Baseline Management
Last updated:2024-08-13 16:29:50
This document describes how to use the Baseline Management to ensure baseline security for servers.
Overview
Tencent Cloud CWPP (Cloud Workload Protection Platform) allows you to perform periodic and quick baseline checks on servers based on default or custom baseline policies. You can also specify check items and servers to be included in baseline policies. By providing information such as baseline check pass rates, detected risks, threat levels, and suggestions on how to fix the vulnerabilities, the product helps you better manage the baseline security of your servers.
CWPP Editions
Basic Edition : If this is the first time you use it, it supports detection of all hosts in the default policy, but it can only display 5 results. It does not support baseline policy management, one-click detection, or periodic detection.
Pro Edition : Supports baseline policy management, allowing users to create or edit policies. It supports periodic and one-click detection for baseline policies.
Ultimate Edition : Supports baseline policy management, allowing users to create or edit policies. It supports periodic and one-click detection for baseline policies. Also supports custom weak password.
Operation Guide
1. Log in to the CWPP console, and in the left sidebar, choose Baseline Management .
2. The baseline management page provides settings for baseline policies, periodic detection, and one-click detection for specified policies. It supports viewing the pass rate and risk status of baseline policies, as well as the list of baseline detection results. You can view details of the baselines and check items and their repair plans. You can also ignore specific check items for specified servers.
Baseline policies
A baseline policy is a collection of user-defined baseline check items, allowing you to track baseline pass rates and detected risks based on the dimensions included in the policy.
Tencent Cloud default baseline policies: Tencent Cloud CWPP provides default baseline policies based on mainstream network security baseline check items, including: weak password policy, CIS baseline policy, and Tencent Cloud best security practice policy. You can add check items and servers to be checked to a default baseline policy, under which the check is conducted once every 7 days by default (at 00:00 of the day).
