Viewing monitoring data
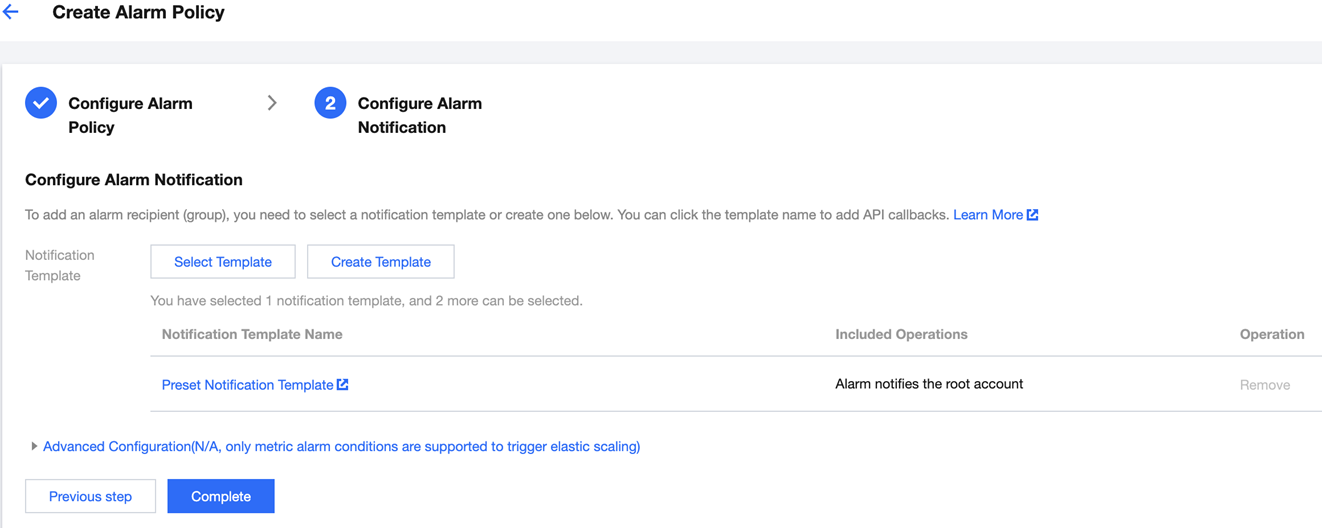
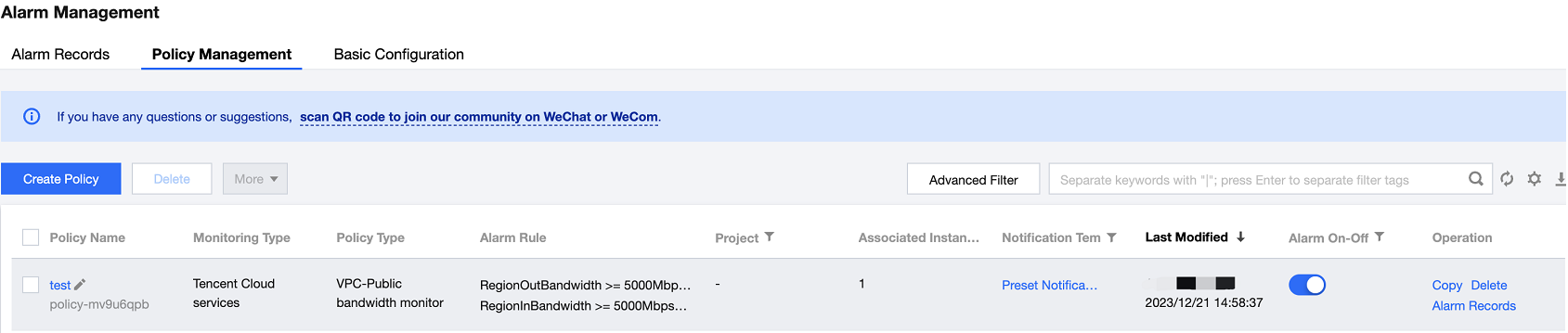
Configure alarms


Copyright Notice
©2013-2025 Tencent Cloud. All rights reserved.
