安全概览
最后更新时间:2024-02-07 09:04:14
本文档为您介绍容器安全服务各个安全模块的整体安全情况概览。
实时展示容器安全风险概览信息和容器安全事件新增趋势等信息。
容器安全服务的版本和使用情况,并提供升级、续费等功能。
主要功能
查看资产信息
1. 在安全概览页面,资产信息模块展示容器、镜像、集群、主机节点的资产数量信息。
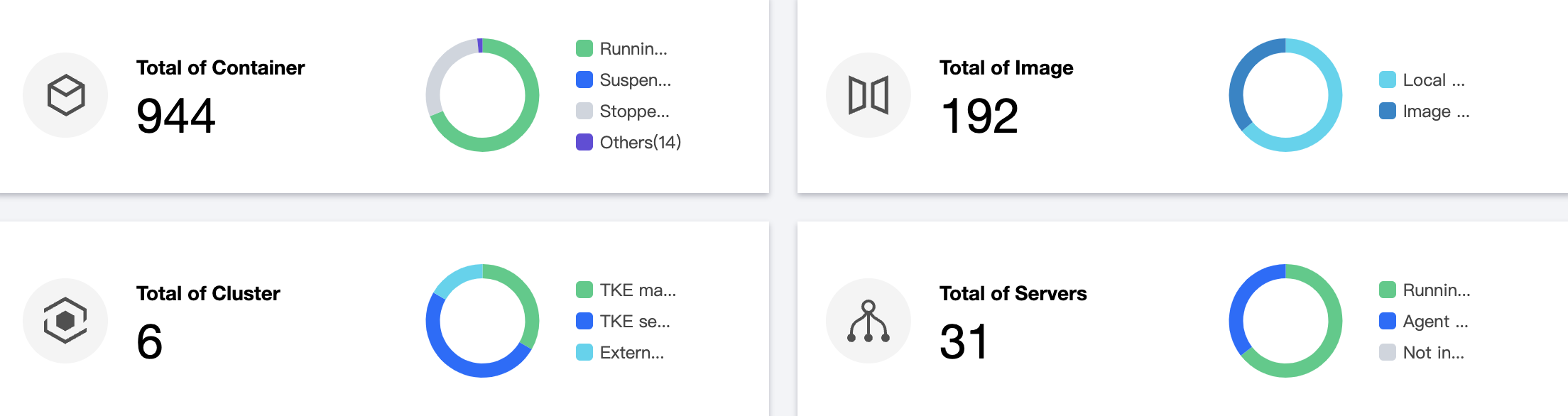

2. 在安全概览页面,单击“模块总数”,可跳转到资产管理的对应模块列表。
查看版本和使用情况,升级、续费
在安全概览页面,版本信息窗口展示当前容器安全服务版本信息和版本到期时间,以专业版为例具体信息如下:
若当前版本即将到期将提醒用户进行续费,用户可单击立即续费,进入续费页面完成续费。
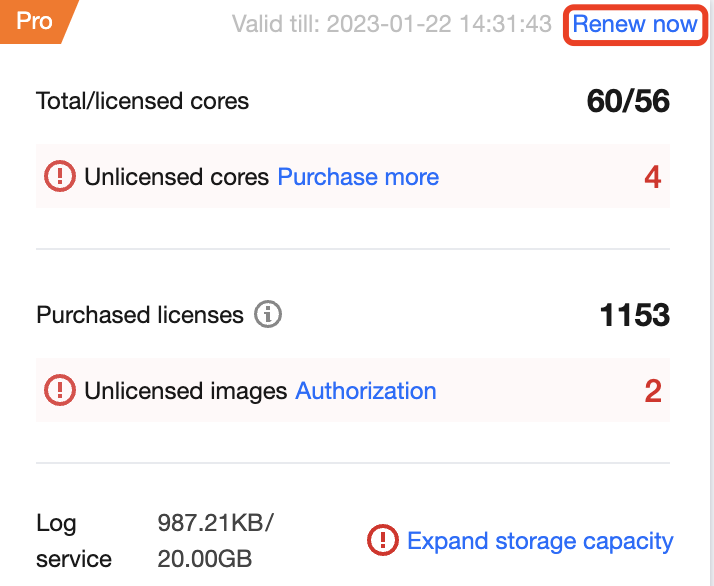

