Encrypted Traffic Detection
Last updated: 2025-12-19 15:53:24
Overview
Network Detection and Response has added encrypted traffic detection capability, supporting parsing and detecting encrypted traffic (such as HTTPS/TLS) for CVM assets and the public network traffic of GAAP assets, comprehensively enhancing visibility of full traffic and threat detection capability. Currently in beta version, only available to invited users. Non-invited users who wish to experience this feature can submit a ticket to apply for access. Users can learn from this chapter about the configuration and usage of this feature. This document uses CVM assets as an example to provide relevant operational instructions, and the same applies to GAAP assets operations.
Prerequisites
Users need to configure security group rules to authorize the probe to collect network traffic, meeting the data input requirements of Network Detection and Response.
Method 1: Configuration of the Enterprise Security Group
1. Log in to the Cloud Firewall console, choose Access Control > Enterprise Security Group (New).
2. On the Enterprise Security Group page, click Add Rule, and enter the rule information as required in the table.
Configuration Item | Set Value |
Access source IP address | 0.0.0.0/0 |
Access destination IP address | 9.9.9.199 |
Destination port | 47891,47892,47893 |
Protocol | UDP |
Policy | Allow |
Description | NDR allow rule |
3. Click Save, and the rule will be deployed to associated instances.
Method 2: Configuration of the Single Instance
1. Log in to the CVM console, and select Instances.
2. On the instance page, click the instance name that requires detection of encrypted traffic to be enabled.
3. On the instance details page, select Security Group, and click the Security Group ID/Name of the bound security group.
4. Click Add Rule, and fill in the rule information according to the requirements in the table.
Configuration Item | Set Value |
Type | Custom |
Target | 9.9.9.199 |
Protocol Port | UDP: 47891,47892,47893 |
Policy | Allow |
Remark | NDR allow rule |
5. Click OK, and the rule will be deployed to associated instances.
Scope of Application and Capability Description
Kernel Version Compatibility
Linux kernel version | Applicable | Not applicable |
Below 4.18 | Curl command Python version 3.8.15 and above | OpenSSL dynamic library Java program Golang program |
Greater than or equal to 4.18 | OpenSSL dynamic library Curl command Python version 3.8.15 and above GnuTLS dynamic library | Java program Golang program |
Specific Decryption Capability
Protocol compatibility: HTTPS, SMTPS, FTPS.
Algorithm support: TLS 1.2/1.3 (RSA, ECDHE, DHE).
Length: The maximum length of a single encrypted traffic packet supporting decryption is 64K.
Performance: 10Gbps (supports dynamic scaling).
Resource consumption
CVM Encrypted Traffic Detection
Under the traffic pressure of 100 new HTTPS sessions per second, the resource usage of the Agent for Encrypted Traffic Detection is as follows:
CPU usage: When continuously running at a rate of 100 new HTTPS sessions per second, single-core CPU usage is approximately 10%; it supports a maximum usage of 60%, corresponding to about 600 new HTTPS sessions per second.
Memory usage: Initial usage is 100MB, which increases with the number of new HTTPS sessions, up to a maximum of 500MB.
When CPU or memory usage exceeds the above limits, the Agent automatically suspends the "encrypted traffic analysis" feature (other basic features remain unaffected; the Agent will not cause interruptions to existing business connections but will not generate new encrypted traffic analysis results until resources recover). It attempts to resume analysis every 10 minutes automatically. If resource limits are still exceeded after recovery, the feature remains suspended until resources fall back within the threshold.
Encrypted Traffic Detection in Containers
After the container decryption feature is enabled, the system will create an Agent Pod for encrypted traffic detection in the **Workload > DaemonSet** section of the corresponding TKE. Its resource usage limits are as follows:
Overall limit: A single Agent Pod can occupy up to 50% of a single-core CPU and 500MB of memory.
Runtime characteristics:
Each node with encrypted traffic detection enabled will independently create a corresponding Agent Pod. The operation of this Pod will not affect the normal operation of other business Pods on the same node.