Note:
Pass rate of policy = the number of servers that pass all check items under this policy/the number of all servers checked under this policy
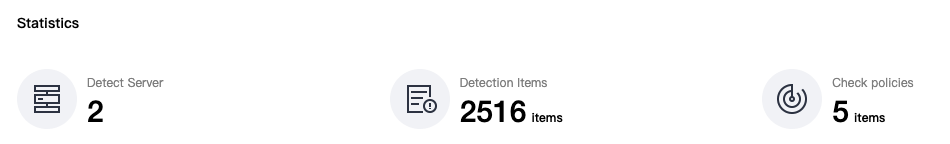
Add Baseline Policies
1.1 Click Baseline Settings in the upper right corner of the baseline check result section.
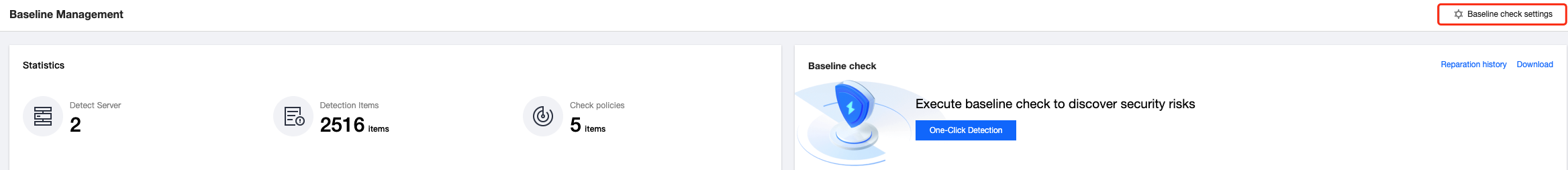
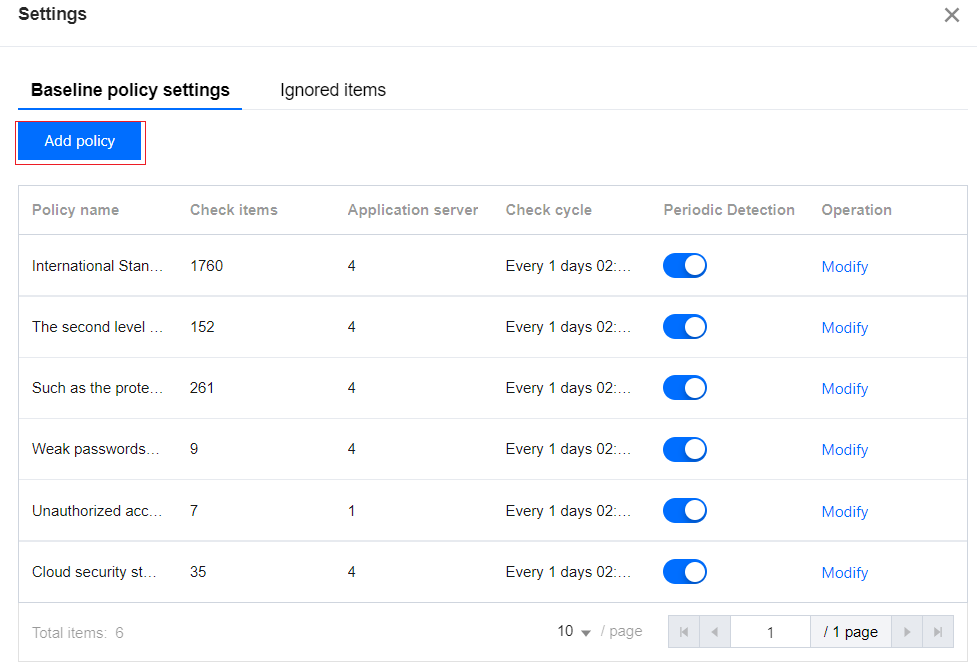
1.2 In the "Baseline Policy Settings" section of the "Baseline Settings" page, click Add Policies.
1.3 Enter the name of the new policy (must be different from existing policy names), specify Interval, Baseline Types, and Target Assets in the "Add Policies" page, and then click "Save and update".
Note:
A maximum of 20 baseline policies. If this limit is reached, you must delete an existing policy before you can create a new one.
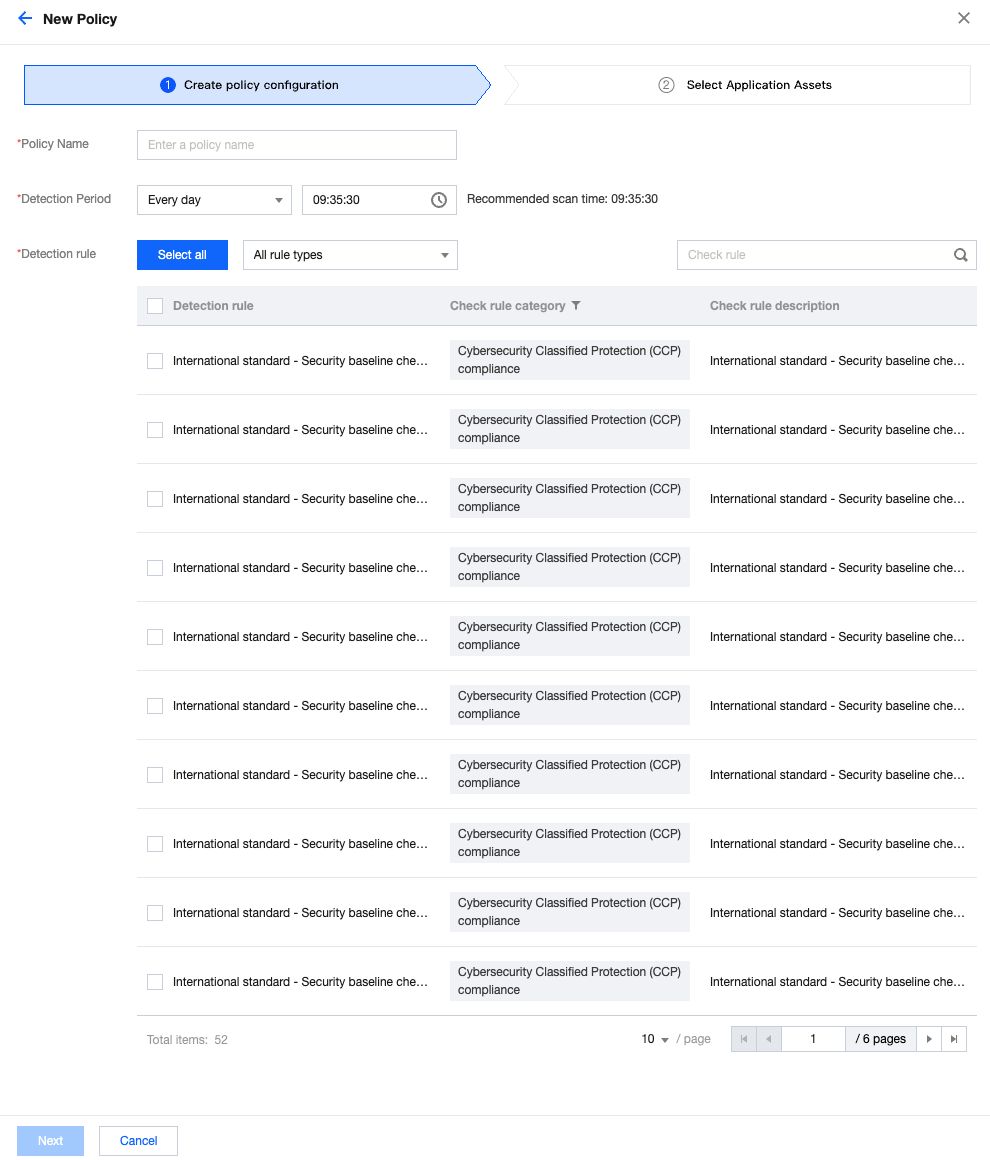
1.4 Select the application assets based on actual needs, and click Complete.
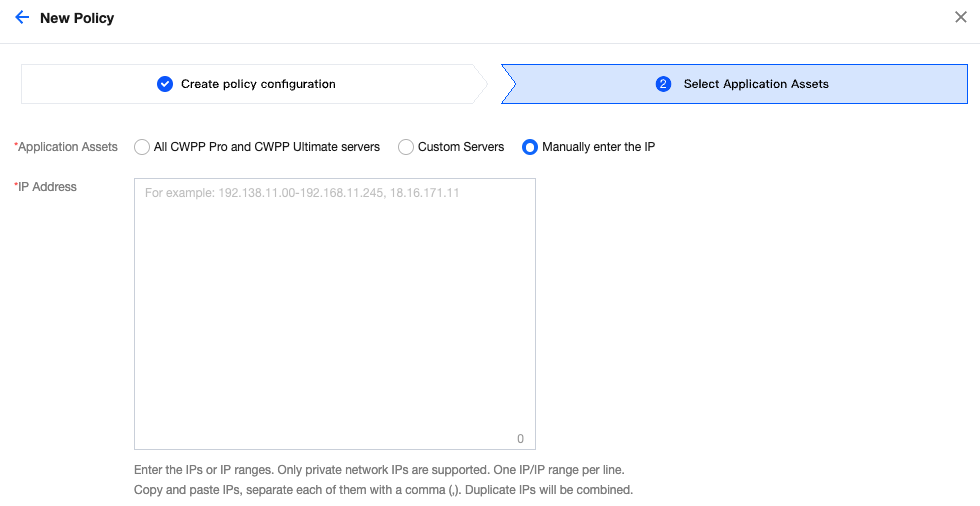
Baseline Detection
Tencent Cloud CWPP supports regular inspections and One-Click Detection for baseline check items and allows checking specified baseline items on designated CVMs.