Copyright in this document is exclusively owned by Tencent Cloud. You must not reproduce, modify, copy or distribute in any way, in whole or in part, the contents of this document without Tencent Cloud's the prior written consent.
Trademark Notice

All trademarks associated with Tencent Cloud and its services are owned by the Tencent corporate group, including its parent, subsidiaries and affiliated companies, as the case may be. Trademarks of third parties referred to in this document are owned by their respective proprietors.
Service Statement
This document is intended to provide users with general information about Tencent Cloud's products and services only and does not form part of Tencent Cloud's terms and conditions. Tencent Cloud's products or services are subject to change. Specific products and services and the standards applicable to them are exclusively provided for in Tencent Cloud's applicable terms and conditions.
Last updated:2024-10-22 16:43:07






Last updated:2024-10-22 16:43:29
Last updated:2024-10-22 16:43:46
Instance | Features |
The instance needs to be restarted The classic network IP is immediately changed to the VPC IP, with no retention time If the CVM instance has a public IP, the public IP will stay unchanged after the network switch, which will not affect the access at domain name | |
Dual-IP access is maintained for a certain period of time. The original classic network IP retention time is as follows: MySQL: 24 hours (1 day) by default and up to 168 hours (7 days) MariaDB: 24 hours (1 day) TDSQL: 24 hours (1 day) Redis: you can choose to expire immediately, release after 1 day, release after 2 days, release after 3 days, or release after 7 days MongoDB: the original IP on v4.0 or above will expire immediately. For other versions, you can choose to expire immediately, release after 1 day, release after 2 days, release after 3 days, or release after 7 days | |
| |
| |
| |