版本信息窗口同时展示当前用户的授权情况,包括总核数和授权核数、已购镜像授权。
总核数和授权核数:总核数是指用户业务节点的虚拟核数总和;授权核数是指用户开通专业版的核数。
说明:
当授权核数小于总核数时,将提示用户需补充购买的核数,用户可单击升级,进入购买页面购买授权。
当用户未补充购买所需授权核数时,将进入弹性计费模式,即超过授权核数将按0.25美元/核/天进行弹性计费。
已购镜像授权:用户已购买的镜像安全扫描数量。
说明:
当业务环境中存在未开启镜像安全扫描的本地镜像或仓库镜像时,将提示用户需补充购买的镜像授权数,用户可单击选购,进入购买页面购买授权。
镜像授权购买后,还需用户进入镜像安全>本地镜像/仓库镜像页面对授权进行配置,用户可自定义配置需开启安全扫描的镜像。
因产品调整,镜像授权于2023年12月29日-2024年03月31日暂停新购,已购用户仍可正常使用,给您带来不便,敬请谅解。
查看待处理安全事件
1. 在安全概览页面,待处理安全事件模块展示当前待处理的安全事件的数量。
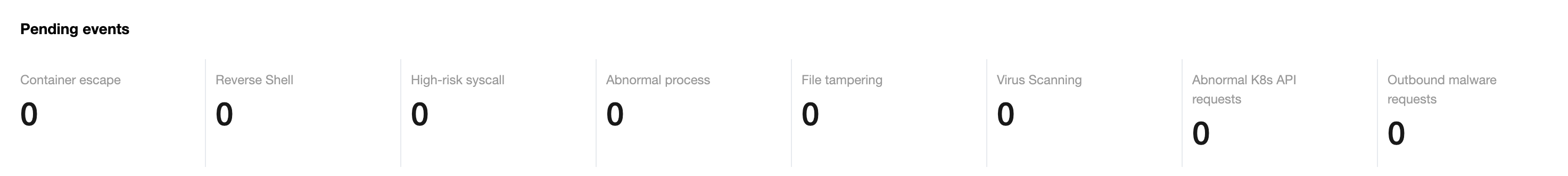

2. 在安全概览页面,单击“模块总数”,可进入到相应的安全事件页面查看详情并进行处理。
查看安全事件新增趋势
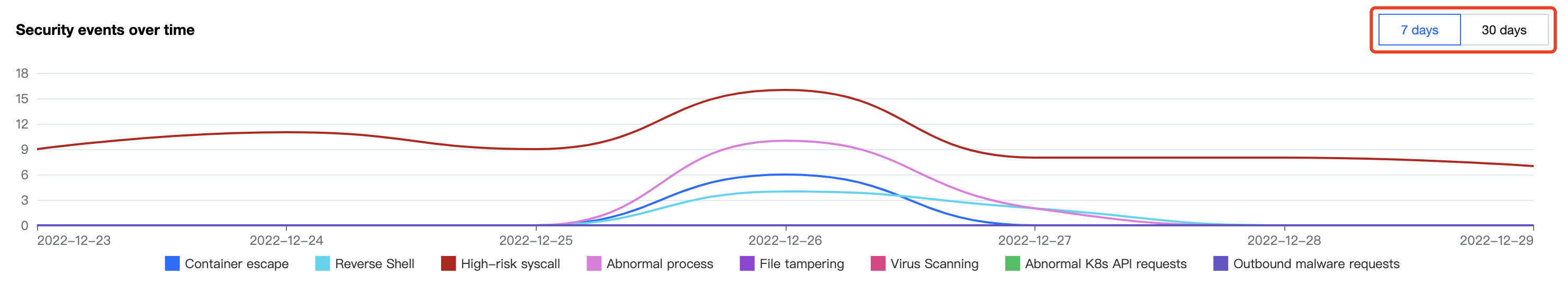
在安全概览页面,安全事件新增趋势模块展示7天或30天内运行时安全事件新增趋势。单击7天或30天可切换时间。

