Log Shipping
Last updated:2024-08-12 17:28:05
Feature Background
Centralize and normalize logs from multiple CSC products and deliver them to message queues via the console. This facilitates data storage or integration with other systems to consume data, aiding in extracting the value of log data and meeting users' log operation and maintenance needs. Once log delivery is enabled, the collected logs will be delivered to the corresponding message queues.
Application Scenario
Log storage
According to the Cybersecurity Law of the People's Republic of China and the Information Security Grade Protection Management Measures, enterprises are required to record and store cybersecurity incidents, and the Log Storage Duration must be at least 6 months. This is to ensure the information security and network security of enterprises and to prevent the occurrence and proliferation of security incidents.
Offline Analysis
After delivering logs to Kafka/CLS, enterprises can integrate other systems for offline analysis. This helps to manage raw logs, assists in deep analysis and research of security incidents, uncovering the root causes and vulnerabilities, and improves the processing capability and level of handling security incidents.
Log Delivery to Kafka
On the log analysis page, you can configure different log types accessed by CSC to be delivered to different Topics of specified CKafka instances.
Preconditions:
To deliver logs to the message queue, you need to purchase the CSC Flagship Version and integrate relevant product logs into CSC. If you need to use either the CKafka Public Domain Name or CKafka Supporting Environment network access method, you must first go to create a Tencent Cloud Message Queue CKafka instance.
CKafka Public Domain Name Access
1. Log in to CSC Console, in the left navigation pane, click Log Analysis.
2. On the Log Analysis page, click Log shipping > Ship to Kafka.
3. On the Ship to Kafka page, CSC automatically retrieves your Tencent Cloud message queue CKafka instance, for logs already integrated with CSC, select CKafka (public domain) and configure the related parameters.
