service or systemctl command on a Linux instance, the command line does not return any error message, but the service cannot run properly, and an error message similar to the following is displayed in the secure log:secure log of the client or server:sshd_config as instructed in Steps.sshd_config configuration file with VIM editor.vim /etc/ssh/sshd_config
#) at the beginning of each line to comment them out.AllowUsers root testDenyUsers testDenyGroups testAllowGroups root
systemctl restart sshd.service
service sshd restart
Permission denied (publickey,gssapi-keyex,gssapi-with-mic).sshd[10826]: Connection closed by xxx.xxx.xxx.xxx.Disconnected:No supported authentication methods available.
PasswordAuthentication parameter and disables the password login.sshd_config as instructed in Steps.PasswordAuthentication parameter and restart the SSH service.sshd_config configuration file with VIM editor.vim /etc/ssh/sshd_config
PasswordAuthentication no to PasswordAuthentication yes.systemctl restart sshd.service
service sshd restart
/etc/hosts.allow and /etc/hosts.deny files. You can set the trusted hosts in the hosts.allow file, and deny all other hosts in the hosts.deny file. The Deny policy can be set as follows:in.sshd:ALL # Deny all SSH connectionsin.sshd:218.64.87.0/255.255.255.128 # Deny SSH connections ranging from 218.64.87.0 to -127.ALL:ALL # Deny all TCP connections
sudo iptables -L --line-number
sshd_config configuration file with VIM editor.vim /etc/ssh/sshd_config
MaxStartups value, which specifies the maximum number of connections allowed. If many connections are required to establish in a short period, adjust the value as needed.service sshd restart
PermitRootLogin configuration.PermitRootLogin parameter in sshd_config as instructed in Steps./usr/sbin/sestatus -v
enabled as shown below is returned, the service is enabled. The disabled response indicates that the service is disabled.SELinux status: enabled
setenforce 0
sed -i 's/SELINUX=enforcing/SELINUX=disabled/' /etc/selinux/config
enforcing status.sshd_config configuration file with VIM editor.vim /etc/ssh/sshd_config
PermitRootLogin no to PermitRootLogin yes.sshd_config, the root user is allowed to log in by default.service sshd restart
sshd_config as instructed in Steps.MaxAuthTries parameter for the password reset policy, and restart the SSH service.sshd_config configuration file with VIM editor.vim /etc/ssh/sshd_config
MaxAuthTries 5
sshd_config configuration file.#) at the beginning of the line to comment it out.MaxAuthTries <number of incorrect password attempts allowed>
service sshd restart
secure log or directly returned:libcrypto.so.10 library file exception.libcrypto.so.10 library file information.ll /usr/lib64/libcrypto.so.10
/usr/lib64/libcrypto.so.10 is the soft link of the libcrypto.so.1.0.2k library file.lrwxrwxrwx 1 root root 19 Jan 19 2021 /usr/lib64/libcrypto.so.10 -> libcrypto.so.1.0.2k
libcrypto.so.1.0.2k library file information.ll /usr/lib64/libcrypto.so.1.0.2k
-rwxr-xr-x 1 root root 2520768 Dec 17 2020 /usr/lib64/libcrypto.so.1.0.2k
libcrypto.so.1.0.2k file.find / -name libcrypto.so.1.0.2k
cp <absolute path of the library file obtained in the step 1> /usr/lib64/libcrypto.so.1.0.2k
chmod 755 /usr/lib64/libcrypto.so.1.0.2k
chown root:root /usr/lib64/libcrypto.so.1.0.2k
ln -s /usr/lib64/libcrypto.so.1.0.2k /usr/lib64/libcrypto.so.10
service sshd start
libcrypto.so.1.0.2k library file of a normal CVM to the \\tmp directory of the target CVM using FTP.\\tmp is used in this example. You can replace with the actual directory.cp /tmp/libcrypto.so.1.0.2k /usr/lib64/libcrypto.so.1.0.2k
chmod 755 /usr/lib64/libcrypto.so.1.0.2k
chown root:root /usr/lib64/libcrypto.so.1.0.2k
ln -s /usr/lib64/libcrypto.so.1.0.2k /usr/lib64/libcrypto.so.10
service sshd start
secure log:FAILED.fatal: Cannot bind any address.address family must be specified before ListenAddress.