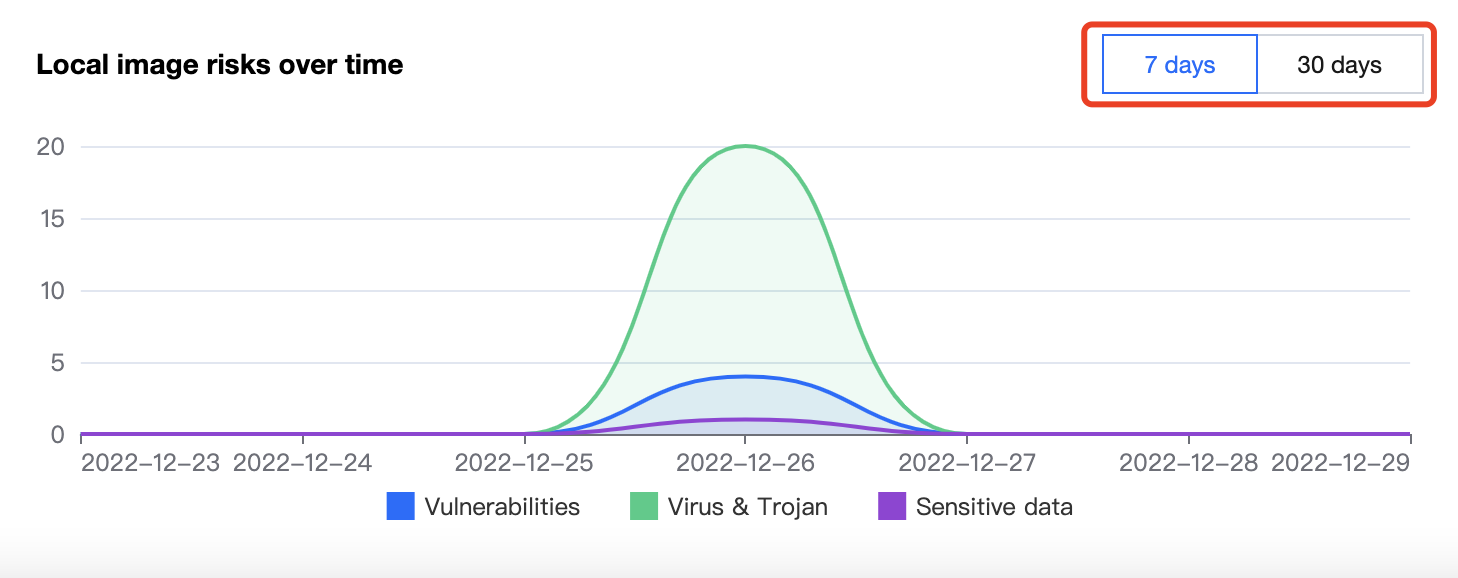
查看本地镜像新增风险趋势
在安全概览页面,展示7天或30天内本地镜像新增的安全漏洞、木马病毒、敏感信息数量趋势。单击7天或30天可切换时间。

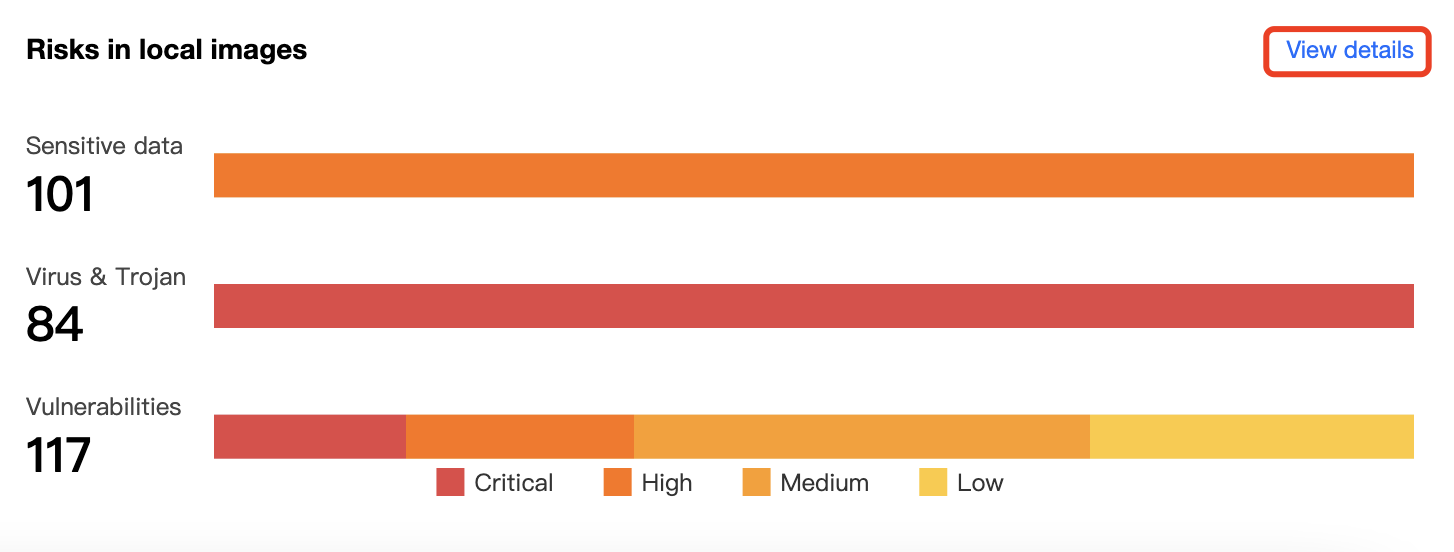
查看本地镜像风险详情
在安全概览页面,本地镜像风险详情模块展示当前镜像存在的敏感信息、木马病毒、安全漏洞的风险总数和威胁等级分布。单击查看详情,可进入镜像安全模块查看详情并进行处理。

文档反馈