The container service platform enforces mandatory limits on CPU and memory usage for DaemonSet Pods. If a Pod's resource consumption still exceeds these limits (for example, due to abnormal conditions surpassing 50% CPU or 500MB memory), the platform will automatically terminate the Pod and recreate a new instance. This process does not affect other business Pods on the same node.
Enable Detection of Encrypted Traffic
You can go to Network Detection and Response > CVM or Public Network Traffic to enable/disable encrypted traffic detection for single, multiple, or all CVM assets.
Single CVM Asset
In the CVM asset list, the system has added an "Encrypted Traffic Detection" operation column for CVM asset types. You can flexibly control the encrypted traffic detection status of individual assets using the "Detect" or "Do Not Detect" options in this column:
When you select Detect: The endpoint probe Agent is deployed with one-click rapid deployment, requiring no manual installation, and the system automatically completes the configuration. The encrypted traffic detection feature will be enabled for this CVM asset, and the page will display the real-time detection status, which falls into the following scenarios:
No Prompt (Normal State): When no exception prompts are displayed, it indicates that encrypted traffic detection is functioning normally. The system has automatically deployed an endpoint probe Agent on your CVM node. This probe decrypts the HTTPS/TLS encrypted traffic for this asset and includes the decrypted plaintext traffic in the Network Detection and Response analysis scope.
Red alert (abnormal state): If an exception occurs in the detection feature, the page will display a red alert icon and exception message, indicating that the current detection is unavailable. The exception information and guidance include:
Exception Categories | Error Message | Solution |
Error in enabling the switch for detection | TAT agent not detected | |
| The current operating system type is not supported. | Please go to Network Detection and Response - Technical Solutions to confirm compatibility. |
| The server is temporarily unavailable. Please try again later. | Please wait 5 minutes and try again. If the issue persists, submit a ticket to contact technical support. |
Error during execution of detection | Terminal Agent abnormal | 1. The Agent network may be abnormal. Please check whether security groups allow access. 2. Operation of the Agent process may be abnormal. Please verify the operating system status. 3. If no abnormalities are detected, submit a ticket to contact technical support. |
Gray indicator (feature disabled state): When the main switch of Network Detection and Response is disabled, the encrypted traffic detection feature automatically stops, and the asset only detects plaintext traffic.
When you select Do Not Detect: The system will not enable detection of encrypted traffic for this CVM asset, performing only regular detection based on plaintext traffic.
Multiple Assets of CVM
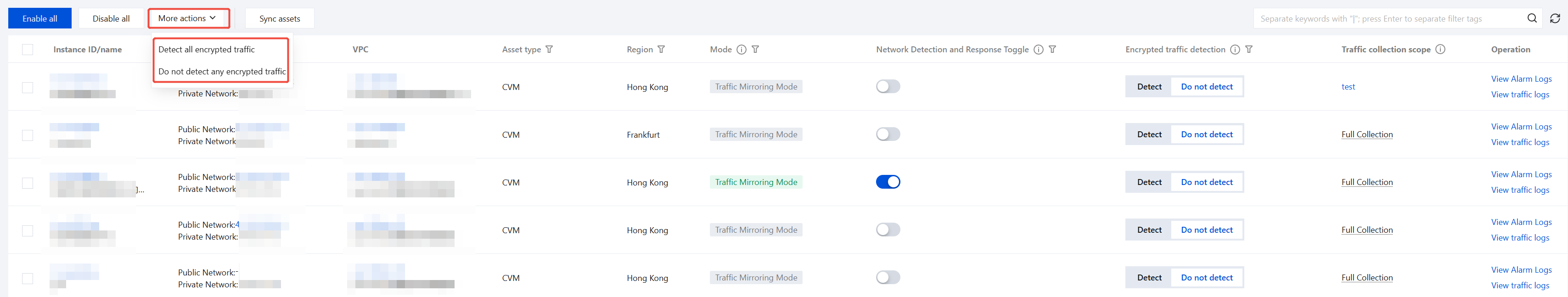
1. If you need to uniformly configure the status of encrypted traffic detection for all CVM assets, you can quickly do so via More Actions:
Detect all encrypted traffic: The system will automatically deploy endpoint probes on all CVM assets, decrypt their HTTPS/TLS encrypted traffic, and incorporate the decrypted traffic into the analysis scope of Network Detection and Response.
