添加安全组规则
最后更新时间:2025-08-19 16:39:25
操作场景
安全组用于管理是否放行来自公网或者内网的访问请求。为安全起见,安全组入方向大多采取拒绝访问策略。如果您在创建安全组时选择了“放通全部端口”模板或者“放通22,80,443,3389端口和ICMP协议”模板,系统将会根据选择的模板类型给部分通信端口自动添加安全组规则。详情请参见 安全组概述。
本文指导您通过添加安全组规则,允许或禁止安全组内的边缘实例及资源对公网或私网的访问。
前提条件
您已经创建一个安全组。具体操作请参见 创建安全组。
您已经知道边缘实例需要允许或禁止哪些公网或内网的访问。更多安全组规则设置的相关应用案例,请参见 安全组应用案例。
操作步骤
1. 登录边缘计算机器控制台,选择左侧导航中的边缘网络 > 安全组。
2. 在安全组管理页面,选择需设置规则的安全组所在行右侧的修改规则。
3. 在安全组规则页签中,单击入站/出站规则,并根据实际需求选择以下任意一种方式完成操作。
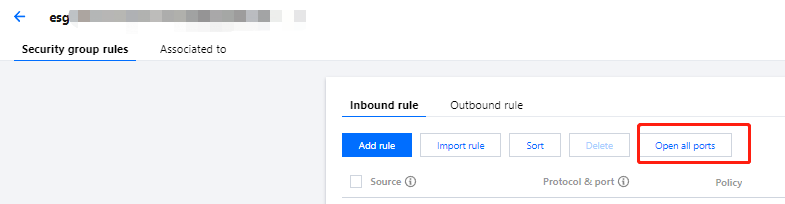
方式一:单击一键放通,并在弹出窗口中进行确认。此方式适用于无需设置 ICMP 协议规则,并通过22,3389,ICMP,80,443,20,21端口便能完成操作的场景。如下图所示:

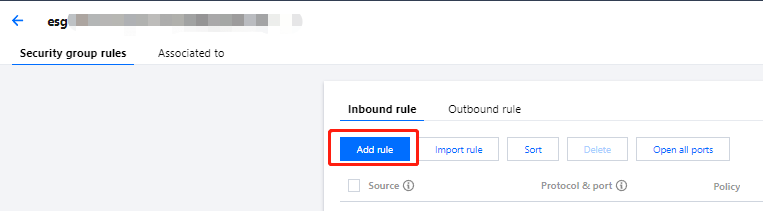
方式二:单击添加规则,并在弹出窗口中进行配置,详情请参见 步骤4。此方式适用于需要设置多种通信协议的场景,例如 ICMP 协议。如下图所示:

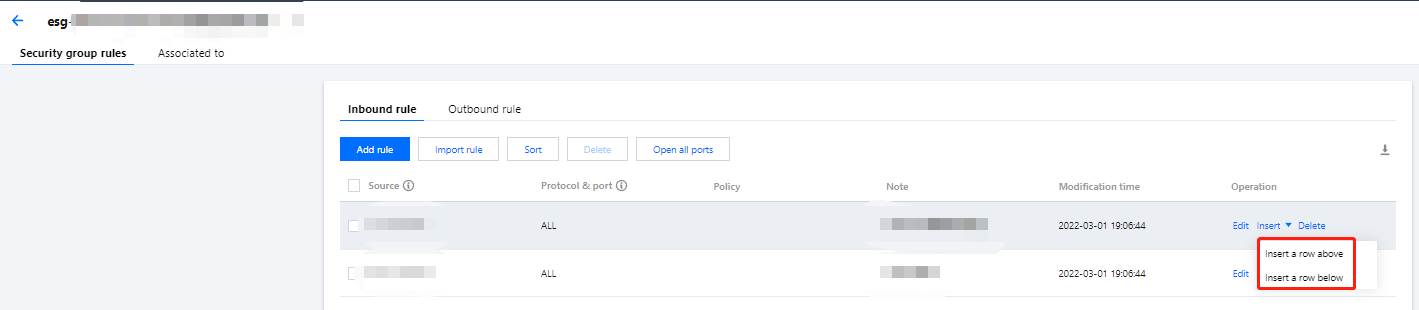
方式三:在安全组规则页面,可按需修改入站/出站规则。选择入站/出站规则页签,根据期望添加规则的位置,单击已有规则所在行右侧的插入 > 向上/向下插入一行,并参考 步骤4 快速配置规则。如下图所示:
4.
添加规则的主要参数如下:
类型:默认选择“自定义”,您也可以选择其他系统规则模板,例如 “Windows 登录”模板、“Linux 登录”模板、“Ping” 模板、HTTP(80)模板和 HTTPS(443)模板等。
来源:流量的源(入站规则) 或目标(出站规则),请指定以下选项:
指定的源/目标 | 说明 |
单个 IPv4 地址或 IPv4 地址范围 | 用 CIDR 表示法(如203.0.113.0、203.0.113.0/24或者0.0.0.0/0,其中0.0.0.0/0代表匹配所有 IPv4 地址)。 |
协议端口:填写协议类型和端口范围。例如,UDP:53、TCP:80,443。
策略:默认选择“允许”。
允许:放行该端口相应的访问请求。
拒绝:直接丢弃数据包,不返回任何回应信息。
备注:自定义,简短地描述规则,便于后期管理。
5.
单击完成,完成安全组入站规则的添加。
文档反馈