Note
If this is not the first time you use the baseline detection, you need to activate CWPP Pro edition or Ultimate edition to proceed with baseline detection.
One-click Detection
First Detection : When you use the baseline detection feature for the first time, We provide you with a free detection service for full-scale baseline policy check and comprehensive scan across all your servers, assisting you in identifying potential baseline security risks. We will display 5 baseline risks. If you need more baseline security features, we recommend upgrading to the Pro edition or Ultimate edition.
1.1 For baseline detection results display module, click Trial Detection .
1.2 In the Detection Prompt pop-up window:
Operation 1: Select the baseline policy to be checked, click Start Inspection (the inspection usually takes 2-5 minutes). After the inspection is complete, the results will be displayed as visualized charts on the vulnerability management page.
Operation 2: Click upgrade now to jump to the CWPP upgrade interface and upgrade CVM to the Pro edition.
Non-first Time Detection : When this is not the first time for you to use the baseline detection, you can choose the baseline policy to be checked, and click One-Click Detection (the inspection usually takes 2-10 minutes). If you do not have a Pro edition server yet, we recommend upgrading to the Pro edition immediately.
Periodic Detection
1. In the top right corner of the baseline management page, click Baseline check settings .
2. On the baseline check settings tab, you can configure periodic detection and manage ignored items.
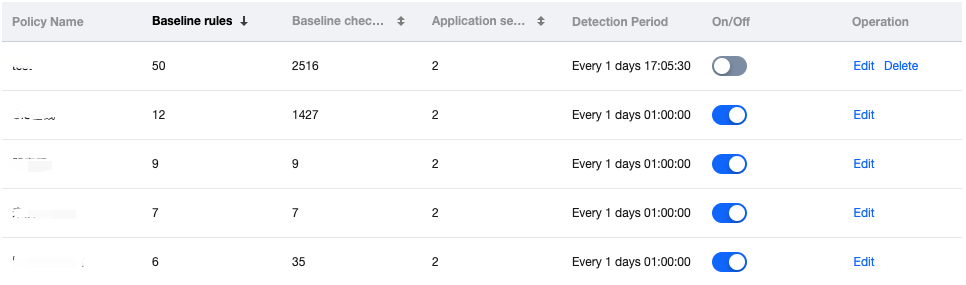
Periodic Detection Settings : On the baseline policy settings tab, you can add or modify policies, set check cycle, and also enable or disable periodic detection. Additionally, it supports the deletion of user-defined policies.
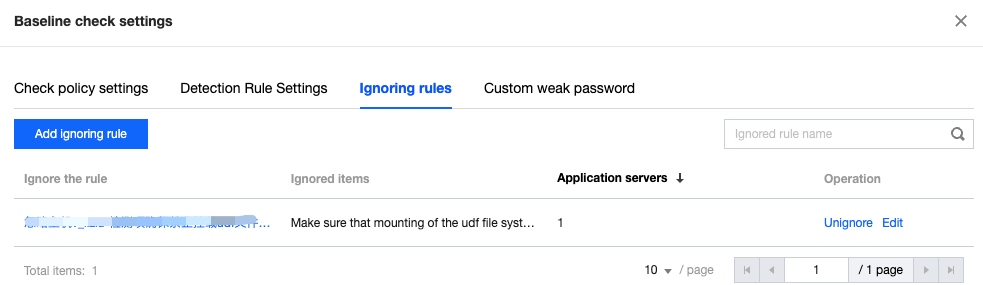
Ignoring rules Management : Under the ignored items management tab, you can view the ignored check items and their details, and perform unignore operations.
