- 产品动态
- 产品简介
- 购买指南
- 快速入门
- 操作指南
- 故障处理
- API 文档
- History
- Introduction
- API Category
- Making API Requests
- Cluster Security APIs
- SetCheckMode
- DescribeUserCluster
- DescribeUnfinishRefreshTask
- DescribeTaskResultSummary
- DescribeRiskList
- DescribeRefreshTask
- DescribeClusterSummary
- DescribeClusterDetail
- DescribeCheckItemList
- DescribeAffectedWorkloadList
- DescribeAffectedNodeList
- DescribeAffectedClusterCount
- CreateRefreshTask
- CreateClusterCheckTask
- CreateCheckComponent
- Network Security APIs
- UpdateNetworkFirewallPolicyYamlDetail
- UpdateNetworkFirewallPolicyDetail
- UpdateAndPublishNetworkFirewallPolicyYamlDetail
- UpdateAndPublishNetworkFirewallPolicyDetail
- DescribeNetworkFirewallPolicyYamlDetail
- DescribeNetworkFirewallPolicyStatus
- DescribeNetworkFirewallPolicyList
- DescribeNetworkFirewallPolicyDiscover
- DescribeNetworkFirewallPolicyDetail
- DescribeNetworkFirewallPodLabelsList
- DescribeNetworkFirewallNamespaceLabelList
- DescribeNetworkFirewallClusterRefreshStatus
- DescribeNetworkFirewallClusterList
- DescribeNetworkFirewallAuditRecord
- DeleteNetworkFirewallPolicyDetail
- CreateNetworkFirewallUndoPublish
- CreateNetworkFirewallPublish
- CreateNetworkFirewallPolicyDiscover
- CreateNetworkFirewallClusterRefresh
- ConfirmNetworkFirewallPolicy
- CheckNetworkFirewallPolicyYaml
- AddNetworkFirewallPolicyYamlDetail
- AddNetworkFirewallPolicyDetail
- AddAndPublishNetworkFirewallPolicyYamlDetail
- AddAndPublishNetworkFirewallPolicyDetail
- Security Compliance APIs
- ScanComplianceScanFailedAssets
- ScanCompliancePolicyItems
- ScanComplianceAssetsByPolicyItem
- ScanComplianceAssets
- ModifyCompliancePeriodTask
- InitializeUserComplianceEnvironment
- DescribeComplianceWhitelistItemList
- DescribeComplianceTaskPolicyItemSummaryList
- DescribeComplianceTaskAssetSummary
- DescribeComplianceScanFailedAssetList
- DescribeCompliancePolicyItemAffectedSummary
- DescribeCompliancePolicyItemAffectedAssetList
- DescribeCompliancePeriodTaskList
- DescribeComplianceAssetPolicyItemList
- DescribeComplianceAssetList
- DescribeComplianceAssetDetailInfo
- DeleteCompliancePolicyItemFromWhitelist
- DeleteCompliancePolicyAssetSetFromWhitelist
- DeleteComplianceAssetPolicySetFromWhitelist
- CreateExportComplianceStatusListJob
- CreateComplianceTask
- AddCompliancePolicyItemToWhitelist
- AddCompliancePolicyAssetSetToWhitelist
- AddComplianceAssetPolicySetToWhitelist
- Runtime security - High-risk syscalls
- Runtime Security - Reverse Shell APIs
- Runtime Security - Container Escape APIs
- ModifyEscapeWhiteList
- ModifyEscapeRule
- ModifyEscapeEventStatus
- DescribeEscapeWhiteList
- DescribeEscapeSafeState
- DescribeEscapeRuleInfo
- DescribeEscapeEventsExport
- DescribeEscapeEventTypeSummary
- DescribeEscapeEventTendency
- DescribeEscapeEventInfo
- DescribeEscapeEventDetail
- DeleteEscapeWhiteList
- CreateEscapeWhiteListExportJob
- CreateEscapeEventsExportJob
- AddEscapeWhiteList
- Runtime Security APIs
- StopVulScanTask
- OpenTcssTrial
- ModifyAccessControlStatus
- ModifyAccessControlRuleStatus
- ModifyAbnormalProcessStatus
- ModifyAbnormalProcessRuleStatus
- DescribeWebVulList
- DescribeVulScanLocalImageList
- DescribeVulScanInfo
- DescribeVulImageList
- DescribeVulDetail
- DescribeVulContainerList
- DescribeSupportDefenceVul
- DescribeRiskSyscallDetail
- DescribeEmergencyVulList
- DescribeAssetImageBindRuleInfo
- DescribeAccessControlRulesExport
- DescribeAccessControlRules
- DescribeAccessControlRuleDetail
- DescribeAccessControlEventsExport
- DescribeAccessControlEvents
- DescribeAccessControlDetail
- DescribeAbnormalProcessRulesExport
- DescribeAbnormalProcessRules
- DescribeAbnormalProcessRuleDetail
- DescribeAbnormalProcessLevelSummary
- DescribeAbnormalProcessEventsExport
- DescribeAbnormalProcessEvents
- DescribeAbnormalProcessEventTendency
- DescribeAbnormalProcessDetail
- DeleteAccessControlRules
- DeleteAbnormalProcessRules
- CreateWebVulExportJob
- CreateVulScanTask
- CreateVulImageExportJob
- CreateVulContainerExportJob
- CreateSystemVulExportJob
- CreateRiskDnsEventExportJob
- CreateProcessEventsExportJob
- CreateEmergencyVulExportJob
- CreateDefenceVulExportJob
- AddEditRiskSyscallWhiteList
- AddEditAccessControlRule
- AddEditAbnormalProcessRule
- Image Security APIs