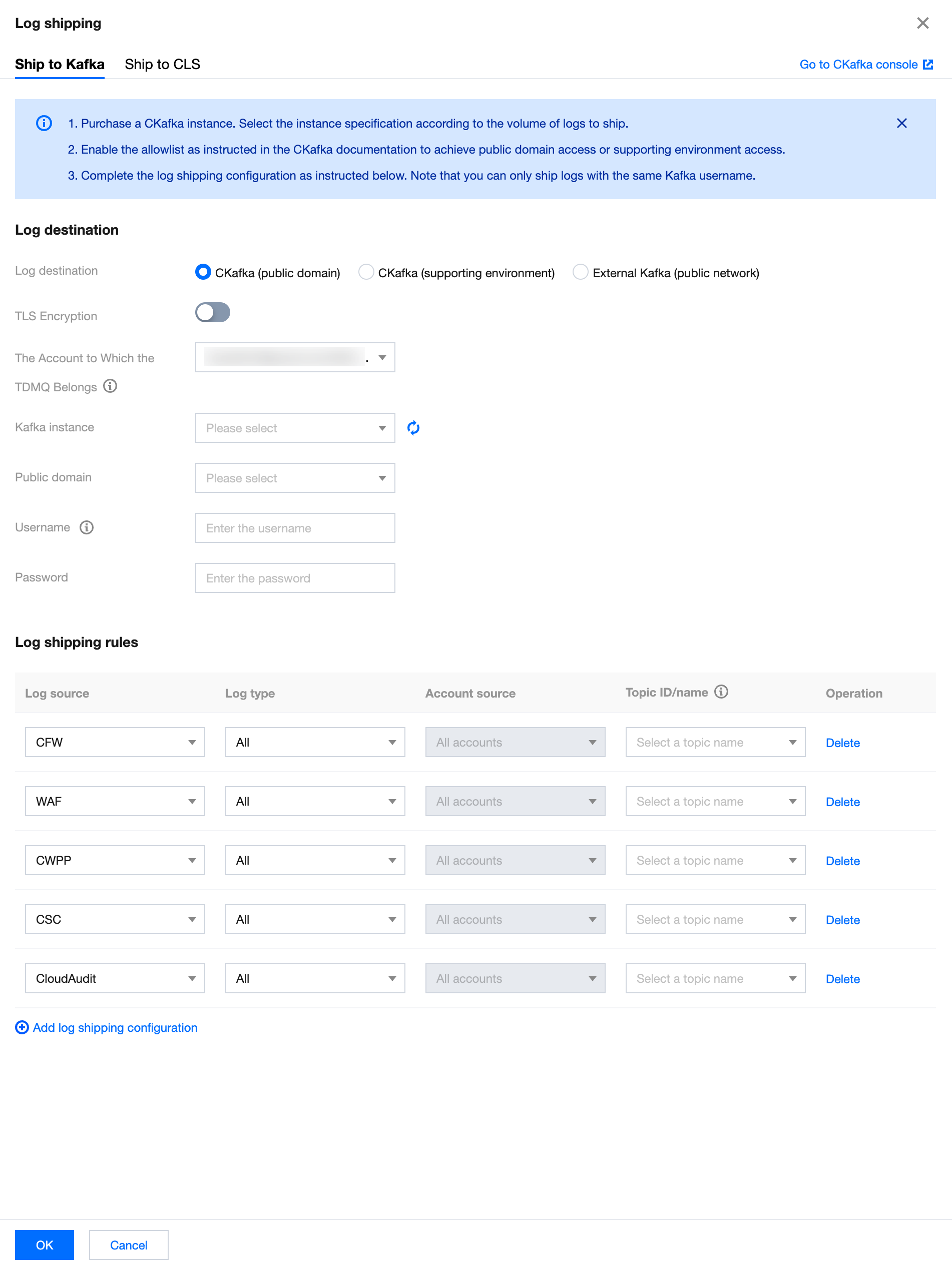
Parameter name | Description |
Log destination | CKafka (public domain). |
TLS Encryption | Select whether to enable TLS encryption. |
The Account to Which the TDMQ Belongs | Target account for shipping |
Kafka instance | CSC automatically retrieves your Tencent Cloud message queue Ckafka instance. Select the required message queue instance. |
Public domain | Select the required public domain name. |
Username | Please enter the selected message queue instance's username. |
Password | Please enter the selected message queue instance's password. |
Log source | Supports selecting logs from CWPP, CFW, WAF, CSC, Anti-DDoS, SaaS Bastion Host, CloudAudit, and Network Honeypot. |
Log type | The log type varies depending on the chosen log source. |
Topic ID/Name | Select the required Topic. |
Operation | Add: click Add log shipping configuration, multiple log sources can be added. Delete: click Delete in the log operation column of the target log. After second confirmation, the log delivery task corresponding to the log type of this log source can be deleted. Edit: If it is not the first time configuring log delivery, you can click Modify Configuration on the log delivery page to modify the related log delivery. |
4. After confirming that everything is correct, click OK to deliver the collected logs to the corresponding message queue.
5. On the Log Delivery page, you can view details of synchronous access method, access object, message queue status, username, and other message queue details, as well as log source, log type, account source (under multiple accounts), Topic ID/Name, Topic delivery status, delivery switch, and other information. It also allows modifications to message queue and Topic configurations, and viewing the status of the message queue and each Topic.
CKafka Supporting Environment Access
1. Log in to CSC Console, in the left navigation pane, click Log Analysis.