Do not detect any encrypted traffic: Endpoint probes on all CVM assets will stop decrypting encrypted traffic, performing only regular detection based on traffic transmitted in plaintext.
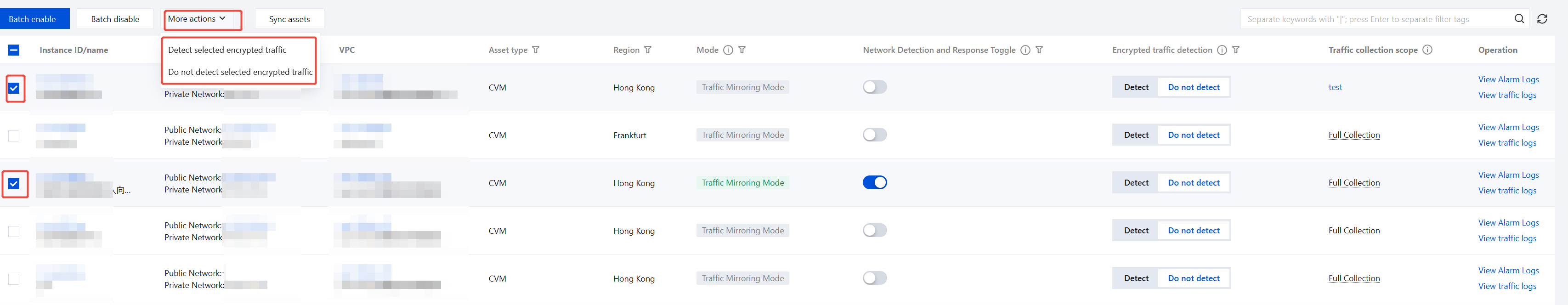
2. If you only need to uniformly configure the status of encrypted traffic detection for some CVM assets, you can do so by following the steps below:
2.1 In the CVM asset list, click More Actions.
2.2 Select the CVM assets that require configuration (multiple selection is supported).
2.3 Select batch operations:
Detect selected encrypted traffic: The system will automatically deploy endpoint probes on the selected CVM assets, decrypt their HTTPS/TLS encrypted traffic, and incorporate it into Network Detection and Responseanalysis.
Do not detect selected encrypted traffic: Endpoint probes on the selected CVM assets will stop decrypting encrypted traffic, detecting only plaintext traffic.
3. If you need to configure encrypted traffic detection for new assets, refer to Network Detection and Response switch.
Status Monitoring
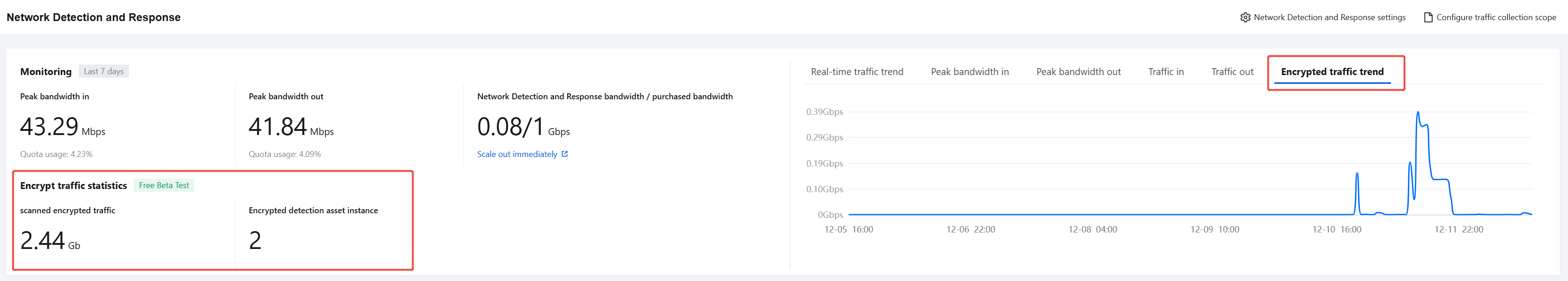
The system has added a dedicated statistics panel for encrypted traffic in the Monitoring module, helping you monitor the operating status and overall scale of encrypted traffic detection in real time. The core monitoring metrics include the following three items:
Statistics on cumulative parsed volume of encrypted traffic: Shows the total volume of encrypted traffic that has been parsed.
