Secrets Manager (SSM) is a credential management service that enables you to easily create, retrieve, update and delete credentials throughout their lifecycle. You can use SSM together with resource-level role authorization to manage sensitive credentials. With SSM, users and applications can retrieve credentials by calling the Secrets Manager API, thereby effectively avoiding security risks from hardcoding sensitive information in plain text.
Secrets Manager
Easily manage, retrieve and store encrypted database credentials, API keys and other secrets

With SSM, hardcoded credentials are deleted from the application source code and replaced by calls to Secrets Manager API, so you can dynamically retrieve and manage credentials programmatically.

Credentials are encrypted and stored in SSM using our Key Management Service (KMS), and the encryption key is generated and protected by the hardware security module (HSM) authenticated by a third party. When a credential is retrieved from SSM, it will be securely transferred to the local server over TLS.

SSM helps you rotate and manage your secrets. It can routinely update sensitive credentials and automatically sync the update across all applications, ensuring that your applications are using the latest version of your secrets and guaranteeing business continuity.

SSM is fully integrated with Cloud Access Management (CAM), so you can use the granular identity and access policies to ensure that only authorized users can access or modify credentials. In addition, you can bind policies to users or roles to specify the credentials that can be accessed by them.

SSM is integrated with CloudAudit and provides monitoring, compliance check, and auditing services for your Tencent Cloud account. It can record all credential management operations and usage.

SSM utilizes cluster deployment and a distributed database storage system for data storage and disaster recovery. You can create the same credentials in multiple regions to implement cross-region disaster recovery for credentials.
Enterprise-grade Credential Management
Authorization and Monitoring
Security Compliance
Enterprise-grade Credential Management
Credential Retrieval
With SSM, hardcoded credentials are deleted from the application source code or configuration files and replaced by calls to Secrets Manager API, so you can dynamically retrieve and manage credentials programmatically. This prevents sensitive information from being leaked due to code or access issues.
Encrypted Credential Storage and Transfer
You can store various types of sensitive data in SSM as name-value pairs. The value part can contain up to 4,096 bytes of database connections, account passwords, IP ports, etc. SSM will use a CMK protected by KMS as the encryption key to encrypt the stored sensitive data. When a credential is requested, it will be securely transferred to the local server over TLS.
Application-Layer Credential Rotation
SSM helps you rotate and manage your secrets. It can routinely update the credential content in the system and automatically sync the credential update across all applications, ensuring that your applications are using the latest version of your secrets and guaranteeing business continuity.
Authorization and Monitoring
Resource-level Access Authorization
SSM is fully-integrated with CAM, so you can securely and granularly manage the access permissions of sensitive credentials. You can create SSM users or roles in CAM, specify the users that can access specified credentials in SSM, and manage the permissions of credential-related operations such as viewing, modification, and deletion using fine-grained access policies.
Refined Regulation and Audit
SSM is integrated with CloudAudit and provides monitoring, compliance check, and auditing services for your Tencent Cloud account. It can record all credential management operations and usage, including details such as users, time, dates, and API operations. These records can be transferred to your specified COS bucket.
Security Compliance
Compliance Requirements
SSM works with KMS, which uses an HMS authenticated by a third party to generate and protect keys, meeting the regulation and compliance requirements.
High-availability Disaster Recovery and Backup
SSM utilizes cluster deployment and a distributed database storage system for data storage and disaster recovery. You can create the same credentials in multiple regions to implement cross-region disaster recovery for credentials. When a cluster fails, you only need to switch the region.
Credential Retrieval
With SSM, hardcoded credentials are deleted from the application source code or configuration files and replaced by calls to Secrets Manager API, so you can dynamically retrieve and manage credentials programmatically. This prevents sensitive information from being leaked due to code or access issues.
Encrypted Credential Storage and Transfer
You can store various types of sensitive data in SSM as name-value pairs. The value part can contain up to 4,096 bytes of database connections, account passwords, IP ports, etc. SSM will use a CMK protected by KMS as the encryption key to encrypt the stored sensitive data. When a credential is requested, it will be securely transferred to the local server over TLS.
