移动应用安全(Mobile Application Security)针对移动应用普遍存在的破解、篡改、重打包等各类安全风险,提供Android应用加固、iOS源码混淆、SDK加固等多种加固技术,拥有丰富的行业经验,已服务于金融、互联网、车联网、物联网,运营商等多个行业。稳定、简单、有效,让移动安全建设不再是一种负担。
简介
产品特性

跨平台保护
覆盖Android、iOS平台,支持Android应用、iOS应用、SDK加固,Android应用支持APK格式、AAB格式、SO文件等多种格式文件的加固保护。

多种加固技术
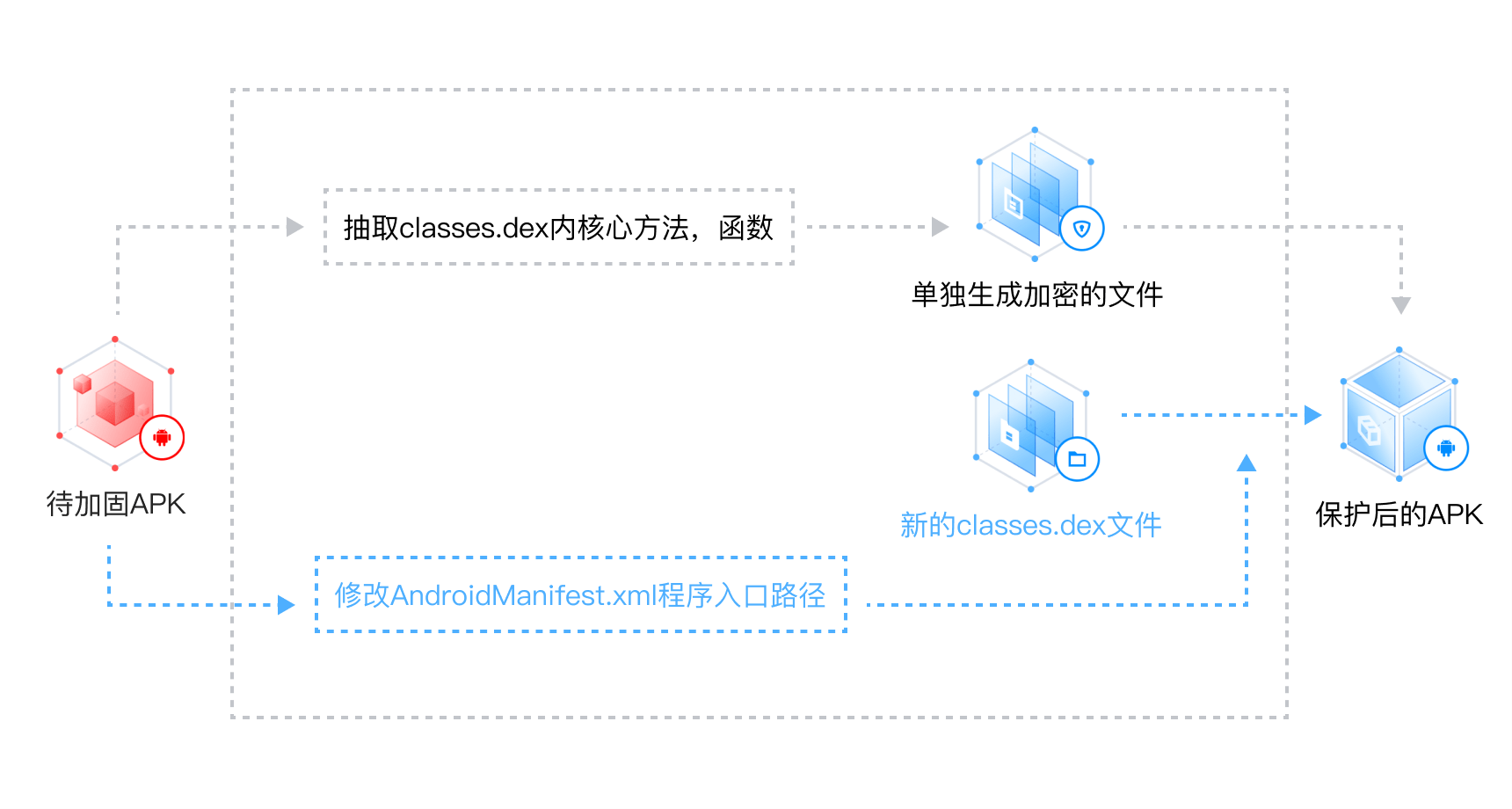
结合dex文件抽离加密、加壳保护技术,并在运行时创建互相监控的守护进程,保护应用静、动态的安全,防止逆向分析、重打包、恶意注入等问题,保障应用业务安全运行。

兼容性高、稳定性强
移动应用安全提供的安全能力可在复杂环境下稳定运行,兼容性高、崩溃率低,支持 Android 5.0以上全部机型。

接入成本低
使用成本低,无需二次开发。支持在线加固或本地工具加固。Android应用支持在线加固,支持命令行工具加固,iOS应用提供本地部署的Xcode编译工具,SDK文件提供命令行工具加固。

安全技术强
采用全新的DEX VMP虚拟化保护技术,将java指令转换为虚拟指令集,由转化后的指令集执行。同时VMP加固技术映射关系随机生成,整体技术同Android系统兼容性高、难于破解。
应用场景
国家政策对移动应用有明确的要求,App上线前需采用有效的加固技术,保障App安全,各地网安也不定期对应用市场的App进行安全扫描,未进行安全防护的App需要限期整改,否则存在被下架风险,此时移动安全建设的重点,是能够快速解决专业测评机构扫描出来的dex文件风险,腾讯加固为客户提供的代码保护方案,可以有效App被逆向、破解、篡改以及二次打包,在第一步就将绝大部分攻击者拒之门外,让企业安全防护化被动为主动。
常见问题
为什么要对应用程序进行加固
加固对性能有什么影响
加固对兼容性有什么影响