- DescribeVulRegistryImageList
- UpdateImageRegistryTimingScanTask
- UpdateAssetImageRegistryRegistryDetail
- SyncAssetImageRegistryAsset
- SwitchImageAutoAuthorizedRule
- RenewImageAuthorizeState
- RemoveAssetImageRegistryRegistryDetail
- ModifyVulDefenceSetting
- ModifyVulDefenceEventStatus
- ModifyImageAuthorized
- ModifyAssetImageScanStop
- ModifyAssetImageRegistryScanStopOneKey
- ModifyAssetImageRegistryScanStop
- ModifyAsset
- DescribeVulTopRanking
- DescribeVulTendency
- DescribeVulSummary
- DescribeVulScanAuthorizedImageSummary
- DescribeVulLevelSummary
- DescribeVulLevelImageSummary
- DescribeVulImageSummary
- DescribeVulIgnoreRegistryImageList
- DescribeVulIgnoreLocalImageList
- DescribeVulDefenceSetting
- DescribeVulDefencePlugin
- DescribeVulDefenceHost
- DescribeVulDefenceEventTendency
- DescribeVulDefenceEventDetail
- DescribeVulDefenceEvent
- DescribeValueAddedSrvInfo
- DescribeSystemVulList
- DescribeSecEventsTendency
- DescribeScanIgnoreVulList
- DescribePostPayDetail
- DescribeNewestVul
- DescribeImageSimpleList
- DescribeImageRiskTendency
- DescribeImageRiskSummary
- DescribeImageRegistryTimingScanTask
- DescribeImageRegistryNamespaceList
- DescribeImageComponentList
- DescribeImageAutoAuthorizedTaskList
- DescribeImageAutoAuthorizedRule
- DescribeImageAutoAuthorizedLogList
- DescribeContainerSecEventSummary
- DescribeContainerAssetSummary
- DescribeAutoAuthorizedRuleHost
- DescribeAssetWebServiceList
- DescribeAssetSummary
- DescribeAssetProcessList
- DescribeAssetPortList
- DescribeAssetImageVulListExport
- DescribeAssetImageVulList
- DescribeAssetImageVirusListExport
- DescribeAssetImageVirusList
- DescribeAssetImageSimpleList
- DescribeAssetImageScanTask
- DescribeAssetImageScanStatus
- DescribeAssetImageScanSetting
- DescribeAssetImageRiskListExport
- DescribeAssetImageRiskList
- DescribeAssetImageRegistryVulListExport
- DescribeAssetImageRegistryVulList
- DescribeAssetImageRegistryVirusListExport
- DescribeAssetImageRegistryVirusList
- DescribeAssetImageRegistrySummary
- DescribeAssetImageRegistryScanStatusOneKey
- DescribeAssetImageRegistryRiskListExport
- DescribeAssetImageRegistryRiskInfoList
- DescribeAssetImageRegistryRegistryList
- DescribeAssetImageRegistryRegistryDetail
- DescribeAssetImageRegistryListExport
- DescribeAssetImageRegistryList
- DescribeAssetImageRegistryDetail
- DescribeAssetImageRegistryAssetStatus
- DescribeAssetImageListExport
- DescribeAssetImageList
- DescribeAssetImageHostList
- DescribeAssetImageDetail
- DescribeAssetHostList
- DescribeAssetHostDetail
- DescribeAssetDBServiceList
- DescribeAssetContainerList
- DescribeAssetContainerDetail
- DescribeAssetComponentList
- DescribeAssetAppServiceList
- DeleteIgnoreVul
- CreateVulExportJob
- CreateVulDefenceHostExportJob
- CreateVulDefenceEventExportJob
- CreateOrModifyPostPayCores
- CreateImageExportJob
- CreateComponentExportJob
- CreateAssetImageScanTask
- CreateAssetImageRegistryScanTaskOneKey
- CreateAssetImageRegistryScanTask
- CheckRepeatAssetImageRegistry
- AddIgnoreVul
- AddEditImageAutoAuthorizedRule
- AddAssetImageRegistryRegistryDetail
- Runtime Security - Trojan Call APIs
- DescribeExportJobResult
- StopVirusScanTask
- ModifyVirusScanTimeoutSetting
- ModifyVirusScanSetting
- ModifyVirusMonitorSetting
- ModifyVirusFileStatus
- ModifyVirusAutoIsolateSetting
- ModifyVirusAutoIsolateExampleSwitch
- ExportVirusList
- DescribeVirusTaskList
- DescribeVirusSummary
- DescribeVirusScanTimeoutSetting
- DescribeVirusScanTaskStatus
- DescribeVirusScanSetting
- DescribeVirusSampleDownloadUrl
- DescribeVirusMonitorSetting
- DescribeVirusManualScanEstimateTimeout
- DescribeVirusList
- DescribeVirusEventTendency
- DescribeVirusDetail
- DescribeVirusAutoIsolateSetting
- DescribeVirusAutoIsolateSampleList
- DescribeVirusAutoIsolateSampleDownloadURL
- DescribeVirusAutoIsolateSampleDetail
- CreateVirusScanTask
- CreateVirusScanAgain
- Asset Management APIs
- ModifyContainerNetStatus
- DescribeUnauthorizedCoresTendency
- DescribeTcssSummary
- DescribePromotionActivity
- DescribeInspectionReport
- DescribeExportJobManageList
- DescribeExportJobDownloadURL
- DescribeAssetSyncLastTime
- DescribeAgentInstallCommand
- DescribeAgentDaemonSetCmd
- DescribeABTestConfig
- DeleteMachine
- CreateHostExportJob
- CreateAssetImageVirusExportJob
