Activating Audit Service
Last updated:2026-01-06 16:31:42
TencentDB for PostgreSQL provides database audit capabilities to help you record accesses to databases and executions of SQL statements, so you can manage risks and improve the database security level.
Use Cases
Audit risks
Difficulty in tracing and locating security breaches due to incomplete audit logs.
Inability to meet the requirements defined by China's Classified Protection of Cybersecurity (Level 3).
Inability to meet the requirements defined by industry-specific information security compliance documents.
Administrative risks
Business system security risks caused by faulty, non-compliant, and unauthorized operations of technical personnel.
Faulty and malicious operations and tampering by third-party development and maintenance personnel.
Excessive permissions granted to the super administrator, which cannot be audited and monitored.
Technical challenges
Database system SQL injections and maliciously pull data from databases and tables.
Inability to quickly locate the sudden increase of database requests that are not slow logs.
Billing Overview
For information regarding the billing of TencentDB for PostgreSQL Database Audit , please refer to the Database Auditing Billing Documentation.
Supported Versions
TencentDB for PostgreSQL Database Audit supports dual-server high-availability (one primary and one secondary) primary instances and read-only instances of the PostgreSQL engine in versions v11.12_r1.14, v12.7_r1.15, v13.3_r1.12, v14.2_r1.15, v15.1_r1.7, v16, and later versions. For earlier versions of TencentDB for PostgreSQL instances, if you need to enable full audit capability, please first upgrade the kernel minor version.
Supported Regions
TencentDB for PostgreSQL audit is currently in the beta testing stage. The audit service is only supported in several regions such as Beijing, Guangzhou, Shanghai, Bangkok, Chengdu and Shanghai Autonomous Driving Cloud. Please be informed.
Prerequisites
Note:
Enabling and disabling the audit service requires a database restart. Please be aware.
Directions
1. Log in to TencentDB for PostgreSQL Console.
2. In the left sidebar, select Database Audit.
3. After selecting a region above, on the audit instance page, click Audit Status to view the list of enabled and disabled audit instances.
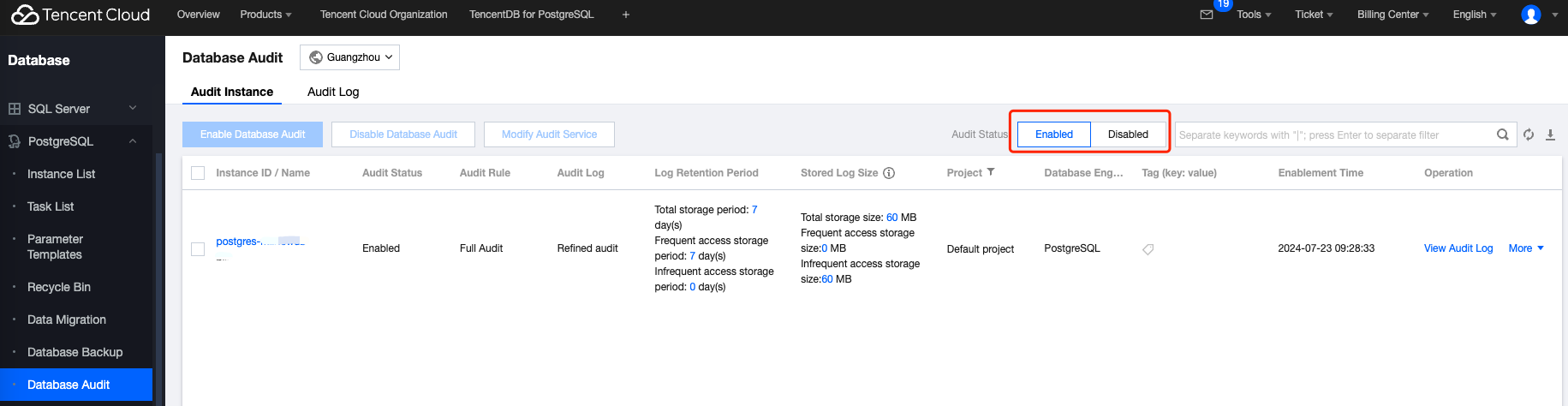
4. In the audit instance list, find the target instance (you may also quickly search for it by filtering resource attributes in the search box). In its Operation column, click Enable Database Audit.