| |
You can configure up to two networks for each instance, both of which can be used for business access. The IPs of different networks can be the same. | |
Last updated:2024-10-22 16:44:01
Last updated:2024-10-22 16:44:16
Last updated:2024-10-22 16:44:38
172.21.10.13 and 172.21.10.17, keep scan the non-open ports of VPC A. 172.21.10.13 and 172.21.10.17.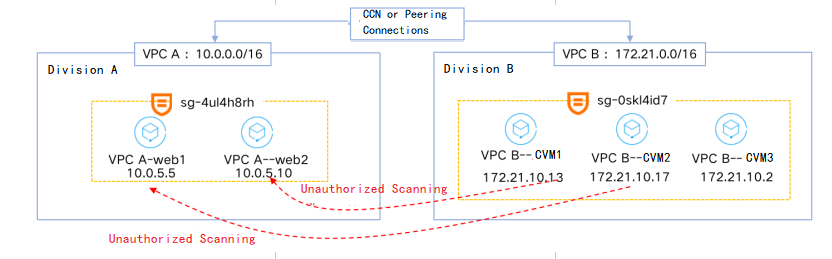
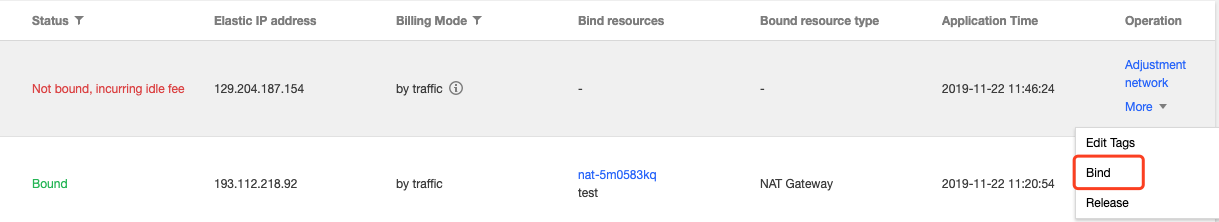
sg-4ul4h8rh in this example). Click More > Clone.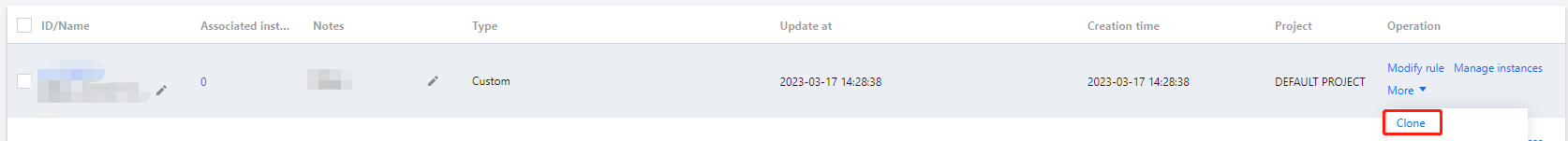
web1 in VPC A is used as a test instance, to which the cloned security group will be bound after the modification.172.21.10.13 and 172.21.10.17). Click OK.172.21.10.0/24 is also entered as the source IP address, CVM3 in VPC B will unable to access the CVMs in VPC A. Therefore, you should enter the specific IP addresses or narrow the IP range.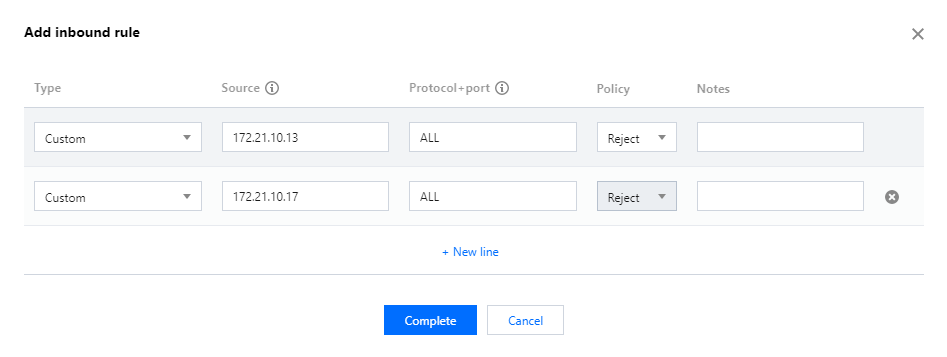
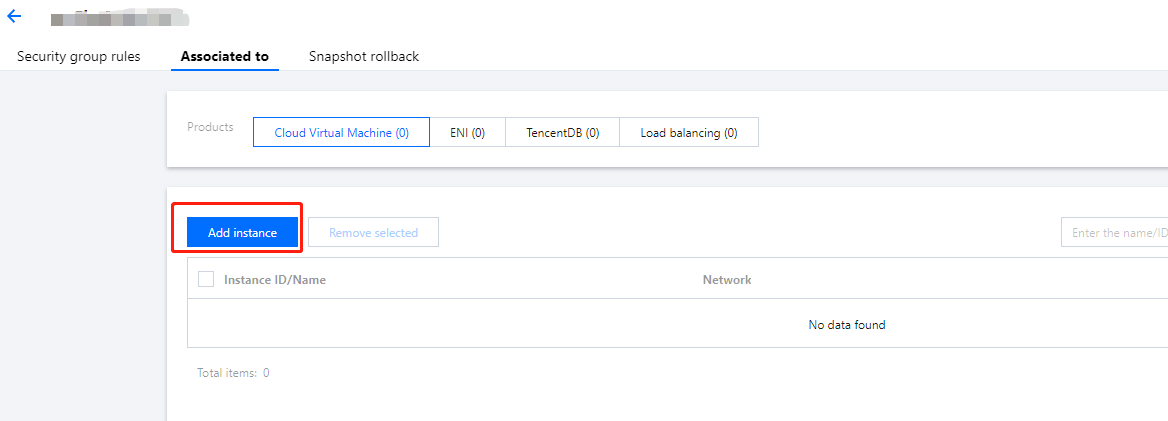
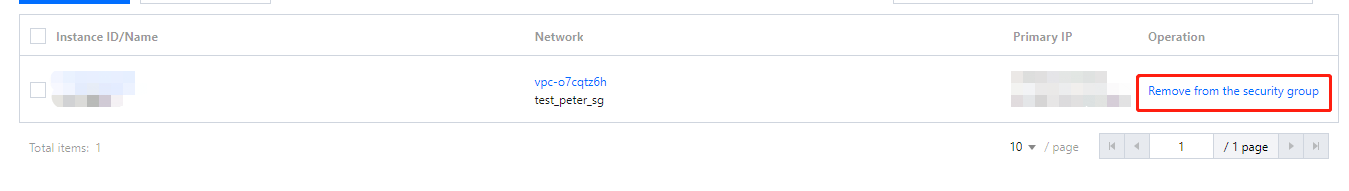
172.21.10.13 and 172.21.10.17). Click OK.172.21.10.13 and 172.21.10.17). Click OK.Last updated:2024-10-22 16:44:58
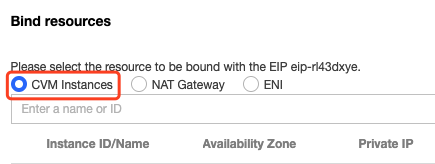
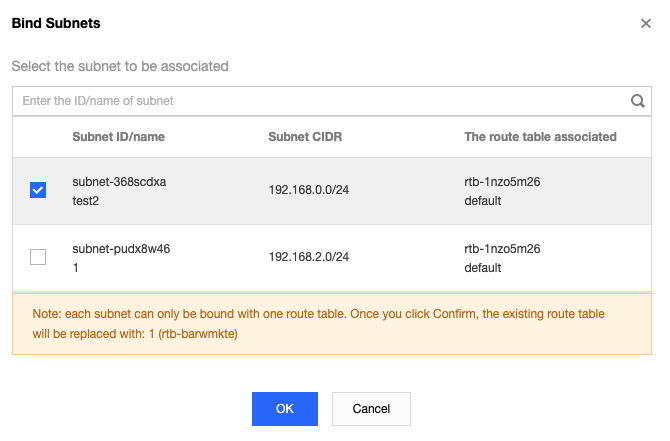
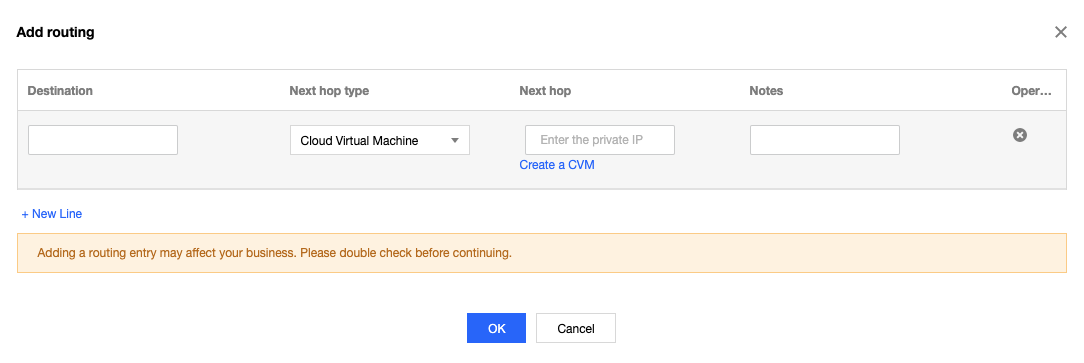
vpcGateway.sh script in usr/local/sbin.vim /usr/local/sbin/vpcGateway.sh
#!/bin/bashecho "----------------------------------------------------"echo " `date`"echo "(1)ip_forward config......"file="/etc/sysctl.conf"grep -i "^net\.ipv4\.ip_forward.*" $file &>/dev/null && sed -i \'s/net\.ipv4\.ip_forward.*/net\.ipv4\.ip_forward = 1/' $file || \echo "net.ipv4.ip_forward = 1" >> $fileecho 1 >/proc/sys/net/ipv4/ip_forward[ `cat /proc/sys/net/ipv4/ip_forward` -eq 1 ] && echo "-->ip_forward:Success" || \echo "-->ip_forward:Fail"echo "(2)Iptables set......"iptables -t nat -A POSTROUTING -j MASQUERADE && echo "-->nat:Success" || echo "-->nat:Fail"iptables -t mangle -A POSTROUTING -p tcp -j TCPOPTSTRIP --strip-options timestamp && \echo "-->mangle:Success" || echo "-->mangle:Fail"echo "(3)nf_conntrack config......"echo 262144 > /sys/module/nf_conntrack/parameters/hashsize[ `cat /sys/module/nf_conntrack/parameters/hashsize` -eq 262144 ] && \echo "-->hashsize:Success" || echo "-->hashsize:Fail"echo 1048576 > /proc/sys/net/netfilter/nf_conntrack_max[ `cat /proc/sys/net/netfilter/nf_conntrack_max` -eq 1048576 ] && \echo "-->nf_conntrack_max:Success" || echo "-->nf_conntrack_max:Fail"echo 10800 >/proc/sys/net/netfilter/nf_conntrack_tcp_timeout_established \[ `cat /proc/sys/net/netfilter/nf_conntrack_tcp_timeout_established` -eq 10800 ] \&& echo "-->nf_conntrack_tcp_timeout_established:Success" || \echo "-->nf_conntrack_tcp_timeout_established:Fail"
chmod +x /usr/local/sbin/vpcGateway.shecho "/usr/local/sbin/vpcGateway.sh >/tmp/vpcGateway.log 2>&1" >> /etc/rc.local
set_rps.sh script in usr/local/sbin.vim /usr/local/sbin/set_rps.sh
# !/bin/bashecho "--------------------------------------------"datemask=0i=0total_nic_queues=0get_all_mask() {local cpu_nums=$1if [ $cpu_nums -gt 32 ]; thenmask_tail=""mask_low32="ffffffff"idx=$((cpu_nums / 32))cpu_reset=$((cpu_nums - idx * 32))if [ $cpu_reset -eq 0 ]; thenmask=$mask_low32for ((i = 2; i <= idx; i++)); domask="$mask,$mask_low32"doneelsefor ((i = 1; i <= idx; i++)); domask_tail="$mask_tail,$mask_low32"donemask_head_num=$((2 ** cpu_reset - 1))mask=$(printf "%x%s" $mask_head_num $mask_tail)fielsemask_num=$((2 ** cpu_nums - 1))mask=$(printf "%x" $mask_num)fiecho $mask}set_rps() {if ! command -v ethtool &>/dev/null; thensource /etc/profilefiethtool=$(which ethtool)cpu_nums=$(cat /proc/cpuinfo | grep processor | wc -l)if [ $cpu_nums -eq 0 ]; thenexit 0fimask=$(get_all_mask $cpu_nums)echo "cpu number:$cpu_nums mask:0x$mask"ethSet=$(ls -d /sys/class/net/eth*)for entry in $ethSet; doeth=$(basename $entry)nic_queues=$(ls -l /sys/class/net/$eth/queues/ | grep rx- | wc -l)if (($nic_queues == 0)); thencontinueficat /proc/interrupts | grep "LiquidIO.