- CreateAssetImageScanSetting
- Security Operations - Log Analysis APIs
- ResetSecLogTopicConfig
- ModifySecLogKafkaUIN
- ModifySecLogJoinState
- ModifySecLogJoinObjects
- ModifySecLogDeliveryKafkaSetting
- ModifySecLogDeliveryClsSetting
- ModifySecLogCleanSettingInfo
- DescribeSecLogKafkaUIN
- DescribeSecLogJoinTypeList
- DescribeSecLogJoinObjectList
- DescribeSecLogDeliveryKafkaSetting
- DescribeSecLogDeliveryKafkaOptions
- DescribeSecLogDeliveryClsSetting
- DescribeSecLogDeliveryClsOptions
- DescribeSecLogCleanSettingInfo
- DescribeSecLogAlertMsg
- DescribeSearchTemplates
- DescribeSearchLogs
- DescribeSearchExportList
- DescribePublicKey
- DescribeLogStorageStatistic
- DescribeIndexList
- DescribeESHits
- DescribeESAggregations
- DeleteSearchTemplate
- CreateSearchTemplate
- Alert Settings APIs
- Advanced prevention - K8s API abnormal requests
- ModifyK8sApiAbnormalRuleStatus
- ModifyK8sApiAbnormalRuleInfo
- ModifyK8sApiAbnormalEventStatus
- DescribeK8sApiAbnormalTendency
- DescribeK8sApiAbnormalSummary
- DescribeK8sApiAbnormalRuleScopeList
- DescribeK8sApiAbnormalRuleList
- DescribeK8sApiAbnormalRuleInfo
- DescribeK8sApiAbnormalEventList
- DescribeK8sApiAbnormalEventInfo
- DescribeAssetClusterList
- DeleteK8sApiAbnormalRule
- CreateK8sApiAbnormalRuleInfo
- CreateK8sApiAbnormalRuleExportJob
- CreateK8sApiAbnormalEventExportJob
- CreateAccessControlsRuleExportJob
- Billing APIs
- Data Types
- Error Codes
- 常见问题
- TCSS 政策
- 联系我们
- 词汇表
- 产品动态
- 产品简介
- 购买指南
- 快速入门
- 操作指南
- 故障处理
- API 文档
- History
- Introduction
- API Category
- Making API Requests
- Cluster Security APIs
- SetCheckMode
- DescribeUserCluster
- DescribeUnfinishRefreshTask
- DescribeTaskResultSummary
- DescribeRiskList
- DescribeRefreshTask
- DescribeClusterSummary
- DescribeClusterDetail
- DescribeCheckItemList
- DescribeAffectedWorkloadList
- DescribeAffectedNodeList
- DescribeAffectedClusterCount
- CreateRefreshTask
- CreateClusterCheckTask
- CreateCheckComponent
- Network Security APIs
- UpdateNetworkFirewallPolicyYamlDetail
- UpdateNetworkFirewallPolicyDetail
- UpdateAndPublishNetworkFirewallPolicyYamlDetail
- UpdateAndPublishNetworkFirewallPolicyDetail
- DescribeNetworkFirewallPolicyYamlDetail
- DescribeNetworkFirewallPolicyStatus
- DescribeNetworkFirewallPolicyList
- DescribeNetworkFirewallPolicyDiscover
- DescribeNetworkFirewallPolicyDetail
- DescribeNetworkFirewallPodLabelsList
- DescribeNetworkFirewallNamespaceLabelList
- DescribeNetworkFirewallClusterRefreshStatus
- DescribeNetworkFirewallClusterList
- DescribeNetworkFirewallAuditRecord
- DeleteNetworkFirewallPolicyDetail
- CreateNetworkFirewallUndoPublish
- CreateNetworkFirewallPublish
- CreateNetworkFirewallPolicyDiscover
- CreateNetworkFirewallClusterRefresh
- ConfirmNetworkFirewallPolicy
- CheckNetworkFirewallPolicyYaml
- AddNetworkFirewallPolicyYamlDetail
- AddNetworkFirewallPolicyDetail
- AddAndPublishNetworkFirewallPolicyYamlDetail
- AddAndPublishNetworkFirewallPolicyDetail
- Security Compliance APIs
- ScanComplianceScanFailedAssets
- ScanCompliancePolicyItems
- ScanComplianceAssetsByPolicyItem
- ScanComplianceAssets
- ModifyCompliancePeriodTask
- InitializeUserComplianceEnvironment
- DescribeComplianceWhitelistItemList
- DescribeComplianceTaskPolicyItemSummaryList
- DescribeComplianceTaskAssetSummary
- DescribeComplianceScanFailedAssetList
- DescribeCompliancePolicyItemAffectedSummary
- DescribeCompliancePolicyItemAffectedAssetList
- DescribeCompliancePeriodTaskList
- DescribeComplianceAssetPolicyItemList
- DescribeComplianceAssetList
- DescribeComplianceAssetDetailInfo
- DeleteCompliancePolicyItemFromWhitelist
- DeleteCompliancePolicyAssetSetFromWhitelist
- DeleteComplianceAssetPolicySetFromWhitelist
- CreateExportComplianceStatusListJob
- CreateComplianceTask
- AddCompliancePolicyItemToWhitelist
- AddCompliancePolicyAssetSetToWhitelist
- AddComplianceAssetPolicySetToWhitelist
- Runtime security - High-risk syscalls
- Runtime Security - Reverse Shell APIs
- Runtime Security - Container Escape APIs
- ModifyEscapeWhiteList
- ModifyEscapeRule
- ModifyEscapeEventStatus
- DescribeEscapeWhiteList
- DescribeEscapeSafeState
- DescribeEscapeRuleInfo
- DescribeEscapeEventsExport
- DescribeEscapeEventTypeSummary
- DescribeEscapeEventTendency
- DescribeEscapeEventInfo
- DescribeEscapeEventDetail