Application-Layer Credential Rotation
SSM helps you rotate and manage your secrets. It can routinely update the credential content in the system and automatically sync the credential update across all applications, ensuring that your applications are using the latest version of your secrets and guaranteeing business continuity.
Resource-level Access Authorization
SSM is fully-integrated with CAM, so you can securely and granularly manage the access permissions of sensitive credentials. You can create SSM users or roles in CAM, specify the users that can access specified credentials in SSM, and manage the permissions of credential-related operations such as viewing, modification, and deletion using fine-grained access policies.
Refined Regulation and Audit
SSM is integrated with CloudAudit and provides monitoring, compliance check, and auditing services for your Tencent Cloud account. It can record all credential management operations and usage, including details such as users, time, dates, and API operations. These records can be transferred to your specified COS bucket.
Compliance Requirements
SSM works with KMS, which uses an HMS authenticated by a third party to generate and protect keys, meeting the regulation and compliance requirements.
High-availability Disaster Recovery and Backup
SSM utilizes cluster deployment and a distributed database storage system for data storage and disaster recovery. You can create the same credentials in multiple regions to implement cross-region disaster recovery for credentials. When a cluster fails, you only need to switch the region.
Technical Application
It is necessary for an agile business to utilize numerous sensitive account information such as tokens, certificates, SSH keys, and API keys. You can use SSM to easily manage, store and retrieve these sensitive credentials throughout their lifecycle.
Use Cases
Lifecycle management operations such as the encryption, storage, and querying of sensitive configuration information and credentials of multiple applications.
Challenges
A high number of sensitive credentials are distributed among different departments and systems, management is unorganized and lack a centralized credential management tool.
Solution
You can use SSM together with CAM and CloudAudit to manage the full lifecycle of credentials. Sensitive credentials can be created, stored and managed via the console, SDK or TCCLI.
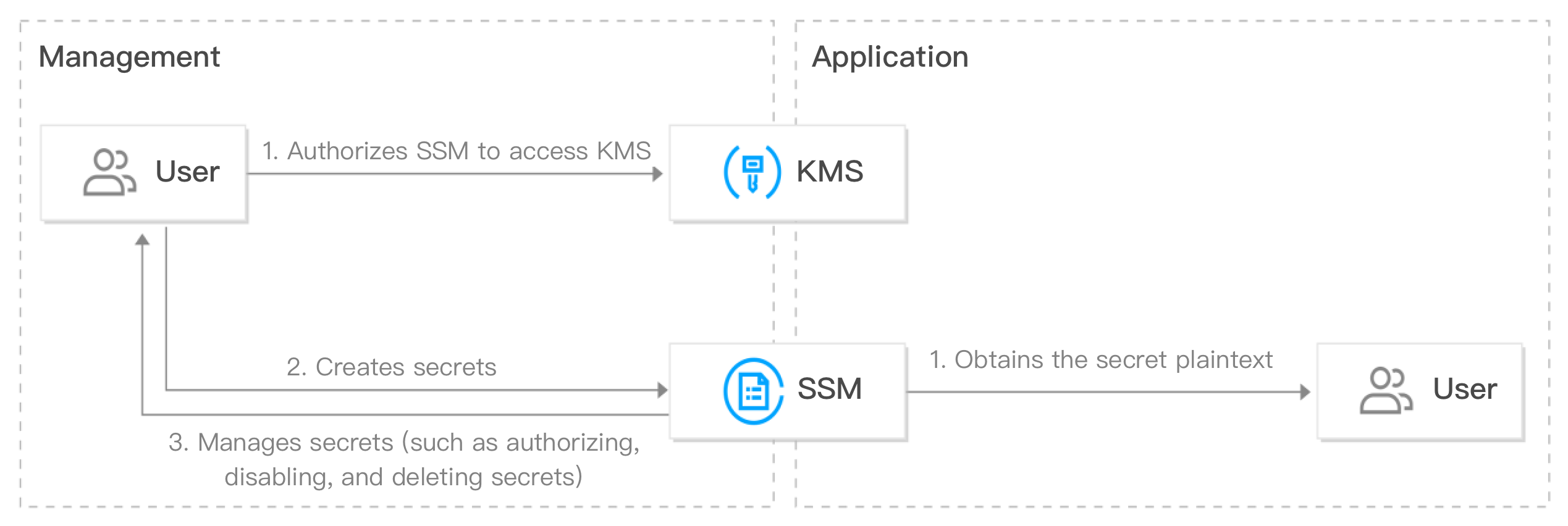
Technical Application
Generally, any digital certificates for authentication that are created when you access an application or a service, such as passwords, tokens, certificates, SSH keys, API keys, or other confidential information, will be directly embedded into the application configuration file in plaintext, which is inherently insecure. With SSM, you can effectively avoid risks such as hardcoding sensitive data.
