Viewing and Handling of Attack Alarm Events
Last updated: 2025-12-24 11:26:05
Note:
The new version of Alarm Center is now available. This document only provides instructions for operations in the new version of Alarm Center. If you are currently using the old version of Alarm Center, you can click Switch to New Version in the upper right corner of Alarm Center to switch.
Attack alarm events intelligently merge user Intrusion Defense logs into clearer event entries based on dimensions such as attack type, attack method, and asset impact level, reducing interference from duplicate alarms and supporting trend analysis, alarm handling, and detailed viewing. Users can filter alarms based on multiple conditions and perform operations such as blocking, allowing, and isolating.
View Attack Alarm Trend
Attack alarm trend provides key metric statistics such as TOP 10 observed event IPs, affected assets, and so on, and visually presents event trends. It supports clicking quick filter to achieve attack tracing and handling closure. Through the visual summary of alarm information, users can conveniently perform statistical analysis and operational handling for attack events detected by the firewall. The statistical data is updated every 20 minutes.
1. Log in to the CFW console, in the left navigation, click Alarm Center > Attack Alert Event.
2. In the upper left corner of the attack alarm events page, select the time and analyze the security alarm events within that range.
3. In the attack alarm trend, you can view the following modules:
Module | Description | Interactive Feature |
Pending Events | Unhandled medium to high-risk observational alarms, reflecting the most urgent security risks currently. | Click number to filter related alarms; prioritize handling these. |
Host Compromise | Identifies and marks compromised assets, alerting to the risk of lateral movement within the private network. | Click number to filter related alarms; isolation operation is recommended. |
High-risk Alarms | Comprehensive assessment indicates significant risks to the business, requiring attention and prompt handling. | Click number to filter related alarms; promptly address the associated risks. |
Trend Chart of Attack Alarms | A line chart displays the trend of the number of alarms for "observe" and "intercept" actions over time. | Supports toggling the legend display with a click to assist in analyzing attack peak periods. |
Monitor TOP 10 Event IPs | TOP Statistics of Attacking IPs in Observed Events. | Click IP to quick copy. Click bar chart to enable quick filtering. |
TOP 10 Affected Assets | TOP Statistics of Affected Assets in All Attacks Except Those of the "Malicious IP address Attack" Type. | Click ID to quick copy. Click bar chart to enable quick filtering. |
Handle Alarm Events
The alarm list supports filtering alarm events of attacks by multiple conditions such as event severity (High/Medium/Low risk), traffic direction, and attack outcome. Users can perform operations like block, isolate, allowlist, or ignore on individual or batch alarms within the last 7 days, and correlate with Log Auditing to trace attack details.
Note:
The Alarm Center only supports operations on alarm events within the last 7 days.
After the specified target is disposed of, the status will be updated to "Disposed" and simultaneously moved to the corresponding alarm events that are disposed.
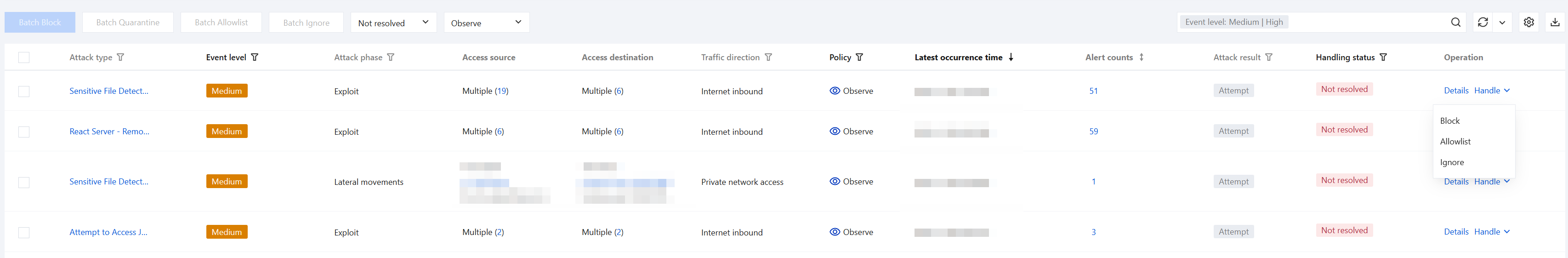
Feature Category | | |
Filter and Search | Quick Filter | Supports quick filtering of alarms by disposition status and protection action. |
| Advanced Search | Supports combined search with multiple conditions such as IP address, instance ID, event severity, and attack phase. Multiple keywords are separated by a vertical bar "|". |
| Customize List Fields | Attack type, access source, and access destination are fixedly displayed, while other fields (such as time of first occurrence and firewall type) can be customized for display. |
| Custom List Export | Supports full export or export of alarm events within the currently selected time range based on search conditions. |
Disposition Action | Block | Add the specified external IP address to the Intrusion Defense-Blocklist to block all its access requests. |
| Quarantine | Automatically deploys Enterprise Security Group blocking rules to intercept network access in specified directions for designated assets. This may cause network disconnection and should be used with caution. |
| Allowlist | Add the IP address to the Intrusion Defense-allowlist policy list, and it will no longer be detected by Intrusion Defense. |
| Ignore | Mark the alarm as "Ignored". The same attack event on the same day will not trigger alarms again and will not be counted in the statistics of the attack alarm trend. |
View alarm events. | Alarm List | In the alarm list, you can view relevant information about alarm events, including Attack Type, Event Severity, Attack Phase, Source, Destination, Traffic Direction, Policy, Time of First Occurrence, Time of Recent Occurrence, Alarm Count, Detection Source, Firewall Type, Attack Result, Alarm Category, and Handling Status. |
| View details. | In the alarm list, click the details in the operation column to view the details of the alarm event. AI Analysis of Events Event Summary: Analyze attack methods and potential risks. Disposition Recommendations: Provide operational guidance. Basis for Inference: Explains the logic for determining event severity. Details Feature Module Basic Information: Displays attack type, event severity, first/recent occurrence time, and so on. payload Information: Displays details of the attack request. Source Perspective: Displays IP address of the attack source, asset type, region, and associated access destinations. Destination Perspective: Displays affected asset IDs, private IP addresses, and associated access sources. |
Achieve More Precise Alarm Analysis
When user assets enable Network Detection and Response, the Alarm Center dynamically adjusts event severity based on attack context (such as attack outcome, URI validity, and so on), making levels of alarm events more objectively reflect actual risks and significantly reducing false positives. Simultaneously, additional relevant information is available in alarm details to help you rapidly identify and handle genuine high-risk incidents, enhancing efficiency of security operations. For detailed information about Network Detection and Response, see Network Detection and Response Switch.
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No
Feedback