Periodic Check
1. Click Baseline Settings in the upper right corner of the baseline check result section.
2. You can set the interval of periodic checks and manage ignored check items
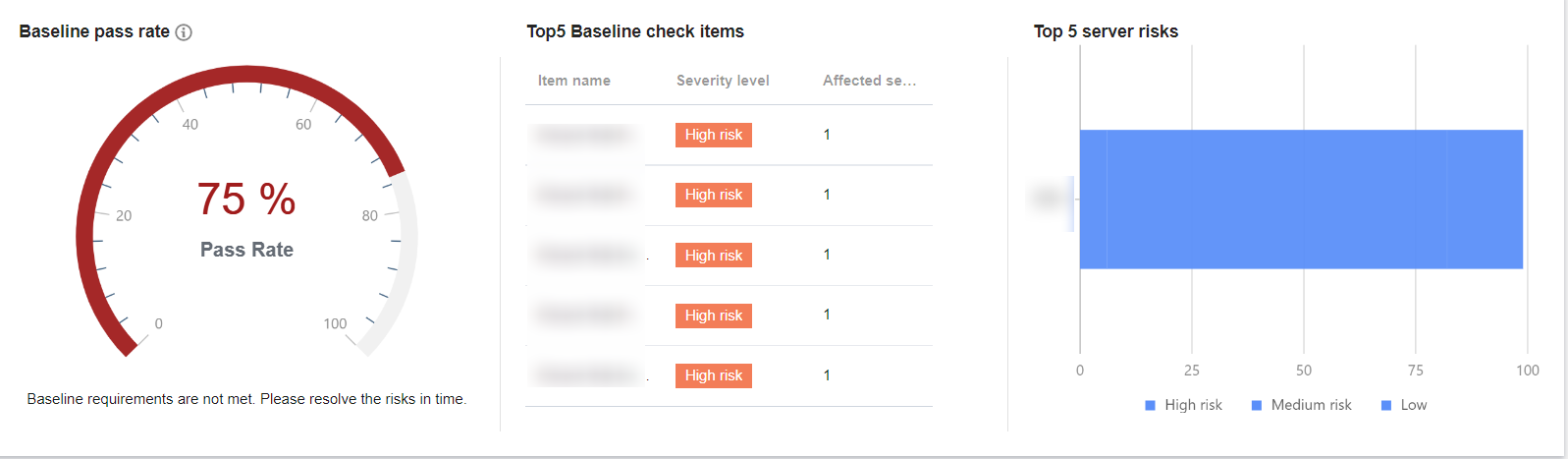
Visualized baseline data
After selecting baseline policies and running a check, the Baseline Management page shows the number of checked servers, number of check items, the pass rate of the baseline policies, top 5 baseline check items, and top 5 risk items, which are categorized by threat level.
Baseline check result list
At the bottom of the Baseline Management page, the list of baseline check results is shown, where you can view baseline details, perform fuzzy search and status filtering for a single baseline, and download all tables.
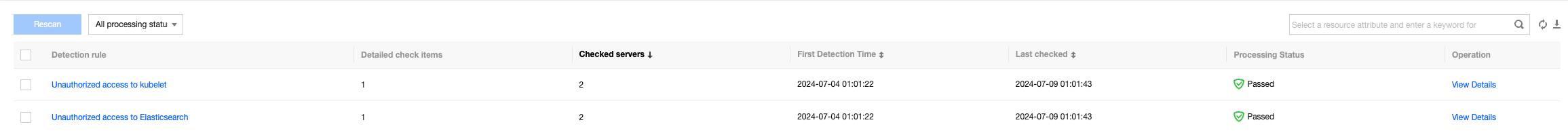
Field description:
Baseline Name: The name of the current baseline set, which contains multiple check items of the same category.
Threat Level: Divided into Severe, High, Medium, and Low
Baseline Check Items: The total number of check items included in the current baseline set.
Affected servers: The number of servers that do not pass every check item in the current baseline set under the baseline policy, i.e. the number of servers affected by this baseline set.
Last Checked: The time when the check items in the baseline set were last executed on a server.