2. On the Log Analysis page, click Log shipping > Ship to Kafka.
3. On the Ship to Kafka page, CSC automatically retrieves your Tencent Cloud message queue CKafka instance and the log source already integrated with CSC. Select CKafka (supporting environment) and configure the related parameters.
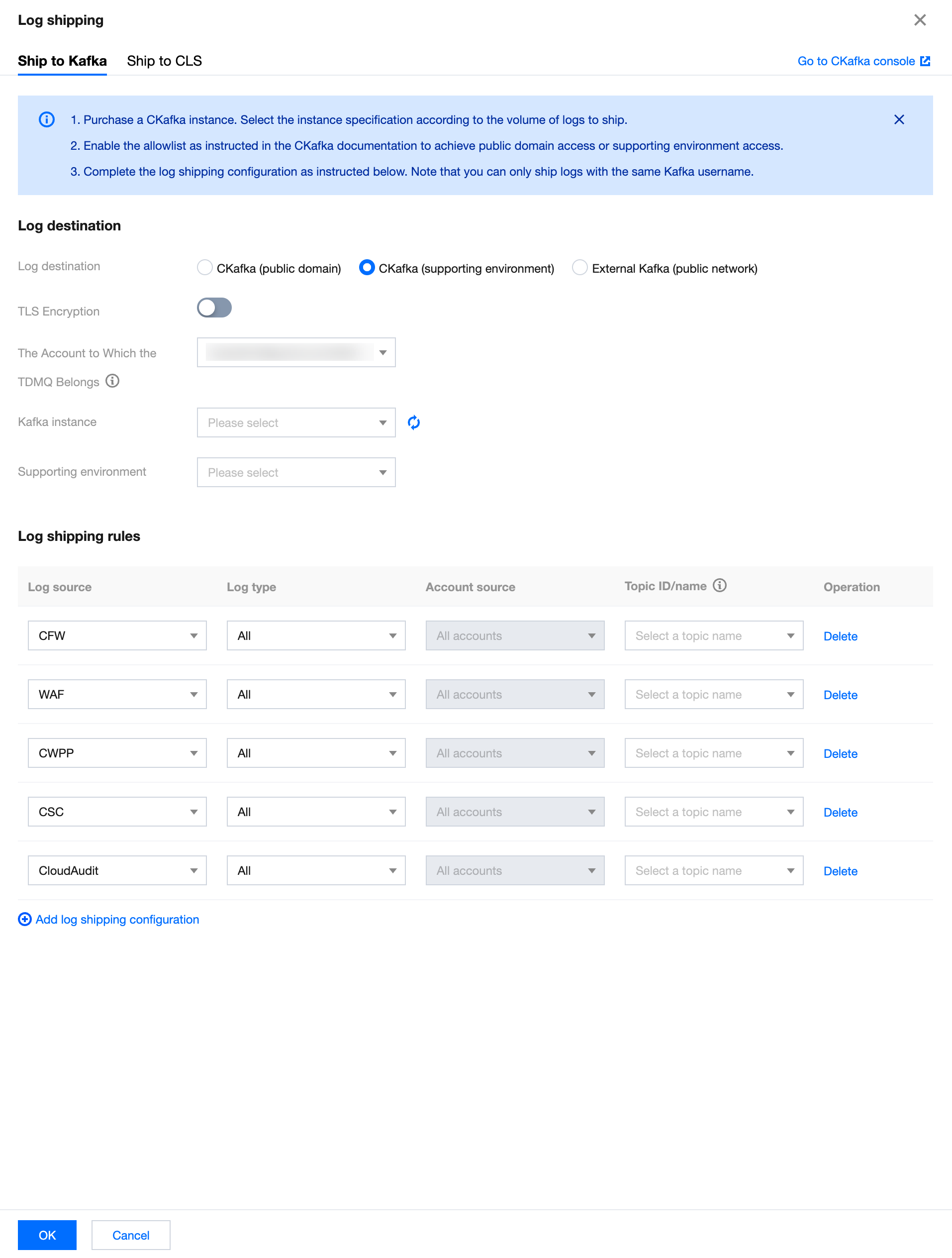
Parameter name | Description |
Log destination | CKafka (supporting environment). |
TLS Encryption | Select whether to enable TLS encryption. |
The Account to Which the TDMQ Belongs | Target account for shipping |
Kafka instance | CSC automatically retrieves your Tencent Cloud message queue Ckafka instance. Select the required message queue instance. |
Supporting environment | Select the required supporting environment. |
Log source | Supports selecting logs from CWPP, CFW, WAF, CSC, Anti-DDoS, SaaS Bastion Host, CloudAudit, and Network Honeypot. |
Log type | The log type varies depending on the chosen log source. |
Topic ID/Name | Select the required Topic. |
Operation | Add: click Add log shipping configuration, multiple log sources can be added. Delete: click Delete in the log operation column of the target log. After second confirmation, the log delivery task corresponding to the log type of this log source can be deleted. Edit: If it is not the first time configuring log delivery, you can click Modify Configuration on the log delivery page to modify the related log delivery. |
4. After confirming that everything is correct, click OK to deliver the collected logs to the corresponding message queue.
5. On the Log Delivery page, you can view details of synchronous access method, access object, message queue status, username, and other message queue details, as well as log source, log type, account source (under multiple accounts), Topic ID/Name, Topic delivery status, delivery switch, and other information. It also allows modifications to message queue and Topic configurations, and viewing the status of the message queue and each Topic.