Use Cases
Management of credentials such as database credentials, API keys, and account passwords.
Challenges
Hardcoding sensitive credential information and plaintext-based storage creates security risks.
Solution
You can replace hardcoded credentials (including passwords) in the code with calls to Secrets Manager API to dynamically retrieve credentials programmatically. This ensures that your keys will not be disclosed to people who can view your code, as the code will no longer store any sensitive information.
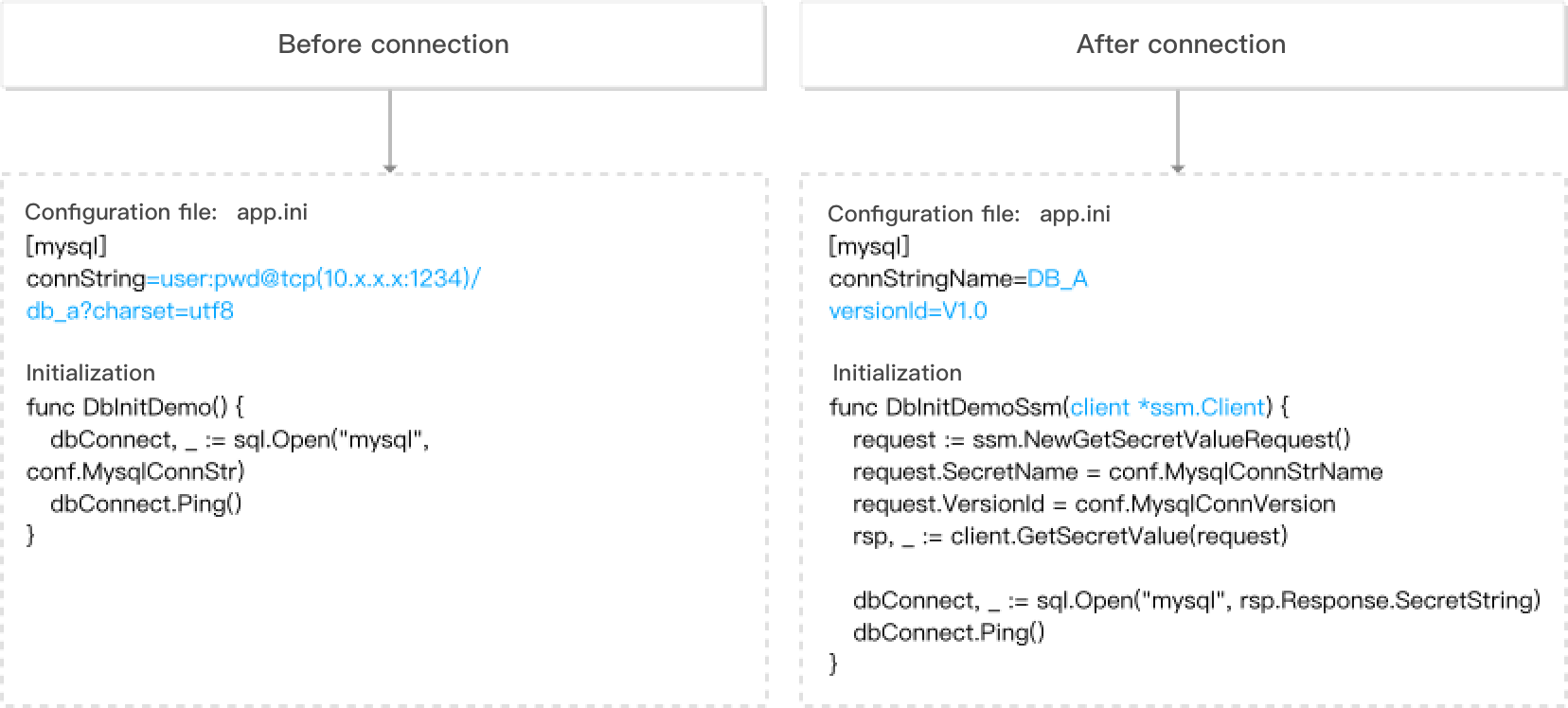
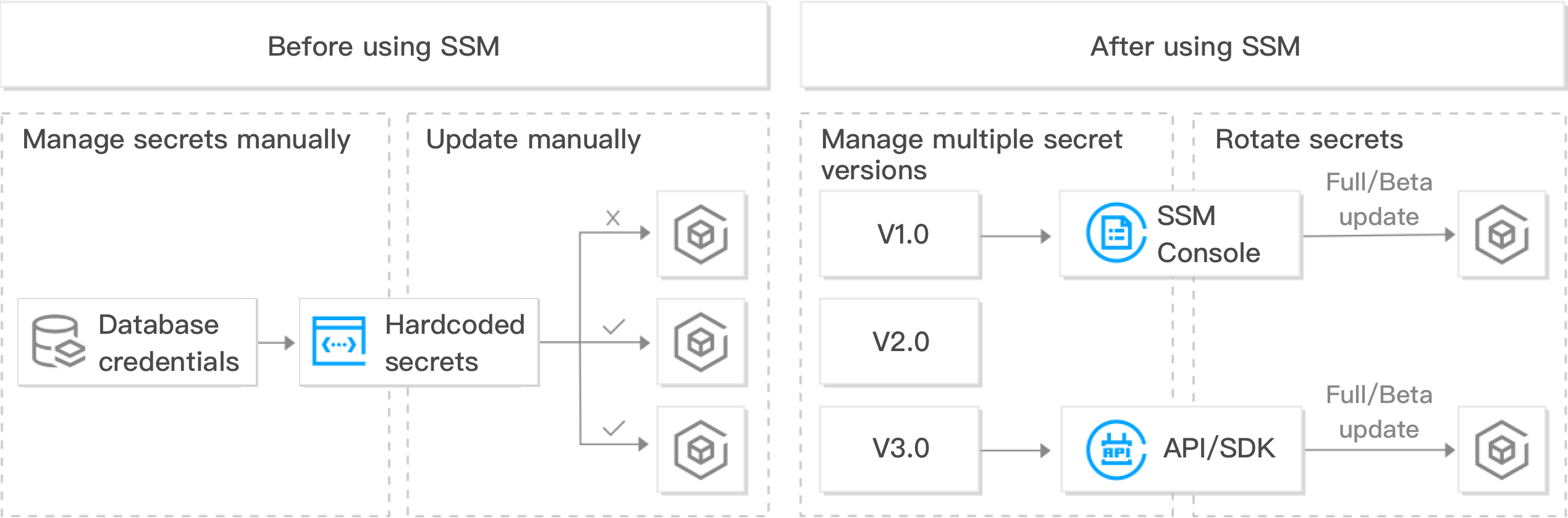
Technical Application
To improve system security, sensitive credentials need to be routinely updated.
Use Cases
Application-Layer credential rotation.
Challenges
Credentials needs to be updated and synced across multiple applications/configurations. If done manually, an application might be missed, which runs the risk of business interruptions.
Solution
You can update the credential in the SSM Console or via API. You can also select full or grayscale rotation to update the credential in all applications synchronously.
SSM is monthly pay-as-you-go. Fees consist of the credential storage fees and API call fees. Fees for the month are calculated, billed, and charged on the 3rd to 5th days of the following month. View more