Status: Pass, Fail and In Progress.
Operation: Allows you to view baseline details and run a recheck for failed baselines.
Rescan:
Option 1: Select the baselines for a recheck, and click Recheck in the upper left corner of the list to run a recheck for the selected baselines at one time.
Option 2: Click Recheck on the right of the desired baseline to run a recheck for the baseline.
View details:
In the baseline check result list, locate the desired baseline, and then click Details in the Action column on the right to open the baseline details page.
The baseline details page shows the description and threat level of the baseline, as well as the list of affected servers. The server list supports fuzzy search for individual servers, status filtering, batch re-detection of servers, and viewing details of individual servers. In the action bar on the right of the target server, click Details to enter the detection details page.
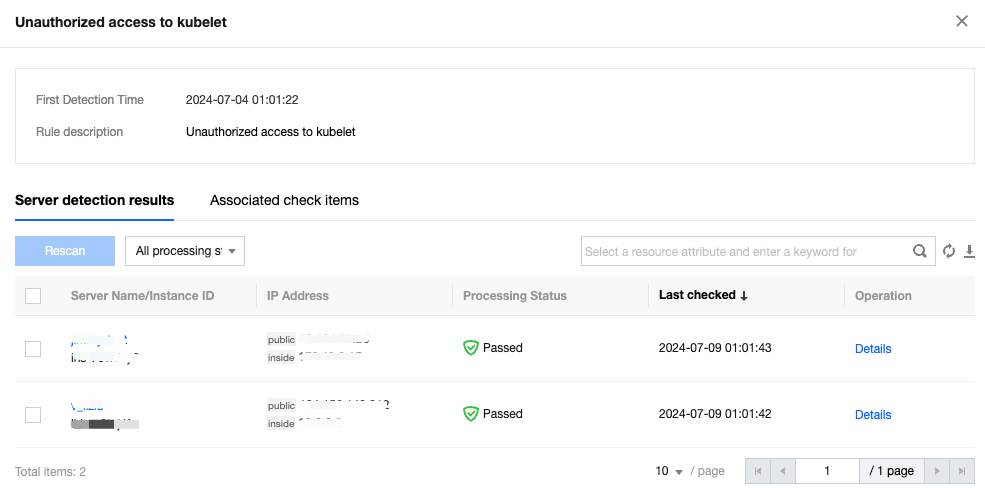
The check details page shows the basic information including baseline name, server name, and check items.
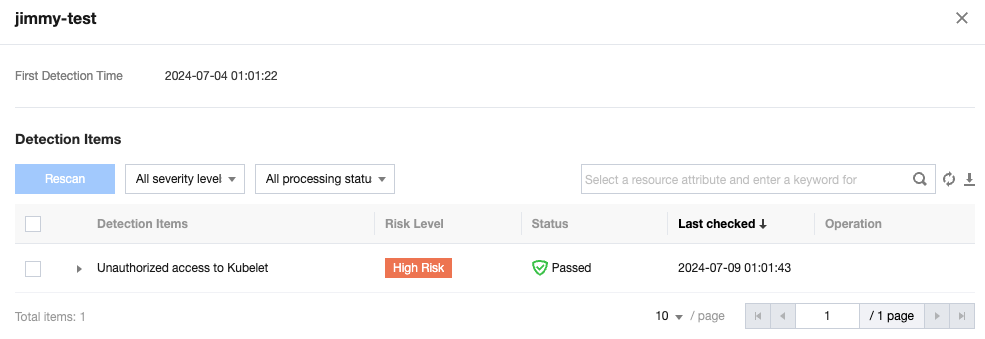
You can run a Recheck or select Ignore for multiple check items. The ignored items can be viewed on the ignored risk item management page.
You can filter check items by threat level or status.
When you hover the mouse cursor over a check item, the details of the item, and solutions to the detected issue will appear.
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No
Feedback