- DeleteEscapeWhiteList
- CreateEscapeWhiteListExportJob
- CreateEscapeEventsExportJob
- AddEscapeWhiteList
- Runtime Security APIs
- StopVulScanTask
- OpenTcssTrial
- ModifyAccessControlStatus
- ModifyAccessControlRuleStatus
- ModifyAbnormalProcessStatus
- ModifyAbnormalProcessRuleStatus
- DescribeWebVulList
- DescribeVulScanLocalImageList
- DescribeVulScanInfo
- DescribeVulImageList
- DescribeVulDetail
- DescribeVulContainerList
- DescribeSupportDefenceVul
- DescribeRiskSyscallDetail
- DescribeEmergencyVulList
- DescribeAssetImageBindRuleInfo
- DescribeAccessControlRulesExport
- DescribeAccessControlRules
- DescribeAccessControlRuleDetail
- DescribeAccessControlEventsExport
- DescribeAccessControlEvents
- DescribeAccessControlDetail
- DescribeAbnormalProcessRulesExport
- DescribeAbnormalProcessRules
- DescribeAbnormalProcessRuleDetail
- DescribeAbnormalProcessLevelSummary
- DescribeAbnormalProcessEventsExport
- DescribeAbnormalProcessEvents
- DescribeAbnormalProcessEventTendency
- DescribeAbnormalProcessDetail
- DeleteAccessControlRules
- DeleteAbnormalProcessRules
- CreateWebVulExportJob
- CreateVulScanTask
- CreateVulImageExportJob
- CreateVulContainerExportJob
- CreateSystemVulExportJob
- CreateRiskDnsEventExportJob
- CreateProcessEventsExportJob
- CreateEmergencyVulExportJob
- CreateDefenceVulExportJob
- AddEditRiskSyscallWhiteList
- AddEditAccessControlRule
- AddEditAbnormalProcessRule
- Image Security APIs
- DescribeVulRegistryImageList
- UpdateImageRegistryTimingScanTask
- UpdateAssetImageRegistryRegistryDetail
- SyncAssetImageRegistryAsset
- SwitchImageAutoAuthorizedRule
- RenewImageAuthorizeState
- RemoveAssetImageRegistryRegistryDetail
- ModifyVulDefenceSetting
- ModifyVulDefenceEventStatus
- ModifyImageAuthorized
- ModifyAssetImageScanStop
- ModifyAssetImageRegistryScanStopOneKey
- ModifyAssetImageRegistryScanStop
- ModifyAsset
- DescribeVulTopRanking
- DescribeVulTendency
- DescribeVulSummary
- DescribeVulScanAuthorizedImageSummary
- DescribeVulLevelSummary
- DescribeVulLevelImageSummary
- DescribeVulImageSummary
- DescribeVulIgnoreRegistryImageList
- DescribeVulIgnoreLocalImageList
- DescribeVulDefenceSetting
- DescribeVulDefencePlugin
- DescribeVulDefenceHost
- DescribeVulDefenceEventTendency
- DescribeVulDefenceEventDetail
- DescribeVulDefenceEvent
- DescribeValueAddedSrvInfo
- DescribeSystemVulList
- DescribeSecEventsTendency
- DescribeScanIgnoreVulList
- DescribePostPayDetail
- DescribeNewestVul
- DescribeImageSimpleList
- DescribeImageRiskTendency
- DescribeImageRiskSummary
- DescribeImageRegistryTimingScanTask
- DescribeImageRegistryNamespaceList
- DescribeImageComponentList
- DescribeImageAutoAuthorizedTaskList
- DescribeImageAutoAuthorizedRule
- DescribeImageAutoAuthorizedLogList
- DescribeContainerSecEventSummary
- DescribeContainerAssetSummary
- DescribeAutoAuthorizedRuleHost
- DescribeAssetWebServiceList
- DescribeAssetSummary
- DescribeAssetProcessList
- DescribeAssetPortList
- DescribeAssetImageVulListExport
- DescribeAssetImageVulList
- DescribeAssetImageVirusListExport
- DescribeAssetImageVirusList
- DescribeAssetImageSimpleList
- DescribeAssetImageScanTask
- DescribeAssetImageScanStatus
- DescribeAssetImageScanSetting
- DescribeAssetImageRiskListExport
- DescribeAssetImageRiskList
- DescribeAssetImageRegistryVulListExport
- DescribeAssetImageRegistryVulList
- DescribeAssetImageRegistryVirusListExport
- DescribeAssetImageRegistryVirusList
- DescribeAssetImageRegistrySummary
- DescribeAssetImageRegistryScanStatusOneKey
- DescribeAssetImageRegistryRiskListExport
- DescribeAssetImageRegistryRiskInfoList
- DescribeAssetImageRegistryRegistryList
- DescribeAssetImageRegistryRegistryDetail
- DescribeAssetImageRegistryListExport
- DescribeAssetImageRegistryList
- DescribeAssetImageRegistryDetail
- DescribeAssetImageRegistryAssetStatus
- DescribeAssetImageListExport
- DescribeAssetImageList
- DescribeAssetImageHostList
- DescribeAssetImageDetail
- DescribeAssetHostList
- DescribeAssetHostDetail
- DescribeAssetDBServiceList
- DescribeAssetContainerList
- DescribeAssetContainerDetail
- DescribeAssetComponentList
- DescribeAssetAppServiceList
- DeleteIgnoreVul
- CreateVulExportJob
- CreateVulDefenceHostExportJob
- CreateVulDefenceEventExportJob
- CreateOrModifyPostPayCores
