Server-side Encryption Overview
Last updated:2025-12-31 18:00:09
Overview
Cloud Object Storage (COS) encrypts your data at the object level before data is written to disks and automatically decrypts the data when you access it. Encryption and decryption are completed on servers. Server-side encryption can effectively protect static data.
Note:
This operation does not support setting encryption for Archive Type objects. If encryption is needed, please first perform restore on the object. Once recovery is completed, change the storage type to standard or low frequency, then you can proceed with encryption setting.
There is no difference in experience between accessing an encrypted object and accessing an unencrypted object, provided that you have access to the objects.
Server-side encryption encrypts object data but not object metadata, and does not cause any adjustment to object size.
When you list objects in a bucket, all objects will be listed, regardless of whether they are encrypted.
Use Cases
Private data storage: For private data storage, server-side encryption can encrypt stored data to protect your privacy and automatically decrypt the data when you access it.
Private data transfer: For private data transfer, COS supports deploying SSL certificates with HTTPS to implement encryption. An encryption layer will be established on the transfer linkage layer, ensuring that data will not be stolen or tampered with during transfer.
Encryption
COS supports multiple server-side encryption methods such as SSE-COS and SSE-C. You can choose the appropriate one to encrypt data stored in COS.
SSE-COS Encryption
SSE-COS encryption refers to server-side encryption with COS-managed keys. Tencent Cloud COS oversees the master keys and manages the data. Users can directly manage and encrypt their data through COS. SSE-COS employs multi-factor robust encryption, ensuring that each object is encrypted with a unique key, and the keys themselves are encrypted using periodically rotated master keys.
SSE-COS mode supports two encryption algorithms, AES256 and SM4. By default, AES256 is used. During object upload, you can specify the encryption algorithm through the server-side encryption header x-cos-server-side-encryption.
Note:
If you upload an object with a pre-signed URL, you cannot use SSE-COS encryption to encrypt it. You can only use the COS console or HTTP request header to specify server-side encryption.
SSE-KMS Encryption
SSE-KMS encryption is server-side encryption using a key managed by KMS. KMS is a security management service launched by Tencent Cloud, using a third-party-certified hardware security module (HSM) to generate and protect keys. KMS allows users to easily create and manage keys, meeting their key management needs for multiple applications and services, while satisfying regulatory and compliance requirements.
SSE-KMS mode supports two encryption algorithms, AES256 and SM4. By default, AES256 is used. During object upload, you can specify the encryption algorithm through the server-side encryption header x-cos-server-side-encryption-cos-kms-algorithm.
When using SSE-KMS encryption for the first time, you need to enable the KMS service. After the KMS service is enabled, the system will automatically create a default customer master key (CMK) for you. You can also create your own keys through the KMS console, and define key policies and use methods. KMS allows users to choose their own key material from KMS or external sources. For more information, see Create Key and Import External Key.
Note:
SSE-KMS only encrypts the object data, not its metadata.
Currently, SSE-KMS is only supported in the following regions: Beijing, Shanghai, Guangzhou, Shanghai Finance, Hong Kong (China), Bangkok, and Tokyo.
Using SSE-KMS encryption will incur an additional cost, which will be charged by KMS. For more information, see KMS Billing Overview.
Objects encrypted with SSE-KMS can only be accessed with a valid signature but not by anonymous users.
Details
If you have never used COS console for SSE-KMS encryption, and only used API for SSE-KMS encryption, you need to create a CAM role first:
1. Log in to the CAM Console and go to the Roles page.
2. Click Create Role and select Tencent Cloud Product Service as the role entity.
3. Select Cloud Object Storage as the service supporting the role, and click Next.
4. Search for the QcloudKMSAccessForCOSRole role policy and select it, and click Next.
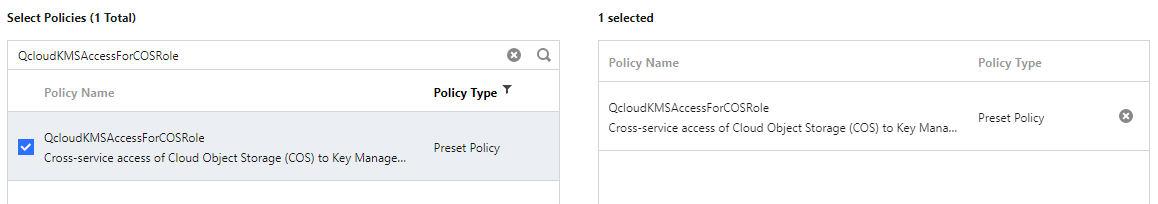
5. Set the role tag keys and values and click Next.
6. Enter the specified role name: COS_QCSRole.
Note:
In the CAM role list, the existing role name "COS_QCSRole" can continue to use, and its effective status remains unaffected.
7. Click Done to complete the process.
SSE-C Encryption
SSE-C encryption is server-side encryption with a custom key. The encryption key is provided by the user. When uploading an object, COS will use the user-provided encryption key to encrypt the user's data. SSE-C mode supports two encryption algorithms, AES256 and SM4. By default, AES256 is used. During object upload, you can specify the encryption algorithm through the server-side encryption header x-cos-server-side-encryption-customer-algorithm.
Note:
COS does not store your encryption key. Instead, it stores the HMAC value of the encryption key with random data added. This value is used to verify your request to access the object. COS cannot use the HMAC value with random data to derive the value of the encryption key or to decrypt the encrypted object. Therefore, if you lose the encryption key, you cannot get the object again.
Usage
Using the COS Console
Note:
SSE-C encryption can only be used via APIs but not the console.
SSE-COS and SSE-KMS encryption with SM4 algorithm is not supported currently on the console or through SDK invocation, and can only be used via API.
1. Log in to the COS Console.
2. In the left sidebar, click Bucket List to go to the bucket list page.
3. Find the bucket where the object is located and click the bucket name to enter the bucket management page.
4. In the left sidebar, select File List to go to the file list page.
5. Find the object you want to set encryption on and click Details on the right operation column.
6. In the "Server Encryption" column, select the corresponding encryption method and click Save.
7. Currently, the following two encryption methods are supported:
SSE-COS: Server-side encryption with COS-managed keys. For more information about SSE-COS, see Server-side Encryption Overview: SSE-COS.
SSE-KMS: Server-side encryption with KMS managed keys. You can use the default key or create your own key. For key information, please refer to Create a KMS Key. For more information about SSE-KMS, see Server-side Encryption Overview: SSE-KMS.
Note:
If you use SSE-KMS encryption for the first time, you must enable KMS service.
Objects encrypted with SSE-COS support anonymous access. Objects encrypted with SSE-KMS must be accessed with a valid signature and are not accessible by anonymous users.
To batch set encryption for multiple objects, select the objects and click More Operations > Modify Encryption Method at the top.
Using the REST API
For SSE-COS and SSE-KMS encryption, support the following API interfaces:
Note:
Note: If uploading object with a non-POST request, apply server-side encryption by providing the
x-cos-server-side-encryption-* header. For post requests, provide the x-cos-server-side-encryption-* field in the form field. For details, see POST Object.For SSE-C encryption, support the following API interfaces:
Note:
Note: If uploading object with a non-POST request, apply server-side encryption by providing the
x-cos-server-side-encryption-* header. For post requests, provide the x-cos-server-side-encryption-* field in the form field. For details, see POST Object.When making API requests for SSE-C encrypted objects via GET Object and HEAD Object, the
x-cos-server-side-encryption-* header is required to decrypt the specified object. For details, see Common Request Headers - SSE-C.You can call the manage object tag method in the SDK. For details, see the following SDK documentation for languages:
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No
Feedback