*rxtx" &>/dev/nullif [ $? -ne 0 ]; then # not smartnic#multi queue don't set rpsmax_combined=$($ethtool -l $eth 2>/dev/null | grep -i "combined" | head -n 1 | awk '{print $2}')#if ethtool -l $eth goes wrong.[[ ! "$max_combined" =~ ^[0-9]+$ ]] && max_combined=1if [ ${max_combined} -ge ${cpu_nums} ]; thenecho "$eth has equally nic queue as cpu, don't set rps for it..."continuefielseecho "$eth is smartnic, set rps for it..."fiecho "eth:$eth queues:$nic_queues"total_nic_queues=$(($total_nic_queues + $nic_queues))i=0while (($i < $nic_queues)); doecho $mask >/sys/class/net/$eth/queues/rx-$i/rps_cpusecho 4096 >/sys/class/net/$eth/queues/rx-$i/rps_flow_cnti=$(($i + 1))donedoneflow_entries=$((total_nic_queues * 4096))echo "total_nic_queues:$total_nic_queues flow_entries:$flow_entries"echo $flow_entries >/proc/sys/net/core/rps_sock_flow_entries}set_rps
chmod +x /usr/local/sbin/set_rps.shecho "/usr/local/sbin/set_rps.sh >/tmp/setRps.log 2>&1" >> /etc/rc.localchmod +x /etc/rc.d/rc.local
Last updated:2024-10-22 16:45:21
keepalived.conf file.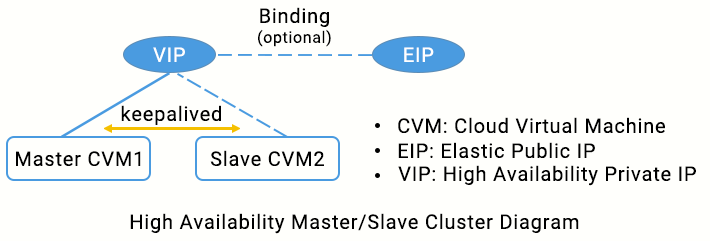
garp parameters have been configured. Because Keepalived relies on ARP messages to update the IP address, these configurations ensure that the primary device always sends ARP messages for the communication.garp_master_delay 1garp_master_refresh 5
vrrp_garp_master_repeat 1 in the “global_defs” section of the Keepalived configuration file.adver_int parameter properly to balance anti-network jitter and disaster recovery speed. If the advert_int parameter is set too small, frequent switchover and temporary active-active (split brain) may occur in case of network jitter. If the advert_int parameter is set too large, it takes a long time for primary-secondary switching to take place after the primary server fails, which cause long service interruption. Please fully