- CreateImageExportJob
- CreateComponentExportJob
- CreateAssetImageScanTask
- CreateAssetImageRegistryScanTaskOneKey
- CreateAssetImageRegistryScanTask
- CheckRepeatAssetImageRegistry
- AddIgnoreVul
- AddEditImageAutoAuthorizedRule
- AddAssetImageRegistryRegistryDetail
- Runtime Security - Trojan Call APIs
- DescribeExportJobResult
- StopVirusScanTask
- ModifyVirusScanTimeoutSetting
- ModifyVirusScanSetting
- ModifyVirusMonitorSetting
- ModifyVirusFileStatus
- ModifyVirusAutoIsolateSetting
- ModifyVirusAutoIsolateExampleSwitch
- ExportVirusList
- DescribeVirusTaskList
- DescribeVirusSummary
- DescribeVirusScanTimeoutSetting
- DescribeVirusScanTaskStatus
- DescribeVirusScanSetting
- DescribeVirusSampleDownloadUrl
- DescribeVirusMonitorSetting
- DescribeVirusManualScanEstimateTimeout
- DescribeVirusList
- DescribeVirusEventTendency
- DescribeVirusDetail
- DescribeVirusAutoIsolateSetting
- DescribeVirusAutoIsolateSampleList
- DescribeVirusAutoIsolateSampleDownloadURL
- DescribeVirusAutoIsolateSampleDetail
- CreateVirusScanTask
- CreateVirusScanAgain
- Asset Management APIs
- ModifyContainerNetStatus
- DescribeUnauthorizedCoresTendency
- DescribeTcssSummary
- DescribePromotionActivity
- DescribeInspectionReport
- DescribeExportJobManageList
- DescribeExportJobDownloadURL
- DescribeAssetSyncLastTime
- DescribeAgentInstallCommand
- DescribeAgentDaemonSetCmd
- DescribeABTestConfig
- DeleteMachine
- CreateHostExportJob
- CreateAssetImageVirusExportJob
- CreateAssetImageScanSetting
- Security Operations - Log Analysis APIs
- ResetSecLogTopicConfig
- ModifySecLogKafkaUIN
- ModifySecLogJoinState
- ModifySecLogJoinObjects
- ModifySecLogDeliveryKafkaSetting
- ModifySecLogDeliveryClsSetting
- ModifySecLogCleanSettingInfo
- DescribeSecLogKafkaUIN
- DescribeSecLogJoinTypeList
- DescribeSecLogJoinObjectList
- DescribeSecLogDeliveryKafkaSetting
- DescribeSecLogDeliveryKafkaOptions
- DescribeSecLogDeliveryClsSetting
- DescribeSecLogDeliveryClsOptions
- DescribeSecLogCleanSettingInfo
- DescribeSecLogAlertMsg
- DescribeSearchTemplates
- DescribeSearchLogs
- DescribeSearchExportList
- DescribePublicKey
- DescribeLogStorageStatistic
- DescribeIndexList
- DescribeESHits
- DescribeESAggregations
- DeleteSearchTemplate
- CreateSearchTemplate
- Alert Settings APIs
- Advanced prevention - K8s API abnormal requests
- ModifyK8sApiAbnormalRuleStatus
- ModifyK8sApiAbnormalRuleInfo
- ModifyK8sApiAbnormalEventStatus
- DescribeK8sApiAbnormalTendency
- DescribeK8sApiAbnormalSummary
- DescribeK8sApiAbnormalRuleScopeList
- DescribeK8sApiAbnormalRuleList
- DescribeK8sApiAbnormalRuleInfo
- DescribeK8sApiAbnormalEventList
- DescribeK8sApiAbnormalEventInfo
- DescribeAssetClusterList
- DeleteK8sApiAbnormalRule
- CreateK8sApiAbnormalRuleInfo
- CreateK8sApiAbnormalRuleExportJob
- CreateK8sApiAbnormalEventExportJob
- CreateAccessControlsRuleExportJob
- Billing APIs
- Data Types
- Error Codes
- 常见问题
- TCSS 政策
- 联系我们
- 词汇表
接入自建集群
本文介绍接入自建集群的步骤,您可以将自建集群接入容器安全服务进行统一管理,对自建集群开展集群风险检查和管理。
限制条件
接入自建集群节点规模小于500节点。
操作步骤
1. 登录 容器安全服务控制台,在左侧导航中,单击集群风险管理 > 集群检查。
2. 在集群检查页面,单击接入自建集群。
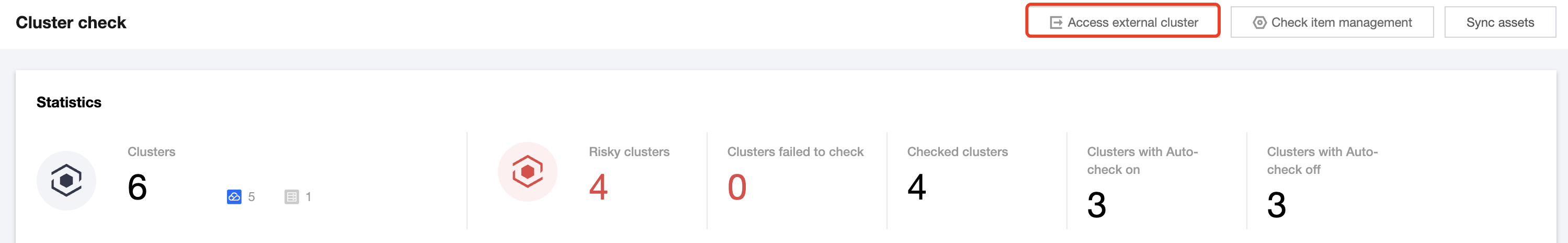

3. 在集群信息设置页面,配置相关参数,单击下一步。
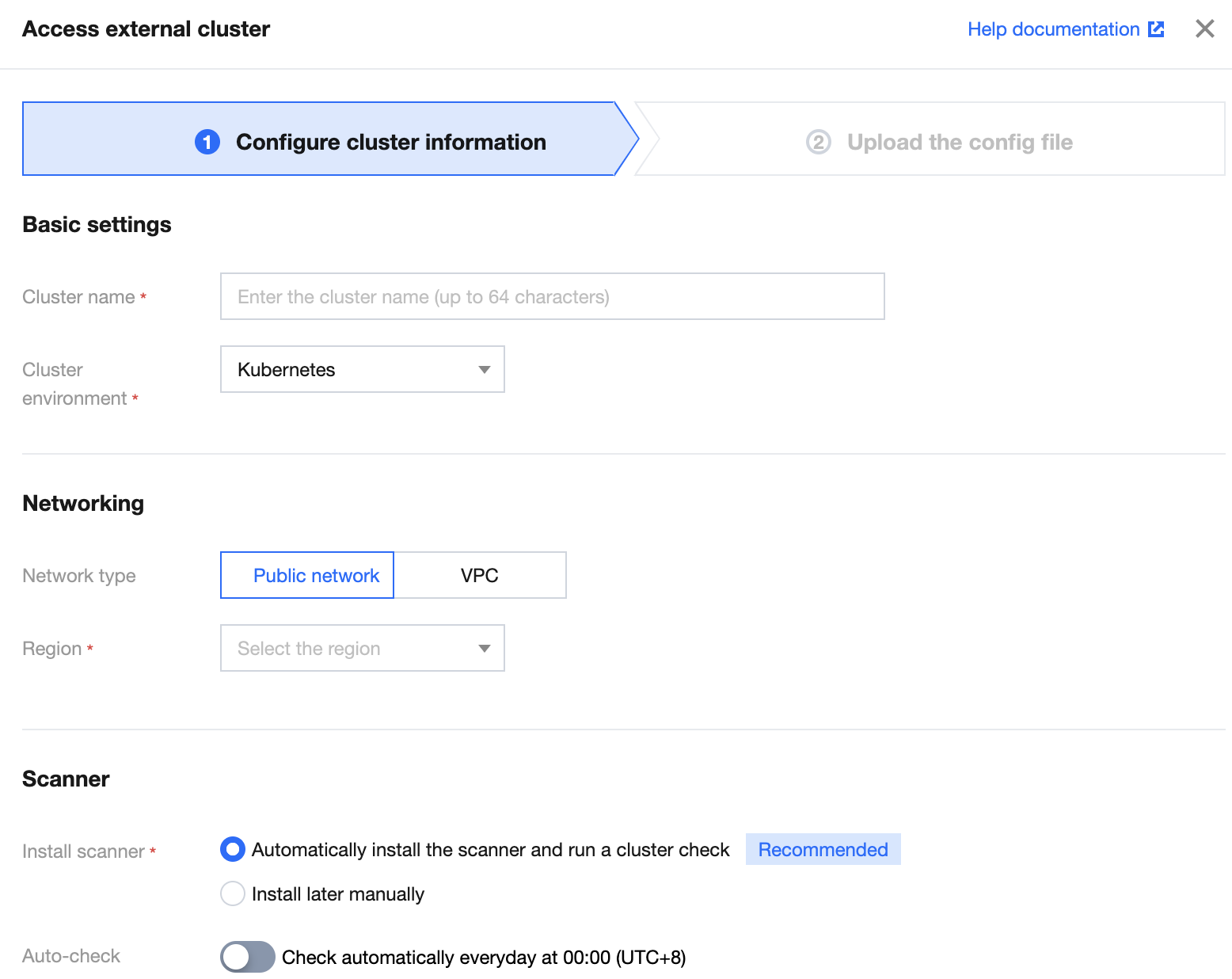

参数说明:
参数组 | 参数 | 说明 | 可选项 |
基础信息设置 | 集群名称 | 输入自建集群的名称,64字符以内 | - |
| 集群环境 | 选择自建集群的类型 | Kubernetes、Openshift |
| 集群版本 | 选择集群环境的集群版本 | K8s 集群支持1.13以上版本 |
网络信息设置 | 网络类型 | 选择通过公网或通过 VPC 网络接入自建集群 | 公网、VPC |
| 所在地域 | 选择自建集群所在的地域,公网类型无地域限制 | - |
| VPC ID | 当网络类型使用 VPC 时,选择集群所在网络的 VPC 信息 | - |
| API Server地址 | 当网络类型使用 VPC 时,选择集群 API Server 后端服务类型 | 服务器、负载均衡 |
集群检查组件 | 安装检查组件 | 选择自动或者自行手动安装集群检查的组件 | 自动安装检查组件并进行一次集群检查 不安装检查组件,接入后自行安装组件并下发集群安装 |
| 自动检查 | 是否开启集群的自动检查功能 | 开启 关闭 |
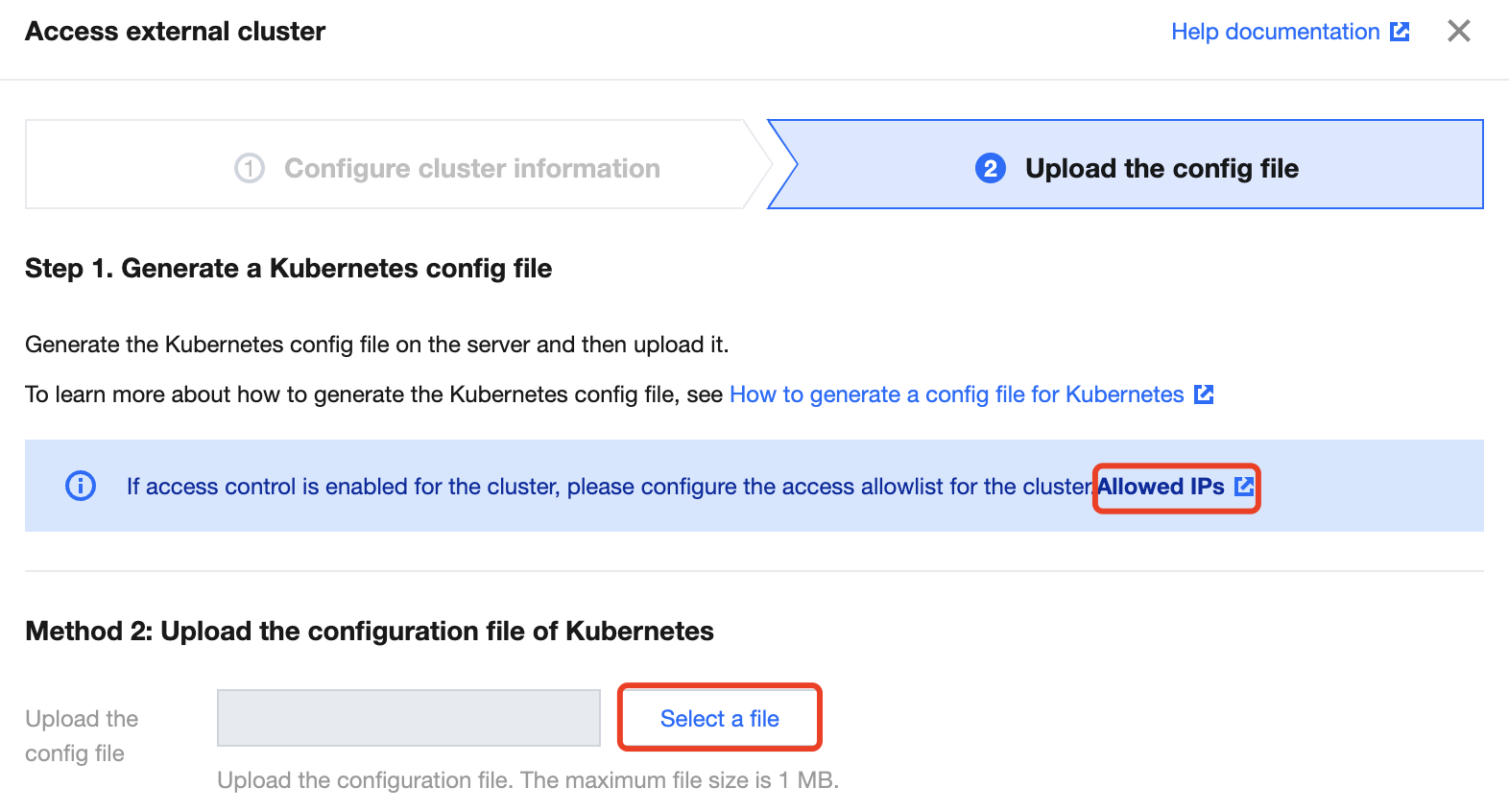
4. 在上传配置文件,单击选择文件,上传本地文件后,单击完成接入即可接入自建集群。
注意:
公网方式接入自建集群,如果您的集群有设置访问控制策略,需单击 IP 白名单地址添加页面中的 IP 地址。
您需要在服务器上生成 K8s 配置文件后,才能上传该配置文件。生成 K8s 配置文件的具体操作,请参见 生成 K8S 配置文件。
上传配置文件,大小需要在1M 以内。
生成 K8s 配置文件
前提条件
已在服务器上搭建 K8s 集群。具体操作,请参见 K8s 官方文档。
已安装 Docker 服务。
操作步骤
1. 以 root 身份登录 k8s 集群 master 所在服务器。
2. 输入如下命令,创建命名空间和权限绑定。