Other Kafka Public Network Access
1. Log in to CSC Console, in the left navigation pane, click Log Analysis.
2. On the Log Analysis page, click Log shipping > Ship to Kafka.
3. In the Ship to Kafka page, select External Kafka (public network) and configure the related parameters.
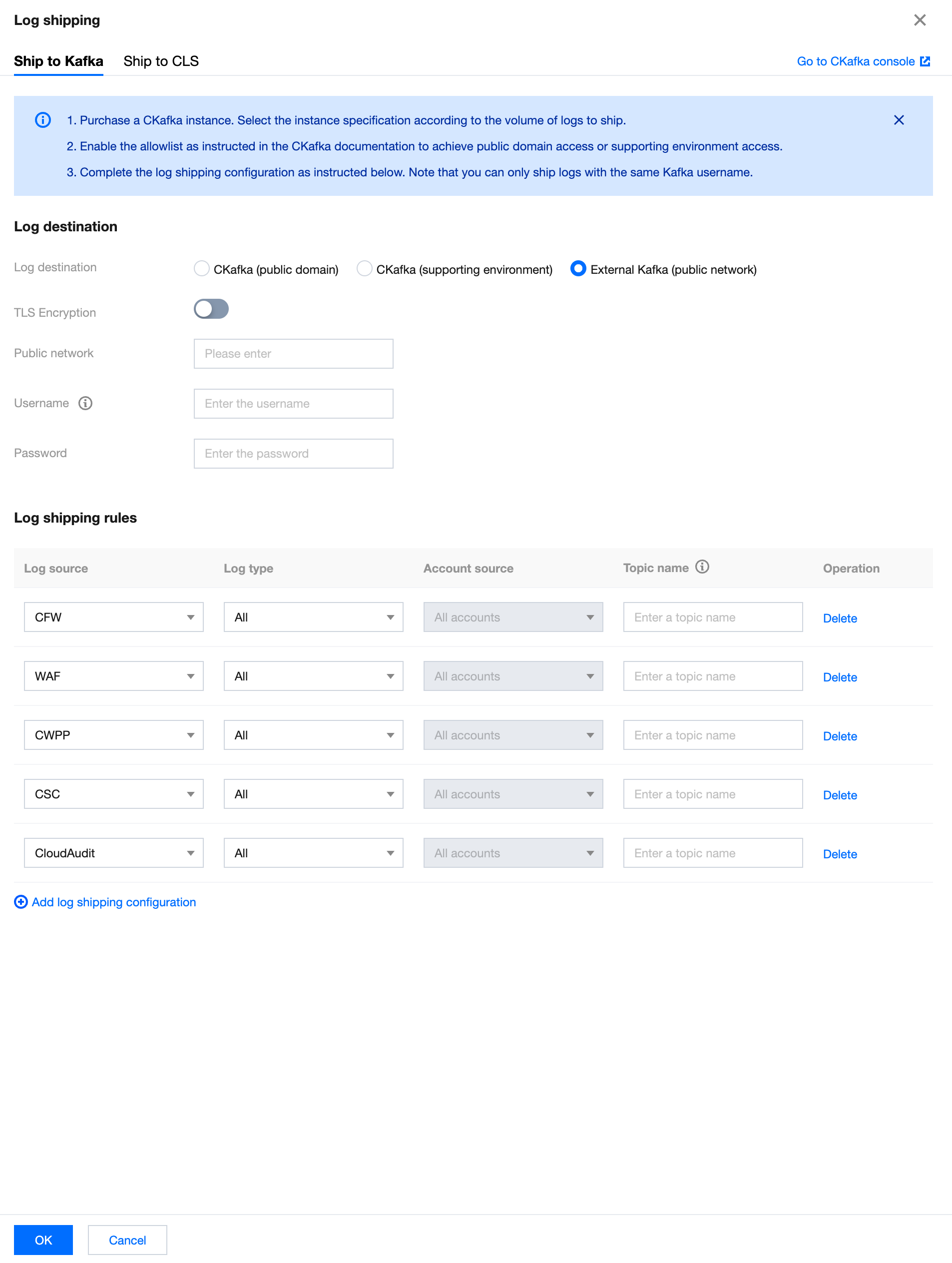
Parameter name | Description |
Log destination | External Kafka (public network). |
TLS Encryption | Select whether to enable TLS encryption. |
Public network | Enter the public network information based on actual needs. |
Username | Please enter the selected message queue instance's username. |
Password | Please enter the selected message queue instance's password. |
Log source | Supports selecting logs from CWPP, CFW, WAF, CSC, Anti-DDoS, SaaS Bastion Host, CloudAudit, and Network Honeypot. |
Log type | The log type varies depending on the chosen log source. |
Topic name | Enter the desired Topic name. |
Operation | Add: click Add log shipping configuration, multiple log sources can be added. Delete: click Delete in the log operation column of the target log. After second confirmation, the log delivery task corresponding to the log type of this log source can be deleted. Edit: If it is not the first time configuring log delivery, you can click Modify Configuration on the log delivery page to modify the related log delivery. |
4. After confirming that everything is correct, click OK to deliver the collected logs to the corresponding message queue.
5. On the log delivery page, you can view details such as synchronous access method, access object, message queue status, username, log source, log type, account source (under multiple accounts), Topic name, Topic delivery status, delivery switch, etc., and you are allowed to modify the message queue and Topic configuration.
Shipping Logs to CLS
On the log analysis page, you can configure different types of logs connected to CSC and ship them to different specified log topics in CLS respectively.
1. Click the Log shipping at the top left corner to open the log shipping configuration pop-up. If the CLS service has not been activated before, you need to click Go to Authorization, agree to service authorization, and create a service role to proceed with more log shipping configurations.