assess the impact of the active-active (split brain) status on your businesses.interval parameter in the specific execution item of track_script script (such as checkhaproxy) to a larger value, avoiding the FAULT status caused by script execution timeout.10.0.0.0/24, the entered private IP address should be within 10.0.0.2 - 10.0.0.254.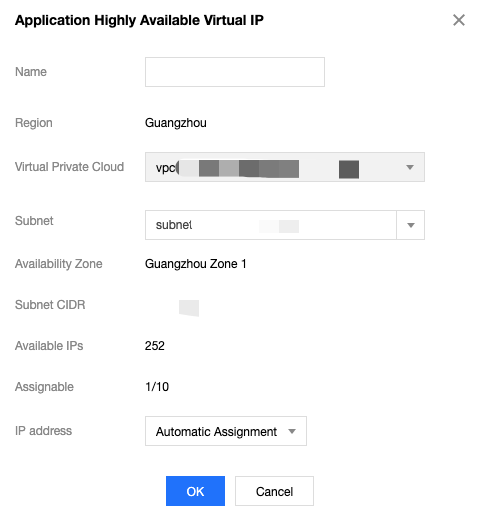
yum list keepalived
yum command.yum install -y keepalived
tar zxvf keepalived-1.2.24.tar.gzcd keepalived-1.2.24./configure --prefix=/make; make installchmod +x /etc/init.d/keepalived // Prevent occurrence of env: /etc/init.d/keepalived: Permission denied
vim /etc/keepalived/keepalived.conf to modify its configurations.! Configuration File for keepalivedglobal_defs {notification_email {acassen@firewall.locfailover@firewall.locsysadmin@firewall.loc}notification_email_from Alexandre.Cassen@firewall.locsmtp_server 192.168.200.1smtp_connect_timeout 30router_id LVS_DEVELvrrp_skip_check_adv_addrvrrp_garp_interval 0vrrp_gna_interval 0}vrrp_script checkhaproxy{script "/etc/keepalived/do_sth.sh" # Check whether the service process runs normally. Replace “do_sth.sh” with your actual script name. Run it as needed.interval 5}vrrp_instance VI_1 {# Select proper parameters for the primary and secondary CVMs.state BACKUP # Set the initial status to `Backup`interface eth0 # The ENI such as `eth0` used to bind a VIPvirtual_router_id 51 # The`virtual_router_id` value for the clusternopreempt # Non-preempt mode# preempt_delay 10 # Effective only when `state` is `MASTER`priority 100 # Configure the same weight for the two devicesadvert_int 5authentication {auth_type PASSauth_pass 1111}unicast_src_ip 172.16.16.5 # Private IP address of the local deviceunicast_peer {172.16.16.6 # IP address of the peer device}virtual_ipaddress {172.16.16.12 # HAVIP}notify_master "/etc/keepalived/notify_action.sh MASTER"notify_backup "/etc/keepalived/notify_action.sh