AddressFamily. This parameter specifies the protocol suite used at runtime. If only IPv6 is configured here, but the IPv6 is not enabled or invalidly configured in the system, this problem may occur.sshd_config as instructed in Steps.AddressFamily parameter and restart the SSH service.sshd_config configuration file with VIM editor.vim /etc/ssh/sshd_config
AddressFamily inet6
#) at the beginning of the line to comment it out. AddressFamily inet
AddressFamily parameter takes effect only after being configured before ListenAddress.servicesshd restart
secure log:/etc/ssh/sshd_config: line 2: Bad configuration options:\\\\/etc/ssh/sshd_config: terminating, 1 bad configuration options
sshd_config configuration file as instructed below./etc/ssh/sshd_config with VIM editor by referring to the correct configuration file of another instance./etc/ssh/sshd_config library file of a normal CVM to the \\tmp directory of the target CVM using FTP.\\tmp is used in this example. You can replace with the actual directory.cp /tmp/sshd_config /etc/ssh/sshd_config
chmod 600 /etc/ssh/sshd_config
chown root:root /etc/ssh/sshd_config
service sshd start
rpm -e openssh-server
yum install openssh-server
service sshd start
sshd_config as instructed in Steps.sshd_config configuration file with VIM editor.vim /etc/ssh/sshd_config
UseDNS yes
#) at the beginning of the line to comment it out.servicesshd restart
secure log of the client or server:600, and if other permissions such as 777 are configured, then other users also have permissions to read or modify the file. In this case, the SSH service will deem that the configuration involves security risks, which causes client connection failures. The troubleshooting process is as follows:cd /etc/ssh/
chmod 600 ssh_host_*
chmod 644 *.pub
ll command to view the file permission. If the following result is returned, the file permission is normal.total 156-rw-------. 1 root root 125811 Nov 23 2013 moduli-rw-r--r--. 1 root root 2047 Nov 23 2013 ssh_config-rw------- 1 root root 3639 May 16 11:43 sshd_config-rw------- 1 root root 668 May 20 23:31 ssh_host_dsa_key-rw-r--r-- 1 root root 590 May 20 23:31 ssh_host_dsa_key.pub-rw------- 1 root root 963 May 20 23:31 ssh_host_key-rw-r--r-- 1 root root 627 May 20 23:31 ssh_host_key.pub-rw------- 1 root root 1675 May 20 23:31 ssh_host_rsa_key-rw-r--r-- 1 root root 382 May 20 23:31 ssh_host_rsa_key.pub
ssh_host_* file.cd /etc/ssh/
ll
ssh_host_* file exists.total 156 -rw-------. 1 root root 125811 Nov 23 2013 moduli -rw-r--r--. 1 root root 2047 Nov 23 2013 ssh_config -rw------- 1 root root 3639 May 16 11:43 sshd_config -rw------- 1 root root 672 May 20 23:08 ssh_host_dsa_key -rw-r--r-- 1 root root 590 May 20 23:08 ssh_host_dsa_key.pub -rw------- 1 root root 963 May 20 23:08 ssh_host_key -rw-r--r-- 1 root root 627 May 20 23:08 ssh_host_key.pub -rw------- 1 root root 1675 May 20 23:08 ssh_host_rsa_key -rw-r--r-- 1 root root 382 May 20 23:08 ssh_host_rsa_key.pub
rm -rf ssh_host_*
sudo rm -r /etc/ssh/ssh*key
ll command to check whether the file has been deleted successfully. If the following result is returned, it has been deleted successfully.total 132-rw-------. 1 root root 125811 Nov 23 2013 moduli-rw-r--r--. 1 root root 2047 Nov 23 2013 ssh_config-rw------- 1 root root 3639 May 16 11:43 sshd_config
service sshd restart
sudo dpkg-reconfigure openssh-server
ll command to check whether the ssh_host_* file has been generated successfully. If the following result is returned, it has been generated successfully.total156-rw-------.1root root125811Nov232013moduli -rw-r--r--.1root root2047Nov232013ssh_config -rw-------1root root3639May1611:43 sshd_config -rw-------1root root668May2023:16 ssh_host_dsa_key -rw-r--r--1root root590May2023:16 ssh_host_dsa_key.pub -rw-------1root root963May2023:16 ssh_host_key -rw-r--r--1root root627May2023:16 ssh_host_key.pub -rw-------1root root1671May2023:16 ssh_host_rsa_key -rw-r--r--1root root382May2023:16 ssh_host_rsa_key.pub
/var/empty/sshd directory/var/empty/sshd directory. ll -d /var/empty/sshd/
drwx--x--x. 2 root root 4096 Aug 9 2019 /var/empty/sshd/
/var/empty/sshd directory has the permission 711 and is a root user in the root group by default.chown -R root:root /var/empty/sshd
chmod -R 711 /var/empty/sshd
systemctl restart sshd.service