Note:
CSC supports shipping logs to CLS, enabling comprehensive CLS services like log collection, log storage, and log search. After the current account authorizes access to CLS and enables shipping logs to CLS, a pay-as-you-go storage space will be automatically created in CLS, along with a pay-as-you-go bill. For details, see CLS Billing Information.
2. After the authorization is completed, you can configure different log topics for logs to be shipped. (Logs not to be shipped do not need to be configured.)
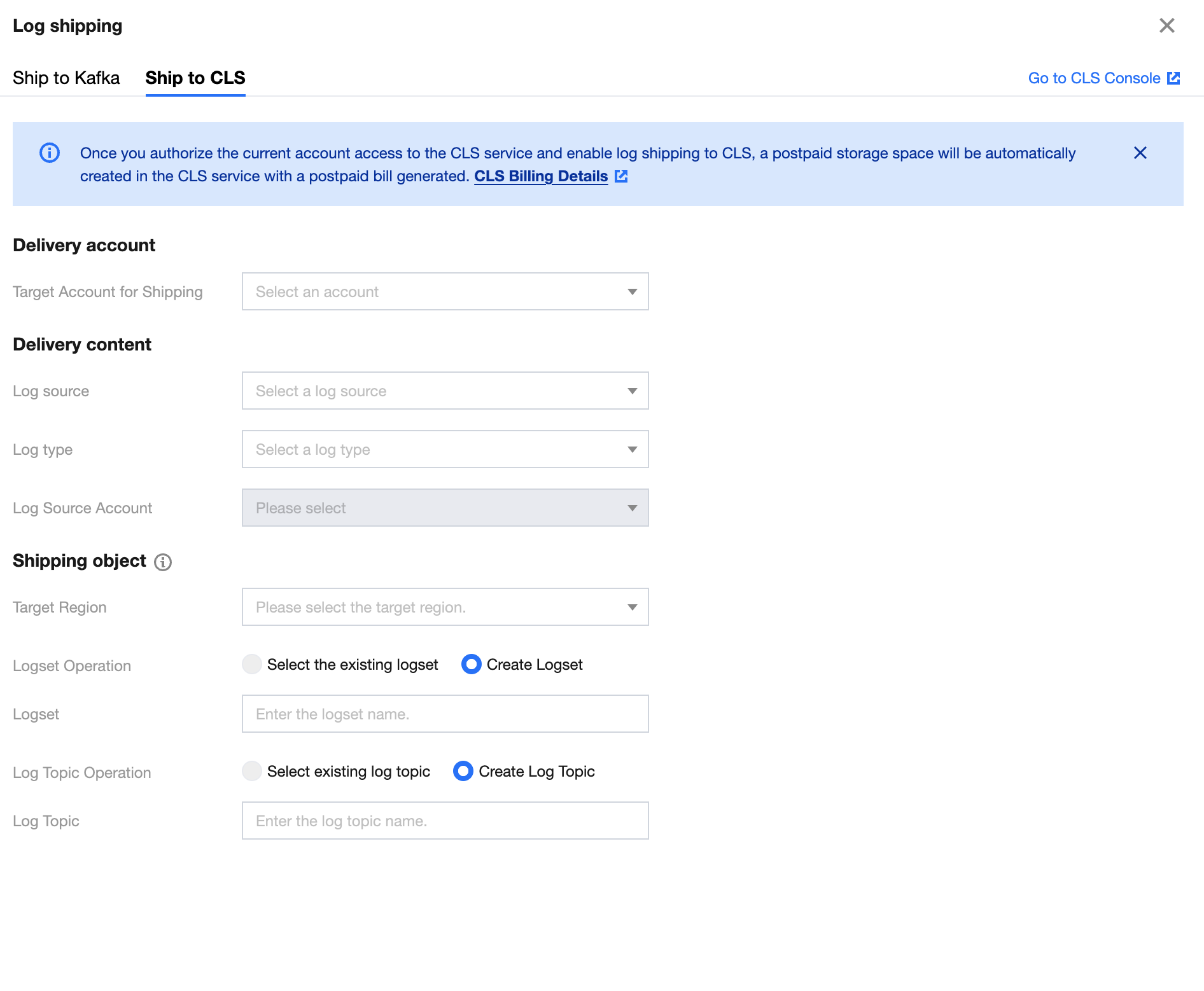
Parameter | Description |
Target account for shipping | Target account for shipping |
Log source | Supports selecting logs from CWPP, CFW, WAF, CSC, Anti-DDoS, SaaS Bastion Host, CloudAudit, and Network Honeypot. |
Log type | The log type varies depending on the selected log source. |
Log source account | Names of multi-accounts corresponding to the selected log source. |
Target region | Enter the target region for shipping. |
Logset operation | Select to ship to an existing logset or create a logset for shipping. |
Logset | Enter the name of the new logset. / Select an existing logset. |
Log topic operation | Select to ship to an existing log topic or create a log topic for shipping. CLS only supports shipping to log topics created in CSC. |
Log topic | Enter the name of the new log topic. / Select an existing log topic. |