# 1. 创建命名空间: tcss# 2. 创建命名空间tcss下的管理角色: tcss-admin# 3. 绑定角色tcss-admin和用户tcss# 4. 创建秘钥并绑定服务账号: tcss-agent-secret,tcss-agent# 5. 创建只读的集群角色: security-clusterrole# 6. 绑定集群角色security-clusterrole到服务账号tcss-agent---apiVersion: v1kind: Namespacemetadata:name: tcss---apiVersion: rbac.authorization.k8s.io/v1kind: Rolemetadata:namespace: tcssname: tcss-adminrules:- apiGroups: ["extensions", "apps", ""]resources: ["*"]verbs: ["get", "list", "watch", "create", "update", "patch", "delete"]---apiVersion: rbac.authorization.k8s.io/v1kind: RoleBindingmetadata:name: tcss-admin-rbnamespace: tcsssubjects:- kind: Username: tcssapiGroup: rbac.authorization.k8s.ioroleRef:kind: Rolename: tcss-adminapiGroup: rbac.authorization.k8s.io---apiVersion: v1kind: Secretmetadata:name: tcss-agent-secretnamespace: tcssannotations:kubernetes.io/service-account.name: tcss-agenttype: kubernetes.io/service-account-token---apiVersion: v1kind: ServiceAccountmetadata:name: tcss-agentnamespace: tcsssecrets:- name: tcss-agent-secretnamespace: tcss---apiVersion: rbac.authorization.k8s.io/v1kind: ClusterRolemetadata:name: security-clusterrolerules:- apiGroups: ["", "v1"]resources: ["namespaces", "pods", "nodes"]verbs: ["get", "list"]- apiGroups: ["apps"]resources: ["replicasets", "daemonsets", "deployments", "statefulsets"]verbs: ["get", "list"]- apiGroups: ["batch"]resources: ["jobs", "cronjobs"]verbs: ["get", "list"]- apiGroups: ["rbac.authorization.k8s.io"]resources: ["clusterroles", "clusterrolebindings"]verbs: ["get"]---apiVersion: rbac.authorization.k8s.io/v1kind: ClusterRoleBindingmetadata:name: security-clusterrolebindingroleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: security-clusterrolesubjects:- kind: ServiceAccountname: tcss-agentnamespace: tcss- kind: Username: tcssapiGroup: rbac.authorization.k8s.io
3. 进入 k8s 配置目录(/etc/kubernetes/),输入如下命令,创建证书。
# 创建User私钥 tcss.key。openssl genrsa -out tcss.key 2048# 创建证书签署请求 tcss.csropenssl req -new -key tcss.key -out tcss.csr -subj "/O=K8s/CN=tcss"# 签署证书 生成 tcss.crtopenssl x509 -req -in tcss.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out tcss.crt -days 365
4. 输入如下命令,创建集群配置文件。
# 创建并设置集群配置, 其中需要 API Server 地址必须为公网可访问地址kubectl config set-cluster tcss --server=https://xx.xx.xx.xx:60002 --certificate-authority=/etc/kubernetes/ca.crt --embed-certs=true --kubeconfig=/root/tcss.conf# 创建并设置用户配置kubectl config set-credentials tcss --client-certificate=tcss.crt --client-key=tcss.key --embed-certs=true --kubeconfig=/root/tcss.conf# 设置context配置kubectl config set-context tcss@tcss --cluster=tcss --user=tcss --kubeconfig=/root/tcss.conf# 切换context配置kubectl config use-context tcss@tcss --kubeconfig=/root/tcss.conf
5. 验证集群配置文件并上传配置。
KUBECONFIG=/root/tcss.conf kubectl -n tcss get pod
说明:
执行上述命令,如果能显示 pod 或者显示当前命名空间下没有相关资源,则表示该集群配置是可用的,上传该文件 /root/tcss.conf 即可。
一键脚本
在 master 节点中,您可基于以下一键脚本代码一键快速生成集群配置文件:
说明:
环境需要提前安装 openssl。
#!/bin/bashset -e;# API_SERVER 需要设置为公网可访问的地址和端口# API_SERVER=https://xx.xx.xx.xx:xxxx# 以下路径,用户根据集群实际情况设定KUBECONFIG_TARGET=/root/tcss.confCA_FILE=/etc/kubernetes/ca.crtCAKEY_FILE=/etc/kubernetes/ca.keyTCSS_TMPDIR=/tmp/tcss# 如果是OpenShift环境,可以更换为 ocKUBECTL_CMD=kubectlif [ ! $API_SERVER ]; thenecho "API_SERVER does not set.";exit 1;fiif ! which kubectl ; thenecho "kubectl does not exist.";exit 1;fiif [ ! -f "$CA_FILE" ]; thenecho "$CA_FILE does not exist.";exit 1;fiif [ ! -f "$CAKEY_FILE" ]; thenecho "$CAKEY_FILE does not exist.";exit 1;fiif [ ! -d $TCSS_TMPDIR ]; thenmkdir -p $TCSS_TMPDIR;ficat <<EOF > $TCSS_TMPDIR/tcss_res.yaml---apiVersion: v1kind: Namespacemetadata:name: tcss---apiVersion: rbac.authorization.k8s.io/v1kind: Rolemetadata:namespace: tcssname: tcss-adminrules:- apiGroups: ["extensions", "apps", ""]resources: ["*"]verbs: ["get", "list", "watch", "create", "update", "patch", "delete"]---apiVersion: rbac.authorization.k8s.io/v1kind: RoleBindingmetadata:name: tcss-admin-rbnamespace: tcsssubjects:- kind: Username: tcssapiGroup: rbac.authorization.k8s.ioroleRef:kind: Rolename: tcss-adminapiGroup: rbac.authorization.k8s.io---apiVersion: v1kind: Secretmetadata:name: tcss-agent-secretnamespace: tcssannotations:kubernetes.io/service-account.name: tcss-agenttype: kubernetes.io/service-account-token---apiVersion: v1kind: ServiceAccountmetadata:name: tcss-agentnamespace: tcsssecrets:- name: tcss-agent-secretnamespace: tcss---apiVersion: rbac.authorization.k8s.io/v1kind: ClusterRolemetadata:name: security-clusterrolerules:- apiGroups: ["", "v1"]resources: ["namespaces", "pods", "nodes"]verbs: ["get", "list"]- apiGroups: ["apps"]resources: ["replicasets", "daemonsets", "deployments", "statefulsets"]verbs: ["get", "list"]- apiGroups: ["batch"]resources: ["jobs", "cronjobs"]verbs: ["get", "list"]- apiGroups: ["rbac.authorization.k8s.io"]resources: ["clusterroles", "clusterrolebindings"]verbs: ["get"]---apiVersion: rbac.authorization.k8s.io/v1kind: ClusterRoleBindingmetadata:name: security-clusterrolebindingroleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: security-clusterrolesubjects:- kind: ServiceAccountname: tcss-agentnamespace: tcss- kind: Username: tcssapiGroup: rbac.authorization.k8s.ioEOF# echo "generate tcss resource file ($TCSS_TMPDIR/tcss_res.yaml) success."