/etc/securetty file/etc/securetty file.ll /etc/securetty
-rw-------. 1 root root 255 Aug 5 2020 /etc/securetty
/etc/securetty file has the permission 600 and is a root user in the root group by default.chown root:root /etc/securetty
chmod 600 /etc/securetty
systemctl restart sshd.service
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY!Someone could be eavesdropping on you right now (man-in-the-middle attack)!It is also possible that the RSA host key has just been changed.The fingerprint for the RSA key sent by the remote host isae:6e:68:4c:97:a6:91:81:11:38:8d:64:ff:92:13:50.Please contact your system administrator.Add correct host key in /root/.ssh/known_hosts to get rid of this message.Offending key in /root/.ssh/known_hosts:70RSA host key for x.x.x.x has changed and you have requested strict checking.Host key verification failed.
The host key of `X.X.X.X` (port: XX) is not the same as the one saved in the host key database. The host key has been changed or someone is attempting to eavesdrop this connection. If you are not sure, we recommend you cancel this connection.
known_hosts file of the corresponding account.vi ~/.ssh/known_hosts
1.14.xxx.xxskowcenw96a/pxka32sa....dsaprgpck2wa22mvi332ueddw...
secure log:/etc/pam.d directory; for example, the configuration file of the login command is /etc/pam.d/login, where you can configure specific policies. cat command to view the corresponding PAM configuration file as described below:File | Feature Description |
/etc/pam.d/login | Configuration file of the console (VNC) |
/etc/pam.d/sshd | Configuration file of SSH login |
/etc/pam.d/system-auth | Global configuration file of the system |
auth required pam_listfile.soitem=usersense=allowfile=/etc/ssh/whitelistonerr=fail
#) at the beginning of the line to comment it out.# auth required pam_listfile.so item=user sense=allow file=/etc/ssh/whitelist onerr=fail
secure log:pam_succeed_if(sshd:auth): requirement "uid >= 1000" not met by user "root".
1000 from logging in.cat command to view the corresponding PAM configuration file as described below:File | Feature Description |
/etc/pam.d/login | Configuration file of the console (VNC) |
/etc/pam.d/sshd | Configuration file of SSH login |
/etc/pam.d/system-auth | Global configuration file of the system |
auth required pam_succeed_if.so uid >= 1000
#) at the beginning of the line to comment it out. We recommend you back up the configuration before modifying it as needed.auth required pam_succeed_if.so uid <= 1000 # Modify the policy# auth required pam_succeed_if.so uid >= 1000 # Comment out the relevant configuration
cat /etc/pam.d/system-auth
cat /etc/pam.d/login
cat /etc/pam.d/sshd
#) at the beginning of the line to comment it out. This document uses commenting the configuration out as an example. After the modification, the relevant configuration is as shown below:#auth required pam_tally2.so deny=3 unlock_time=5#auth required pam_tally.so onerr=fail no_magic_root#auth requeired pam_tally2.so deny=5 lock_time=30 unlock_time=10 even_deny_root root_unlock_time=10
pam_tally2 module is used here; if it is not supported, use the pam_tally module. The settings may vary by PAM version. For more information on how to use a specific module, please see the corresponding rules.pam_tally2 and pam_tally modules can be used for account lockout policy control. They differ in that the former has the automatic unlock time feature.even_deny_root indicates to restrict the root user.deny indicates to set the maximum number of consecutive incorrect login attempts for general users and root users. After it is exceeded, the user will be locked.unlock_time indicates to unlock general users after they are locked for a specified period of time in seconds.root_unlock_time indicates to unlock root users after they are locked for a specified period of time in seconds.pam_tally2 -u root # View the number of consecutive incorrect password attempts made by the root user
pam_tally2 -u root -r # Clear the number of consecutive incorrect password attempts made by the root user
authconfig --disableldap --update # Update the PAM authentication record
secure log:login: Module is unknown.login: PAM unable to dlopen(/lib/security/pam_limits.so): /lib/security/pam_limits.so: cannot open shared object file: No such file or directory.