3. After everything is confirmed, you can click OK to ship the collected logs to the corresponding log topic.
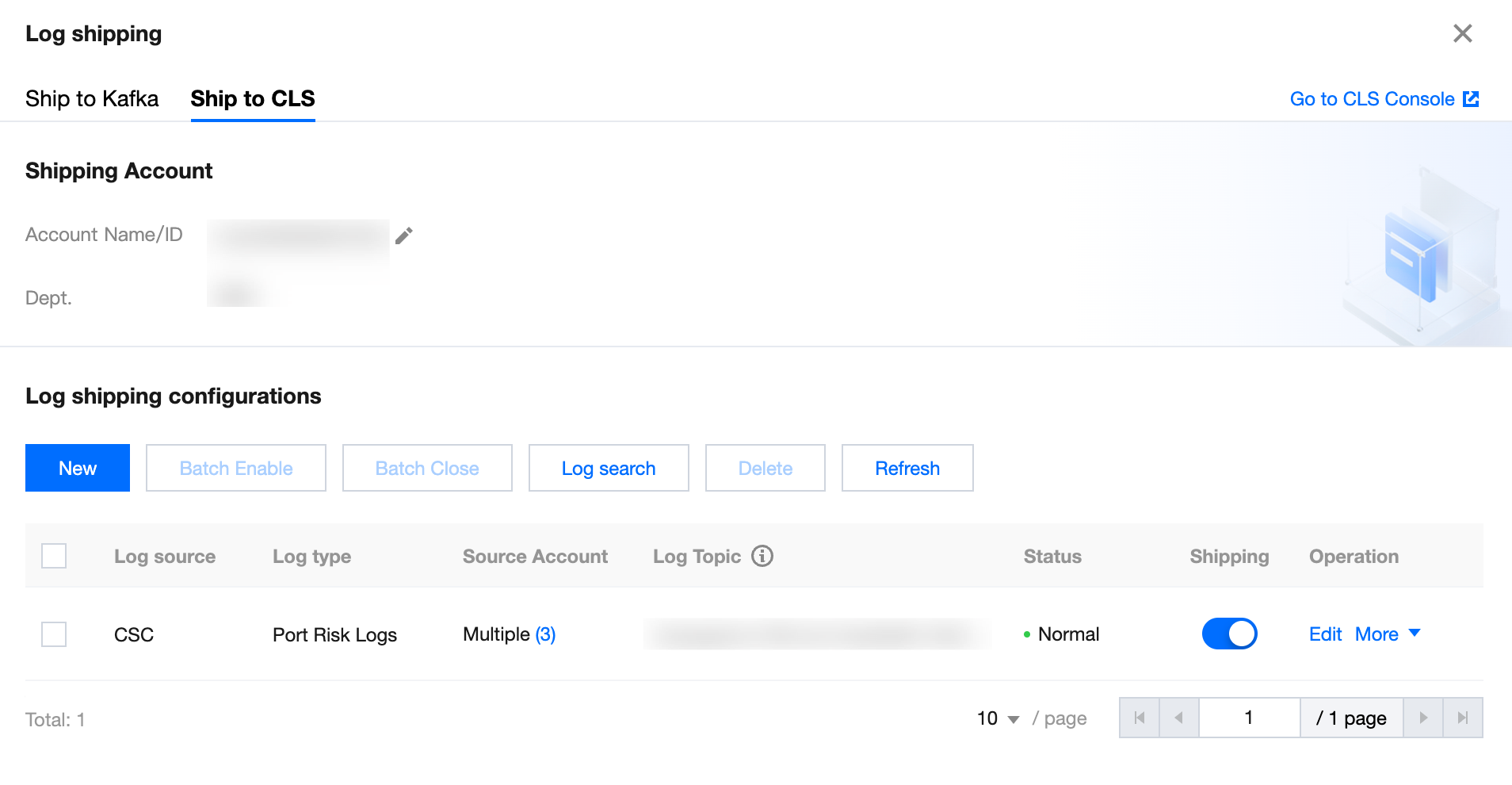
4. On the log shipping page, you can view the account name/ID, department, log source, log type, source account (under multi-account), log topic, shipping status, shipping switch, and other information. It also allows you to edit shipped tasks, (batch) delete tasks, (batch) enable/disable tasks, (batch) refresh, and perform log search.