$KUBECTL_CMD apply -f $TCSS_TMPDIR/tcss_res.yaml;# 创建User私钥 tcss.key。openssl genrsa -out $TCSS_TMPDIR/tcss.key 2048# 创建证书签署请求 tcss.csropenssl req -new -key $TCSS_TMPDIR/tcss.key -out $TCSS_TMPDIR/tcss.csr -subj "/O=K8s/CN=tcss"# 签署证书 生成 tcss.crtopenssl x509 -req -in $TCSS_TMPDIR/tcss.csr -CA $CA_FILE -CAkey $CAKEY_FILE -CAcreateserial -out $TCSS_TMPDIR/tcss.crt -days 365# 创建并设置集群配置$KUBECTL_CMD config set-cluster tcss --server=$API_SERVER --certificate-authority=$CA_FILE --embed-certs=true --kubeconfig=$KUBECONFIG_TARGET# 创建并设置用户配置$KUBECTL_CMD config set-credentials tcss --client-certificate=$TCSS_TMPDIR/tcss.crt --client-key=$TCSS_TMPDIR/tcss.key --embed-certs=true --kubeconfig=$KUBECONFIG_TARGET# 设置context配置$KUBECTL_CMD config set-context tcss@tcss --cluster=tcss --user=tcss --kubeconfig=$KUBECONFIG_TARGET# 切换context配置$KUBECTL_CMD config use-context tcss@tcss --kubeconfig=$KUBECONFIG_TARGETecho "generate KUBECONFIG file success. $KUBECONFIG_TARGET"
生成 Openshift 配置文件
前提条件
1. 已在服务器上搭建 K8s 集群。具体操作,请参见 K8s 官方文档。
2. 已安装 Docker 服务。
3. 暂仅支持 OpenShift3.0及以上版本接入,低于该版本可能存在不确定性问题。
操作步骤
说明:
整体接入思路和 Kubernetes 类似,只涉及相关路径和命令行工具区别,如果集群 master 节点上已经安装的 kubectl 工具,则可以完全同 Kubernetes 集群接入方式进行接入。
1. 以 root 身份登录 OpenShift 集群 master 所在服务器。
2. 输入如下命令,创建命名空间和权限绑定。
# 1. 创建命名空间: tcss# 2. 创建命名空间tcss下的管理角色: tcss-admin# 3. 绑定角色tcss-admin和用户tcss# 4. 创建秘钥并绑定服务账号: tcss-agent-secret,tcss-agent# 5. 创建只读的集群角色: security-clusterrole# 6. 绑定集群角色security-clusterrole到服务账号tcss-agent---apiVersion: v1kind: Namespacemetadata:name: tcss---apiVersion: rbac.authorization.k8s.io/v1kind: Rolemetadata:namespace: tcssname: tcss-adminrules:- apiGroups: ["extensions", "apps", ""]resources: ["*"]verbs: ["get", "list", "watch", "create", "update", "patch", "delete"]---apiVersion: rbac.authorization.k8s.io/v1kind: RoleBindingmetadata:name: tcss-admin-rbnamespace: tcsssubjects:- kind: Username: tcssapiGroup: rbac.authorization.k8s.ioroleRef:kind: Rolename: tcss-adminapiGroup: rbac.authorization.k8s.io---apiVersion: v1kind: Secretmetadata:name: tcss-agent-secretnamespace: tcssannotations:kubernetes.io/service-account.name: tcss-agenttype: kubernetes.io/service-account-token---apiVersion: v1kind: ServiceAccountmetadata:name: tcss-agentnamespace: tcsssecrets:- name: tcss-agent-secretnamespace: tcss---apiVersion: rbac.authorization.k8s.io/v1kind: ClusterRolemetadata:name: security-clusterrolerules:- apiGroups: ["", "v1"]resources: ["namespaces", "pods", "nodes"]verbs: ["get", "list"]- apiGroups: ["apps"]resources: ["replicasets", "daemonsets", "deployments", "statefulsets"]verbs: ["get", "list"]- apiGroups: ["batch"]resources: ["jobs", "cronjobs"]verbs: ["get", "list"]- apiGroups: ["rbac.authorization.k8s.io"]resources: ["clusterroles", "clusterrolebindings"]verbs: ["get"]---apiVersion: rbac.authorization.k8s.io/v1kind: ClusterRoleBindingmetadata:name: security-clusterrolebindingroleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: security-clusterrolesubjects:- kind: ServiceAccountname: tcss-agentnamespace: tcss- kind: Username: tcssapiGroup: rbac.authorization.k8s.io
3. 进入配置目录(/etc/origin/master/),输入如下命令,创建证书。
# 创建User私钥 tcss.key。openssl genrsa -out tcss.key 2048# 创建证书签署请求 tcss.csropenssl req -new -key tcss.key -out tcss.csr -subj "/O=K8s/CN=tcss"# 签署证书 生成 tcss.crtopenssl x509 -req -in tcss.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out tcss.crt -days 365
4. 输入如下命令,创建集群配置文件。