Count of Assets with Encrypted Traffic Detection: Displays the current number of CVM assets with encrypted traffic detection enabled.
Trend Chart of Cumulative Encrypted Traffic: Illustrates the dynamic changes in encrypted traffic parsing volume over the last seven days.
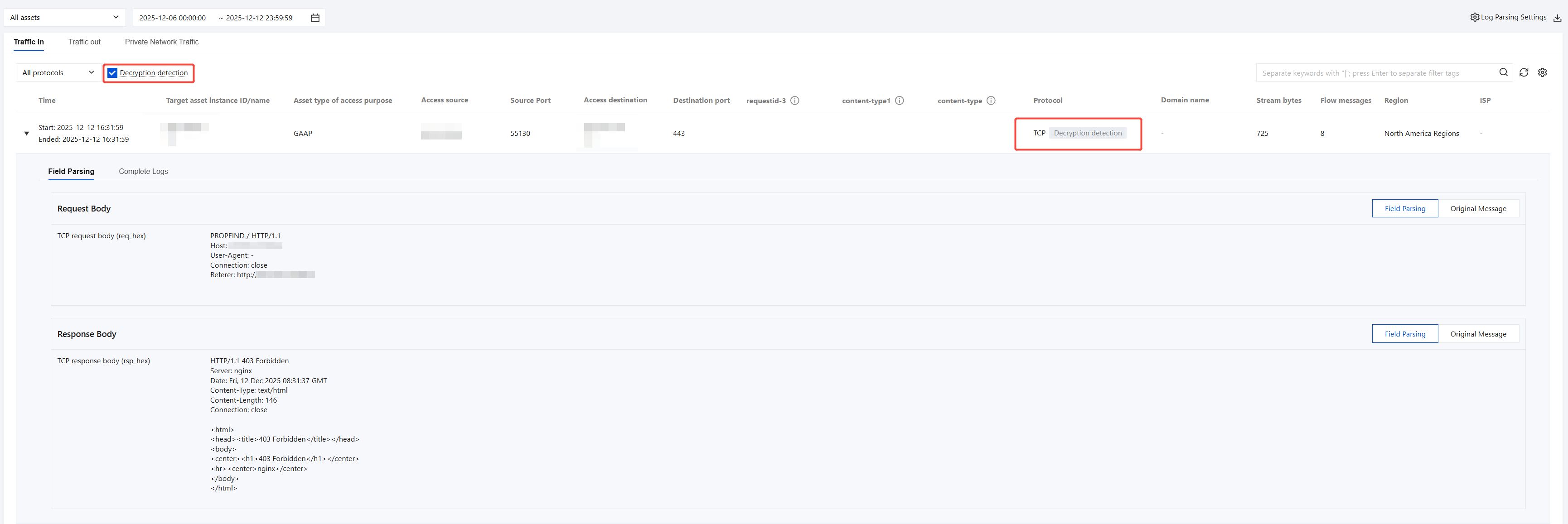
Encrypted Protocol Traffic Log
On the Log Auditing > Network Detection and Response Logs > Traffic Analysis Logs or Traffic Alarm Logs page, for traffic logs of encrypted protocols such as HTTPS, SMTPS, FTPS, the system will first restore the plaintext content (such as request headers, response bodies, and so on) and label it with Decryption Detection beside it; you can also select the Decryption Detection option to quickly filter and view all logs related to encrypted traffic detection.
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No
Feedback