Delivery and Delivering Objects
Multi-account management
After enabling the Multi-account Management feature, multi-account and multi-product log delivery is supported.
1. Log in to CSC Console, in the left navigation pane, click Log Analysis.
2. On the Log Analysis page, click Multi-account Management at the top right.
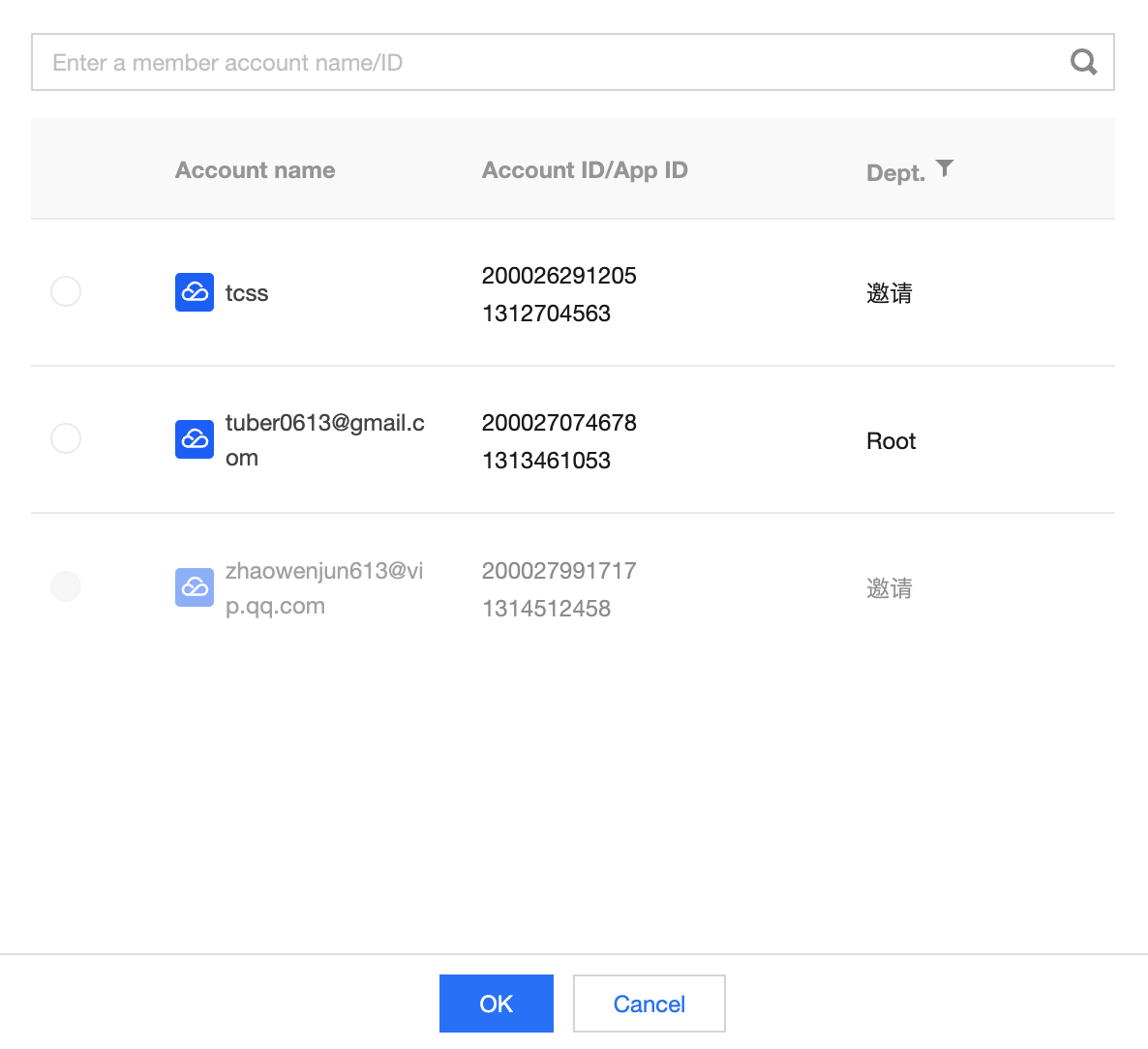
3. On the Multi-account Management page, select the required account, click OK.
Scenario Description | Not configured | Configuration completed |
The Administrator/Delegated Administrator unifies the delivery of multiple product logs from all accounts into a single Kafka. | After selecting all accounts in the upper right corner to configure log delivery, under both Public Domain Access and Supporting Environment Access for CKafka, the Administrator's CKafka will be automatically retrieved. You can select the required Tencent Cloud Message Queue. | Displays the Administrator's message queue status, user information, and other message queue details, along with synchronized configured log sources, log types, account sources, and delivery status. |
The Administrator/Delegated Administrator manages other accounts' logs by configuring multiple product log deliveries for other accounts. | After selecting other accounts in the upper right corner to configure log delivery, under both Public Domain Access and Supporting Environment Access for CKafka, the other account's CKafka will be automatically retrieved. You can select the required Tencent Cloud Message Queue. | Displays other accounts' message queue status, user information, and other message queue details, along with synchronized configured log sources, log types, and delivery status. |
The Administrator/Delegated Administrator manages the current account's (Administrator/Delegated Administrator) logs by configuring multiple product log deliveries for the current account. | After selecting the current account (Administrator/Delegated Administrator) in the upper right corner to configure log delivery, under both Public Domain Access and Supporting Environment Access for CKafka, the CKafka for the current account (Administrator/Delegated Administrator) will be automatically retrieved. You can select the required Tencent Cloud Message Queue. | Displays the current account's (Administrator/Delegated Administrator) message queue status, user information, and other message queue details, along with synchronized configured log sources, log types, and delivery status. |
Single account management
Only supports multi-product log delivery for the current account.
Not configured: When configuring log delivery, CKafka for the current account will be automatically retrieved under both CKafka Public Domain Access, and CKafka Supporting Environment Access network access methods. You can select the required Tencent Cloud Message Queue.
Note:
If the current account is managed by an Administrator/Delegated Administrator, the Administrator/Delegated Administrator may edit the log delivery configuration of the current account.
After configuration: Displays the current account's message queue status, user information, and other message queue details, along with synchronized configured log sources, log types, delivery status, and other log delivery details.
FAQs
How is log delivery charged?
Public Network Log Delivery Egress IP allowlist
106.55.200.0/24106.55.201.0/24106.55.202.0/2481.71.5.0/24134.175.239.0/24193.112.130.0/24193.112.164.0/24193.112.221.0/24111.230.173.0/24111.230.181.0/24129.204.232.0/24193.112.129.0/24193.112.153.0/24106.52.11.0/24106.55.52.0/24118.89.20.0/24193.112.32.0/24193.112.60.0/24106.52.106.0/24106.52.67.0/24106.55.254.0/2442.194.128.0/2442.194.133.0/24106.52.69.0/24118.89.64.0/24129.204.249.0/24182.254.171.0/24193.112.170.0/24106.55.207.0/24119.28.101.0/24150.109.12.0/24
Which products and log types does Log Delivery support?
Product | Log type | Log type |
Cloud Firewall | Access control log | CFW Rule Hit Logging is generated based on access control rules configured by users in Internet Border Firewall, NAT Boundary Firewall, VPC-to-VPC Firewall, and Enterprise Security Group. |
| Zero Trust Protection Log | Zero Trust Protection Log in CFW includes Remote Operation and Maintenance Login, Web Service Access, and Database Access, along with log in to and access service details. |
| Intrusion Defense Log | CFW Based on the "Observation Mode" and "Interception Mode", all security events generated and recorded include four lists: "External Intrusion, Host Compromise, Lateral Movement, Network Honeypot". They allow for the examination of inbound and outbound security event details. |
| Flow Logs | CFW Internet Border Firewall and NAT Boundary Firewall monitor north-south traffic generated by inbound and outbound actions and east-west traffic between VPCs. |
| Operations logs | In CFW, all operational behaviors and details based on the security policies and switch pages within the account are recorded. |
Web Application Firewall | Attack Logs | WAF provides attack logs that record the attack time, attack source IP, attack type, and attack details. |
| Access Log | WAF records access log information for the protected domain. |
Cloud Workload Protection Platform | Intrusion Detection Log | CWPP provides security logs for multi-dimensional intrusion detection, including Trojans, high-risk commands, local privilege escalation, and all log in to behavior events. |
| Vulnerability Management Log | CWPP security logs for detailed situations of vulnerability security events. |
| Advanced Defense Log | CWPP logs for Advanced Defense, including Java Memory Horse and attack detection. |
| Client-related logs | CWPP detected that the client was offline abnormally for over 24 hours and did not come back online. The client was Uninstall (for servers running Linux System) logs. |
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No
Feedback