/etc/pam.d directory; for example, the configuration file of the login command is /etc/pam.d/login, where you can configure specific policies as shown below:File | Feature Description |
/etc/pam.d/login | Configuration file of the console (VNC) |
/etc/pam.d/sshd | Configuration file of SSH login |
/etc/pam.d/system-auth | Global configuration file of the system |
/etc/pam.d/sshd and /etc/pam.d/system-auth files. If /etc/pam.d/login is exceptional, please submit a ticket for assistance.cat [absolute path of the corresponding PAM configuration file]
/lib/security/pam_limits.so.session required pam_limits.so
/lib/security/pam_limits.so path is incorrect.ll /lib/security/pam_limits.so
pam_limits.so module. The correct path should be /lib64/security on a 64-bit Linux instance. The modified configuration information should be as shown below:session required /lib64/security/pam_limits.so
ps aux | grep udev-fall
kill -9 [virus process ID]
chkconfig udev-fall off
for i in ` find / -name "udev-fall"`;do echo '' > $i && rm -rf $i;done
systemctl restart sshd.service
service or systemctl command on a Linux instance, the command line does not return any error message, but the service cannot run properly, and an error message similar to the following is displayed in the secure log:sshd.service: main process exited, code=exited, status=203/EXEC.init: ssh main process (1843) terminated with status 255.
PATH environment variable is exceptional or the relevant files of the SSH software package are removed.PATH environment variable or reinstall the SSH software package as instructed in Steps.echo $PATH
PATH environment variable with its default value as shown below:/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin:/root/bin
export PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin:/root/bin
find / -name sshd
/usr/sbin/sshd
servicesshd restart
-bash: fork: retry: Resource temporarily unavailable.pam_limits(sshd:session): could not sent limit for 'nofile':operaton not permitted.Permission denied.
limits.conf file to permanently change the ulimit system environment limit based on the operating system version as instructed in Steps.X-nproc.conf file is used to manage the ulimit system environment limits. The steps for versions below and above CentOS 6 are differentiated here. The prefix number of the X-nproc.conf file varies by system version; for example, it is 90-nproc.conf on CentOS 6 and 20-nproc.conf on CentOS 7. Please proceed based on the actual environment.cat/etc/security/limits.conf
soft, hard, and -. soft is the <value> of the current system that has taken effect.hard is the maximum <value> set in the system.soft cannot be greater than that of hard. - indicates to set the values of soft and hard at the same time.core limits the kernel file size.rss is the maximum resident set size.nofile is the maximum number of opened files.noproc is the maximum number of processes.limits.conf file to comment out, modify, or delete the resource type code limited by the noproc or nofile parameter.
We recommend you run the following command to back up the limits.conf file before modifying it.cp -af /etc/security/limits.conf /root/limits.conf_bak
cat/etc/security/limits.d/20-nproc.conf
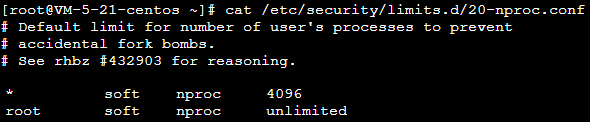
/etc/security/limits.d/20-nproc.conf file as instructed in Below CentOS 6. We recommend you back up the file before doing so.secure log:cat /etc/passwd | grep test
nologin.test:x:1000:1000::/home/test:/sbin/nologin
/etc/passwd file. We recommend you back up the file before doing so.vim /etc/passwd
/sbin/nologin to /bin/bash. Feedback