BACKUP"notify_fault "/etc/keepalived/notify_action.sh FAULT"notify_stop "/etc/keepalived/notify_action.sh STOP"garp_master_delay 1 # How long it will take before the ARP cache can be updated after the CVM switches to the primary statusgarp_master_refresh 5 # Time interval between which the primary node sends ARP messagestrack_interface {eth0 # ENI that bound with VIP, such as `eth0`}track_script {checkhaproxy}}
vim /etc/keepalived/keepalived.conf to modify its configurations.! Configuration File for keepalivedglobal_defs {notification_email {acassen@firewall.locfailover@firewall.locsysadmin@firewall.loc}notification_email_from Alexandre.Cassen@firewall.locsmtp_server 192.168.200.1smtp_connect_timeout 30router_id LVS_DEVELvrrp_skip_check_adv_addrvrrp_garp_interval 0vrrp_gna_interval 0}vrrp_script checkhaproxy{script "/etc/keepalived/do_sth.sh"interval 5}vrrp_instance VI_1 {# Select proper parameters for the primary and secondary CVMs.state BACKUP #Set the initial status to `Backup`interface eth0 # The ENI such as `eth0` used to bind a VIPvirtual_router_id 51 # The`virtual_router_id` value for the clusternopreempt #Non-preempt mode# preempt_delay 10 # Effective only when `state` is `MASTER`priority 100 # Configure the same weight for the two devicesadvert_int 5authentication {auth_type PASSauth_pass 1111}unicast_src_ip 172.16.16.6 #Private IP of the local deviceunicast_peer {172.16.16.5 #IP address of the peer device}virtual_ipaddress {172.16.16.12 # HAVIP}notify_master "/etc/keepalived/notify_action.sh MASTER"notify_backup "/etc/keepalived/notify_action.sh BACKUP"notify_fault "/etc/keepalived/notify_action.sh FAULT"notify_stop "/etc/keepalived/notify_action.sh STOP"garp_master_delay 1 # How long it will take before the ARP cache can be updated after the CVM switches to the primary statusgarp_master_refresh 5 #Time interval between which the primary node sends ARP messagestrack_interface {eth0 # ENI that bound with VIP, such as `eth0`}track_script {checkhaproxy}}