# 创建并设置集群配置, 其中需要主要 server 地址必须为公网可访问地址KUBECONFIG=/root/tcss.conf oc config set-cluster tcss --server=https://xx.xx.xx.xx:60002 --certificate-authority=/etc/origin/master/ca.crt --embed-certs=true --kubeconfig=/root/tcss.conf# 创建并设置用户配置KUBECONFIG=/root/tcss.conf oc config set-credentials tcss --client-certificate=tcss.crt --client-key=tcss.key --embed-certs=true --kubeconfig=/root/tcss.conf# 设置context配置KUBECONFIG=/root/tcss.conf oc config set-context tcss@tcss --cluster=tcss --user=tcss --kubeconfig=/root/tcss.conf# 切换context配置KUBECONFIG=/root/tcss.conf oc config use-context tcss@tcss --kubeconfig=/root/tcss.conf
5. 输入如下命令,验证集群配置文件并上传配置。
KUBECONFIG=/root/tcss.conf oc -n tcss get pod
说明:
执行上述命令,如果能显示pod或者显示当前命名空间下没有相关资源则表示该集群配置是可用的,上传该文件 /root/tcss.conf 即可。
一键脚本
在 master 节点中,您可基于以下一键脚本代码一键快速生成集群配置文件:
说明:
环境需要提前安装 openssl。
#!/bin/bashset -e;# API_SERVER 需要设置为公网可访问的地址和端口# API_SERVER=https://xx.xx.xx.xx:xxxx# 以下路径,用户根据集群实际情况设定KUBECONFIG_TARGET=/root/tcss.confCA_FILE=/etc/kubernetes/ca.crtCAKEY_FILE=/etc/kubernetes/ca.keyTCSS_TMPDIR=/tmp/tcssKUBECTL_CMD=ocif [ ! $API_SERVER ]; thenecho "API_SERVER does not set.";exit 1;fiif ! which $KUBECTL_CMD ; thenecho "$KUBECTL_CMD does not exist.";exit 1;fiif [ ! -f "$CA_FILE" ]; thenecho "$CA_FILE does not exist.";exit 1;fiif [ ! -f "$CAKEY_FILE" ]; thenecho "$CAKEY_FILE does not exist.";exit 1;fiif [ ! -d $TCSS_TMPDIR ]; thenmkdir -p $TCSS_TMPDIR;ficat <<EOF > $TCSS_TMPDIR/tcss_res.yaml---apiVersion: v1kind: Namespacemetadata:name: tcss---apiVersion: rbac.authorization.k8s.io/v1kind: Rolemetadata:namespace: tcssname: tcss-adminrules:- apiGroups: ["extensions", "apps", ""]resources: ["*"]verbs: ["get", "list", "watch", "create", "update", "patch", "delete"]---apiVersion: rbac.authorization.k8s.io/v1kind: RoleBindingmetadata:name: tcss-admin-rbnamespace: tcsssubjects:- kind: Username: tcssapiGroup: rbac.authorization.k8s.ioroleRef:kind: Rolename: tcss-adminapiGroup: rbac.authorization.k8s.io---apiVersion: v1kind: Secretmetadata:name: tcss-agent-secretnamespace: tcssannotations:kubernetes.io/service-account.name: tcss-agenttype: kubernetes.io/service-account-token---apiVersion: v1kind: ServiceAccountmetadata:name: tcss-agentnamespace: tcsssecrets:- name: tcss-agent-secretnamespace: tcss---apiVersion: rbac.authorization.k8s.io/v1kind: ClusterRolemetadata:name: security-clusterrolerules:- apiGroups: ["", "v1"]resources: ["namespaces", "pods", "nodes"]verbs: ["get", "list"]- apiGroups: ["apps"]resources: ["replicasets", "daemonsets", "deployments", "statefulsets"]verbs: ["get", "list"]- apiGroups: ["batch"]resources: ["jobs", "cronjobs"]verbs: ["get", "list"]- apiGroups: ["rbac.authorization.k8s.io"]resources: ["clusterroles", "clusterrolebindings"]verbs: ["get"]---apiVersion: rbac.authorization.k8s.io/v1kind: ClusterRoleBindingmetadata:name: security-clusterrolebindingroleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: security-clusterrolesubjects:- kind: ServiceAccountname: tcss-agentnamespace: tcss- kind: Username: tcssapiGroup: rbac.authorization.k8s.ioEOF# echo "generate tcss resource file ($TCSS_TMPDIR/tcss_res.yaml) success."$KUBECTL_CMD apply -f $TCSS_TMPDIR/tcss_res.yaml;$KUBECTL_CMD adm policy add-scc-to-user privileged -n tcss -z tcss-agent;$KUBECTL_CMD adm policy add-scc-to-user hostaccess -n tcss -z tcss-agent;$KUBECTL_CMD adm policy add-scc-to-user privileged tcss;$KUBECTL_CMD adm policy add-scc-to-user hostaccess tcss;oc adm policy add-cluster-role-to-user cluster-reader tcss;# 创建User私钥 tcss.key。openssl genrsa -out $TCSS_TMPDIR/tcss.key 2048# 创建证书签署请求 tcss.csropenssl req -new -key $TCSS_TMPDIR/tcss.key -out $TCSS_TMPDIR/tcss.csr -subj "/O=K8s/CN=tcss"# 签署证书 生成 tcss.crtopenssl x509 -req -in $TCSS_TMPDIR/tcss.csr -CA $CA_FILE -CAkey $CAKEY_FILE -CAcreateserial -out $TCSS_TMPDIR/tcss.crt -days 365# 创建并设置集群配置KUBECONFIG=$KUBECONFIG_TARGET $KUBECTL_CMD config set-cluster tcss --server=$API_SERVER --certificate-authority=$CA_FILE --embed-certs=true --kubeconfig=$KUBECONFIG_TARGET# 创建并设置用户配置KUBECONFIG=$KUBECONFIG_TARGET $KUBECTL_CMD config set-credentials tcss --client-certificate=$TCSS_TMPDIR/tcss.crt --client-key=$TCSS_TMPDIR/tcss.key --embed-certs=true --kubeconfig=$KUBECONFIG_TARGET# 设置context配置KUBECONFIG=$KUBECONFIG_TARGET $KUBECTL_CMD config set-context tcss@tcss --cluster=tcss --user=tcss --kubeconfig=$KUBECONFIG_TARGET# 切换context配置KUBECONFIG=$KUBECONFIG_TARGET $KUBECTL_CMD config use-context tcss@tcss --kubeconfig=$KUBECONFIG_TARGETecho "generate KUBECONFIG file success. $KUBECONFIG_TARGET"

 是
是
 否
否
本页内容是否解决了您的问题?