开漏洞详情弹窗,根据修复方案手动修复漏洞。
自动修复:当前已支持部分 Linux 软件漏洞、Web-CMS 漏洞进行自动修复,可单击自动修复打开漏洞详情弹窗,选择需要修复的服务器进行修复,详情请参见 漏洞自动修复。
重新扫描:重新对该漏洞进行扫描。
忽略:对该漏洞进行忽略,后续不再对该主机扫描该漏洞。
文档反馈