systemctl start keepalived

vim /etc/keepalived/notify_action.sh command to add the following “notify_action.sh” script.#!/bin/bash#/etc/keepalived/notify_action.shlog_file=/var/log/keepalived.loglog_write(){echo "[`date '+%Y-%m-%d %T'`] $1" >> $log_file}[ ! -d /var/keepalived/ ] && mkdir -p /var/keepalived/case "$1" in"MASTER" )echo -n "$1" > /var/keepalived/statelog_write " notify_master"echo -n "0" /var/keepalived/vip_check_failed_count;;"BACKUP" )echo -n "$1" > /var/keepalived/statelog_write " notify_backup";;"FAULT" )echo -n "$1" > /var/keepalived/statelog_write " notify_fault";;"STOP" )echo -n "$1" > /var/keepalived/statelog_write " notify_stop";;*)log_write "notify_action.sh: STATE ERROR!!!";;esac
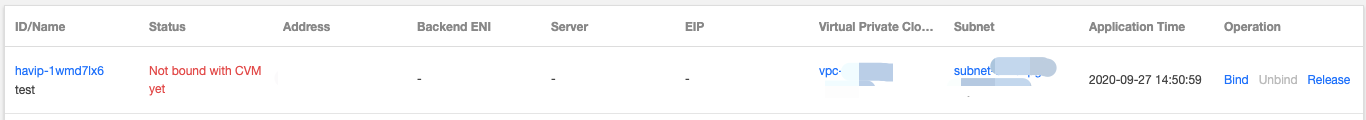
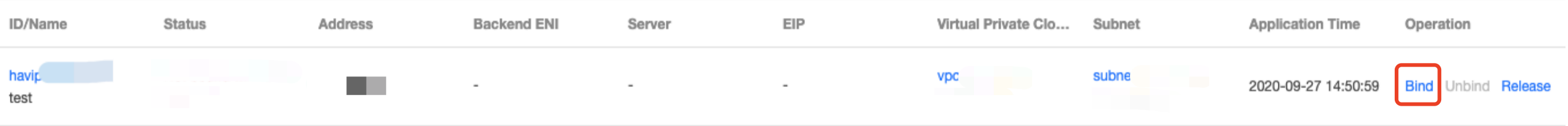
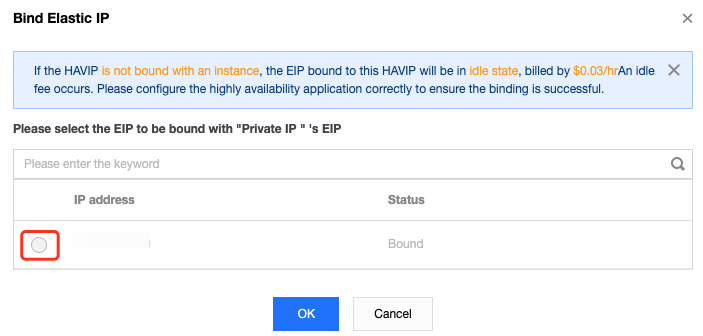
chmod a+x /etc/keepalived/notify_action.sh command to modify the script permission.ip addr show command to check whether the HAVIP is bound to the primary ENI.Last updated:2024-10-22 16:45:56
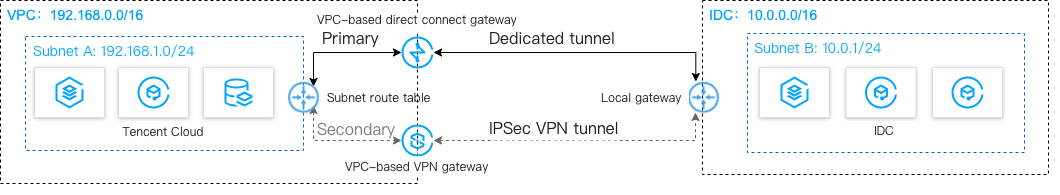
Configuration item | Sample value | ||
Network | VPC information | Subnet CIDR block | 192.168.1.0/24 |
| | Public IP of the VPN gateway | 203.xx.xx.82 |
| IDC information | Subnet CIDR block | 10.0.1.0/24 |
| | Public IP of the gateway | 202.xx.xx.5 |
202.xx.xx.5.
Last updated:2024-10-22 16:46:13
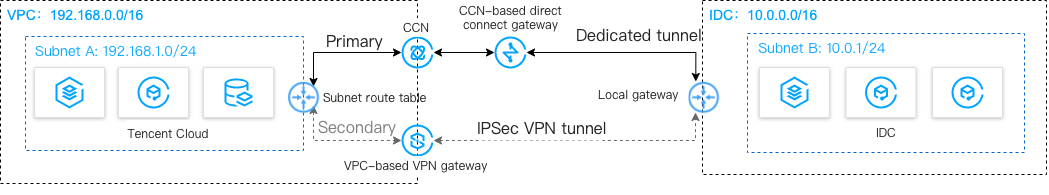
Configuration item | Sample value | ||
Network | VPC information | Subnet CIDR block | 192.168.1.0/24 |
| | Public IP of the VPN gateway | 203.xx.xx.82 |
| IDC information | Subnet CIDR block | 10.0.1.0/24 |
| | Public IP of the gateway | 202.xx.xx.5 |
10.0.1.0/24.202.xx.xx.5.
Last updated:2024-10-22 16:48:23
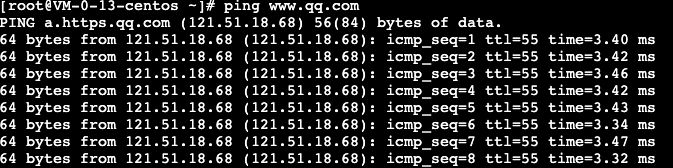
ping www.qq.com to test the data connectivity. If data is returned, the CVM instance can access the public network.