Note:
Batch enabling the audit service is supported. On the audit instance list page, check multiple target instances, and click Enable Database Audit above to enter the setting interface.
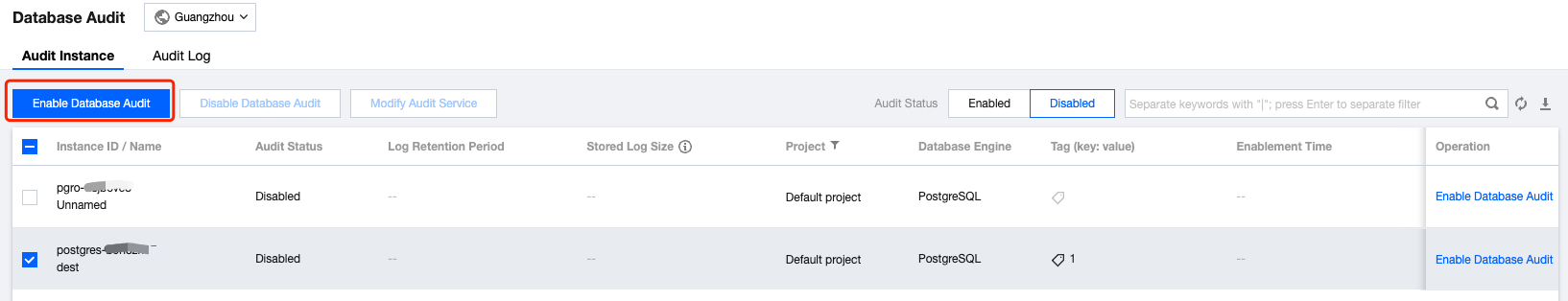
5. In the Enable Database Audit interface, sequentially complete Select Audit Instance, Audit Rule Settings, Audit Service Settings, read and check Tencent Cloud Service Agreement, and then click OK.
5.1 Select Audit Instance
Under the Audit Instance Selection, the system by default checks the instances selected in Step 4. Also, in this window, instance modifications (other instance selections, multiple selections) are supported. Or, in the search box, quickly search for target instances by instance ID/Name. After completing the instance selection, you may proceed to Audit Rule Settings.
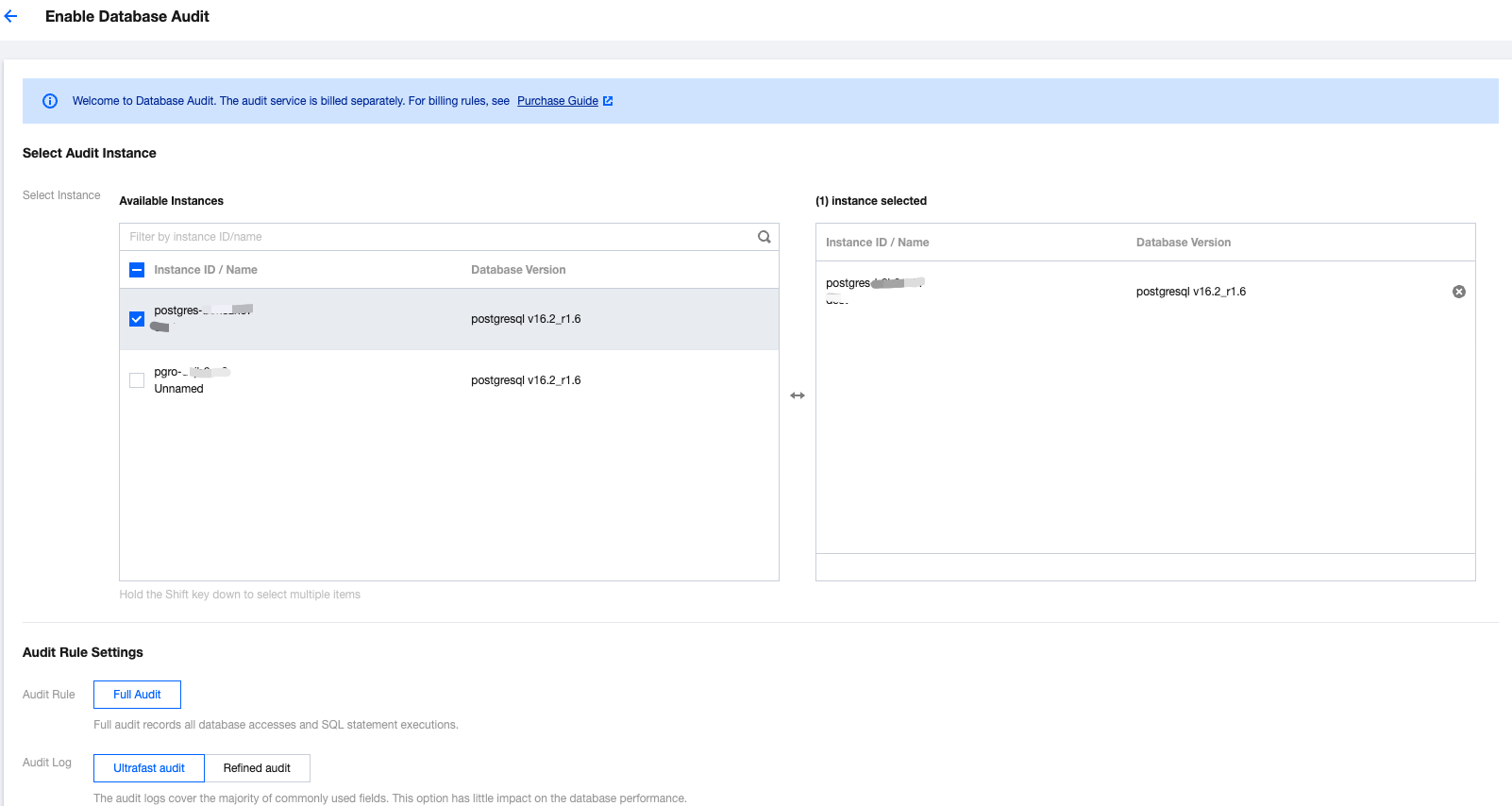
5.2 Audit Rule Settings
Under Audit Rule Settings, currently, only Full Audit is supported. In the Full Audit mode, the system records all access to the database and the execution of SQL statements. Audit logs support Fast Audit and Detailed Audit. For details, see Audit service description. After setting the audit rules, you may proceed to the Audit Service Settings.
5.3 Audit Service Settings
Under Audit Service Settings, you need to set Log Retention Period and Ultra-High-Performance Storage/Infrequent Access Storage Duration, read and check Tencent Cloud Service Agreement, and then click OK to activate the audit service.
Parameter | Description |
Log Retention Period | Setting the retention period of audit logs. Unit: day. Offering selections of 7, 30, 90, 180, 365, 1090, 1825 days. |
Ultra-High-Performance Storage Duration | Ultra-high-performance storage represents an ultra high performance storage medium with the best query performance. Unit: day. After setting the Storage Duration, audit data within the specified duration will be stored in ultra-high-performance storage. When data exceeds its specified period in ultra-high-performance storage, it will automatically transition to infrequent access storage. Different storages support the same audit capabilities, only differing in performance. For example: If the Log Retention Period is set to 30 days, and the Ultra-High-Performance Storage Duration is set to 7 days, then the Infrequent Access Storage Duration defaults to 23 days. |
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No
Feedback

